In this blog post, I will show you the steps to connect Microsoft 365 with defender for cloud apps. Microsoft Defender for cloud apps is now part of Microsoft 365 Defender. Instead of managing it from a separate portal, it can now be managed from the Microsoft 365 Defender portal. You can learn more about the transition from this link.
In this article, we will look into the Initial setup of Microsoft Defender for Cloud Apps (Previously Microsoft Cloud App Security), Connect Microsoft 365 App connector with Microsoft Defender for Cloud apps, and Configure its basic settings. We will also create a policy to Block Downloads while using Microsoft 365 Apps from a non-compliant/Unmanaged device.
Contents
What is Microsoft Defender for Cloud Apps (MDCA)
Microsoft Defender for Cloud Apps (MDCA) is a cloud access security broker (CASB) that provides rich visibility and control over data travel, including log collection, API connectors, and reverse proxy. It provides visibility and insight into the apps and native integration with Microsoft Solutions.
You can connect it to Microsoft or a third-party app to gather logs and analyze data to protect the organization against cyber threats. In the next section of this blog post, we will see how to connect Microsoft 365 with Defender for Cloud Apps.
Connect Microsoft 365 with Defender for Cloud Apps (MDCA)
Let’s check the steps to connect the Microsoft 365 App with MDCA. We will be using the Microsoft 365 Defender portal to create this connection instead of the Microsoft Defender for Cloud Apps portal because the Microsoft Defender for Cloud Apps portal is being transitioned or moved to a centralized Microsoft 365 Defender portal.
Microsoft 365 Defender will be the home for monitoring and managing security across your Microsoft identities, data, devices, apps, and infrastructure, including Defender for cloud apps.
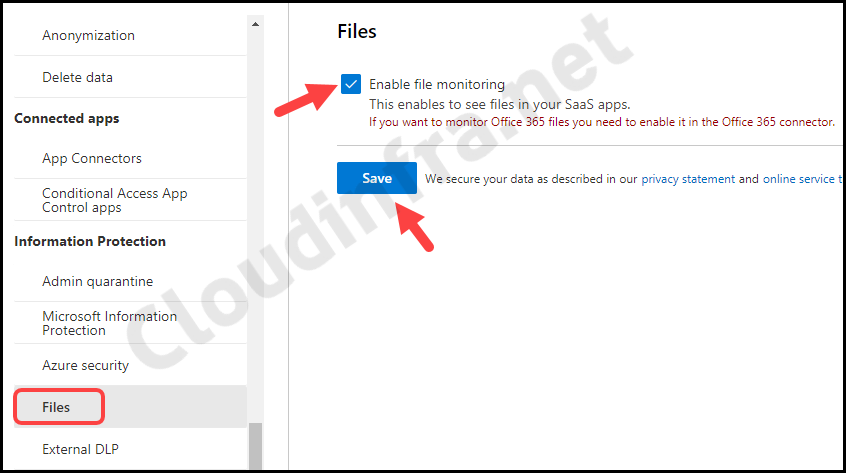
Before we create a connection between the Microsoft 365 app and Microsoft Defender for Cloud Apps (MDCA). We will enable file monitoring for Microsoft 365 services from the Microsoft 365 Defender portal. Let’s check the steps:
1. Enable file monitoring
Please follow below steps to Enable File monitoring on the Defender portal:
- Sign in to the Microsoft 365 Defender portal as Security admin/Global admin.
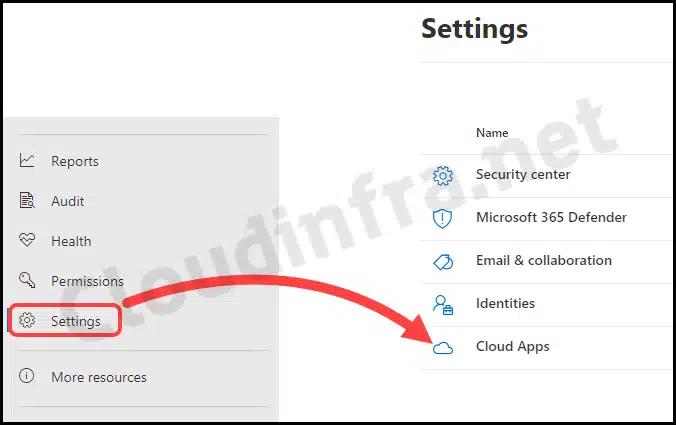
- Scroll down on the portal to find Settings > Cloud Apps.
- Scroll down to Information Protection > Files.
