I received a recent requirement to block access to all Microsoft 365/Office 365 applications, such as Exchange Online (Outlook email access), SharePoint Online, OneDrive, Microsoft Teams, and Microsoft Forms.
This includes both online and installed application access. Specific IT department developers use the target devices for this block. Since these are development machines, they don’t need to use Office 365 applications.
It’s worth mentioning that the developer devices follow a specific naming convention, such as having “Win10” in their names. We’ll explore how to create a Conditional Access (CA) Policy and apply it to these specific devices. Conditional Access Policies can target devices based on filters available under any CA policy’s “Conditions” section.
Create an Entra ID Conditional Access (CA) Policy
- Sign in to the Entra admin center.
- Search for Microsoft Entra Conditional Access and click on New Policy to create a new CA policy.

- When you select Create a new policy, you must configure the policy using the following settings: I’ll provide the options you need to configure, while the remaining settings should be set to not configured.
- Provide a Name to the CA policy. For example, Block Office365 apps on Developer Devices.
Users
- Users: Select All Users under Include.
Target resources
- Select apps under Include
Choose all the apps you wish to block, such as Office 365 Exchange Online, Office 365 SharePoint Online, Office 365 Yammer, Microsoft Teams, etc. Alternatively, you can add “Office 365” to block all Office 365 applications. The provided screenshot illustrates adding individual apps that I wanted to block.

Conditions
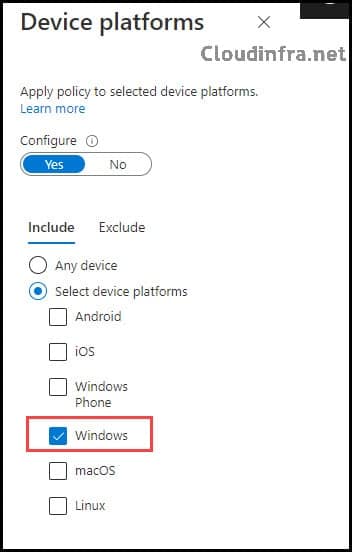
- Device Platforms: Toggle the Configure switch to Yes and click on Select device platforms. Select Windows.
Client Apps
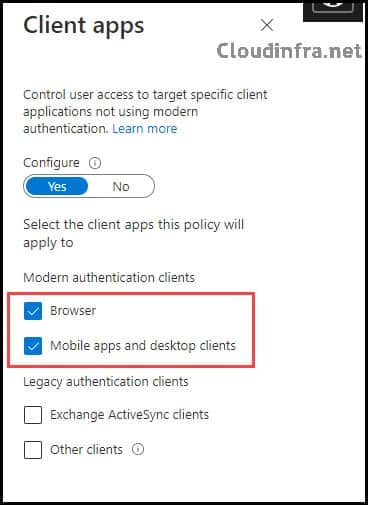
- Toggle the Configure switch to Yes, then Select Browser, Mobile Apps, and Desktop Clients.
Client Apps
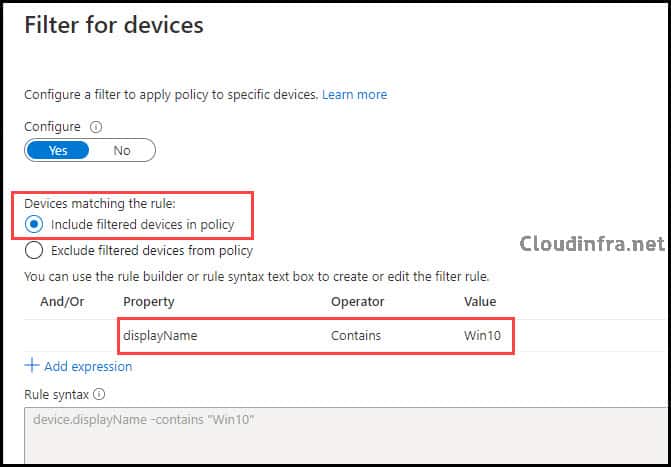
- Click on Filter for devices and toggle the Configure switch to Yes.
- Select Include filtered devices in the policy.
To filter the devices and apply this policy only to machines with “Win10” in their name, create a rule using the query: “device.displayName -contains ‘Win10‘.” This way, the policy will specifically target devices with “Win10” in their display name.