- Enable the checkbox Enable file monitoring and click on Save.
2. Connect Microsoft 365 App with Defender for Cloud Apps
After we have enabled File monitoring for Microsoft 365. The next step is to Connect Microsoft 365 application with Defender for Cloud Apps. We will use Microsoft 365 Defender portal to create this connection.
- Sign in to the Microsoft 365 Defender portal as Security Admin/Global Admin.
- Scroll down on the portal to find Settings > Cloud Apps.
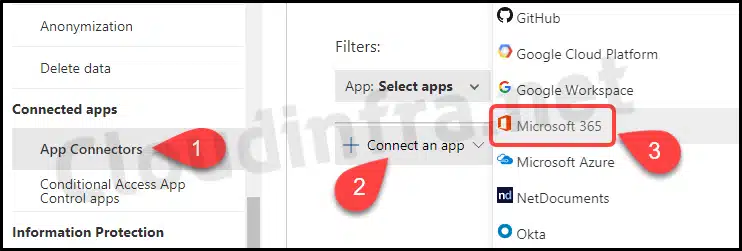
- Scroll down on the page to find App Connectors option under Connected apps.
- Click on App Connectors > + Connect an app > Microsoft 365.
| App Connector |
|---|
| The app connector communicates with the apps using the application provider’s APIs. APIs provide MDCA with great visibility and control over the connected applications. All communication between MDCA and connected apps is encrypted using the HTTPS protocol. |
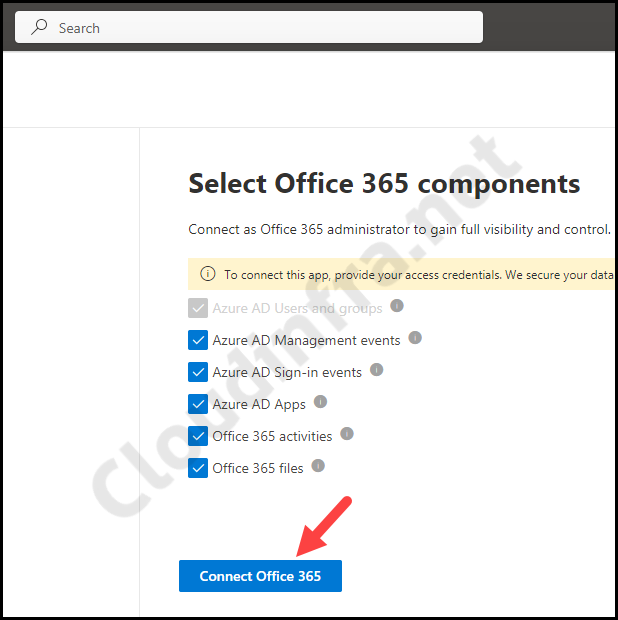
- Select all below events/services for monitoring
- Azure AD Management events
- Azure AD Sign-in events
- Azure AD Apps
- Office 365 activities
- Office 365 files
- Click on Connect Microsoft 365/Office 365 to create this connection.
- A Microsoft 365 / Office 365 connection has been created. Click on Done to proceed.
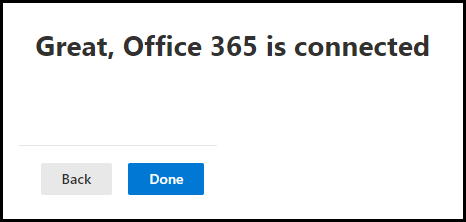
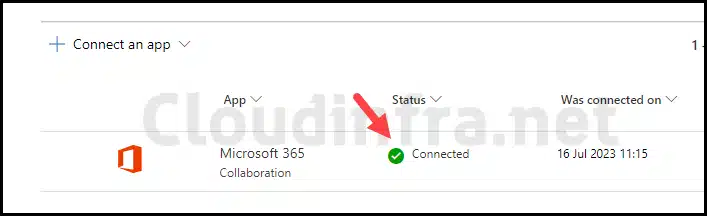
- Microsoft 365 Status will show as Connected after a few minutes.
Configure Integration of Defender for Cloud Apps with Entra ID
After you have created a connection with Microsoft 365 and Defender for Cloud apps, You can also integrate Entra ID. Please refer to the blog post: Setup Integration of Defender for Cloud Apps with Entra ID.
Conclusion
In this blog post, we have seen how to connect Microsoft 365 and Defender for Cloud apps. However, you can do much more with Microsoft Defender for cloud apps, from creating policies to block the download of data on non-compliant devices to monitoring and analyzing user traffic to Microsoft 365 services.