Access Controls
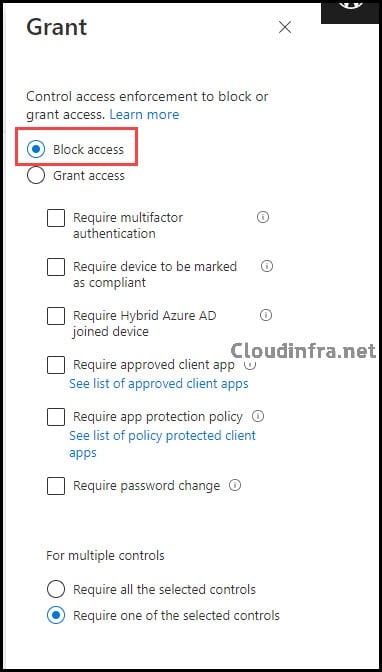
Grant
Under the “Grant” access control configuration, select “Block access” to prevent access to Office 365 from the machines. Since the policy has been applied to all users, anyone using machines with “Win10” in their name will be blocked from accessing any Office 365 apps included in this CA policy. Access to these apps via web browsers or installed clients is impossible.
End-user Experience
Now, let’s test our policy on one of my test machines, which has “Win10” in its name. The computer is named “AdeleV-Win10,” so I should not be granted access to any Office 365 app from this PC.
Below is the screenshot from my test PC.
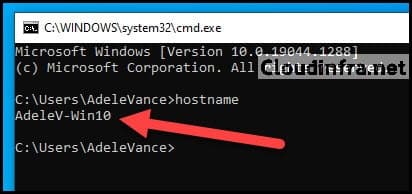
Test 1: Access to Microsoft Teams App
The error message displayed when attempting to access the Microsoft Teams app results from the Conditional Access Policy we recently implemented.
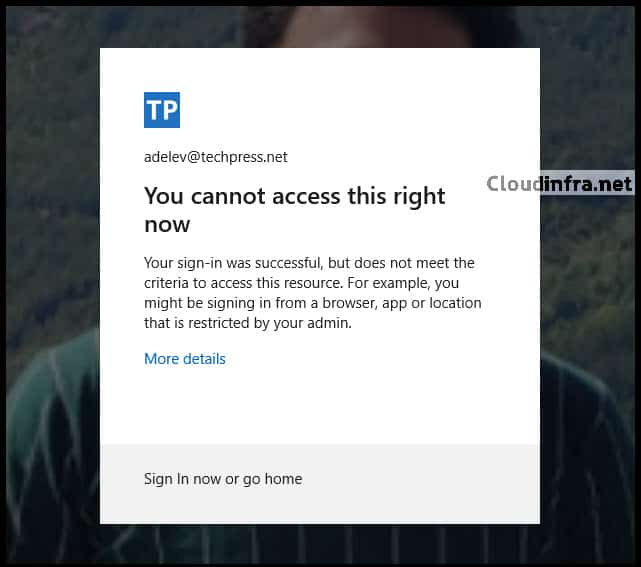
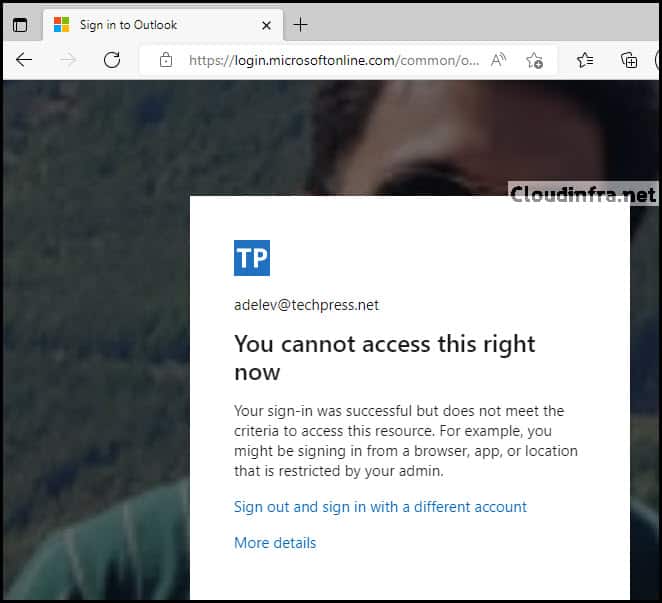
Test 2: Access to Microsoft Exchange Online Web App
Access to the Outlook Online version has been blocked as well with the error message:
Your sign-in was successful but does not meet the criteria for accessing this resource. For example, you might be signing in from a browser, app, or location restricted by your admin.
Wrapping up
In summary, Conditional Access is a powerful tool for enhancing the security of your Microsoft 365 and Azure environment. Device filters allow you to fine-tune policies to specific device types, and numerous other conditions and filters are available to ensure policies are precisely targeted. In this blog post, we learned how to block access to Office 365 apps from specific devices using a Conditional Access policy.
