In this blog post, we will explore in detail about Intune management extension (IME) log files. The Intune Management Extension (IME) is an agent/service that is automatically installed on Windows 10/11 devices when you deploy a PowerShell script, Win32 app, Microsoft Store apps, custom compliance policy, or a remediation script. Whenever you take any of these actions, IME will be installed on the target device. Just ensure that the IME prerequisites are met.
Script execution, app installation, and monitoring on the client device are primarily handled by the Intune Management Extension (IME). All events related to these processes are logged in different text files stored on the device.
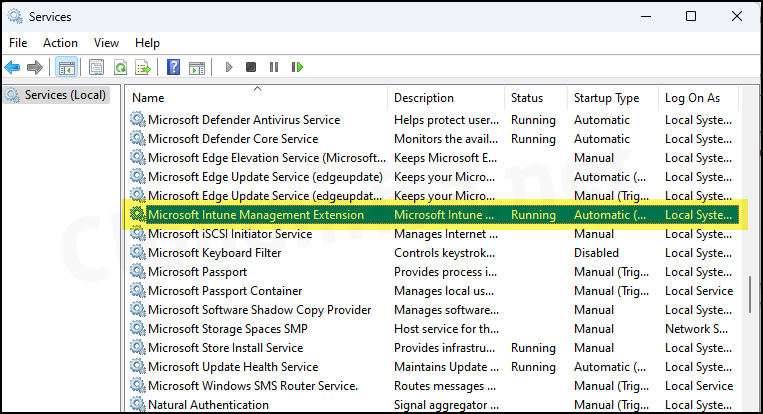
Once Microsoft Intune Management Extension is installed, it runs as a service on the client device. Ensure that the service is in a running state.
Contents
Finding Intune Management Extension logs
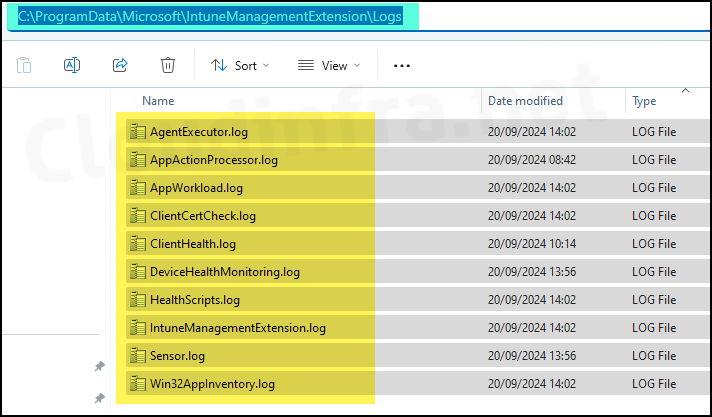
Intune Management Extension log files are stored in the C:\ProgramData\Microsoft\IntuneManagementExtension\Logs folder. Microsoft has introduced new log files, such as AppWorkload.log and ClientCertCheck.log, to help with troubleshooting issues. The screenshot below shows all the files created under the Logs folder.
Best Way to Read Intune Management Extension Logs
You can use CMTrace.exe tool to read log files, It formats the logs in a much more readable way, making it easier to troubleshoot issues.
Different ways to access IME Log files
If you have access to the client device, you can view the IME log files by navigating to C:\ProgramData\Microsoft\IntuneManagementExtension\Logs.
If you don’t have access to the client device, you can collect the logs remotely by signing into the Intune admin center:
- Go to Devices > All Devices > select the device.
- On the top menu bar, click Collect diagnostics.
Maximum Size of IME Log files
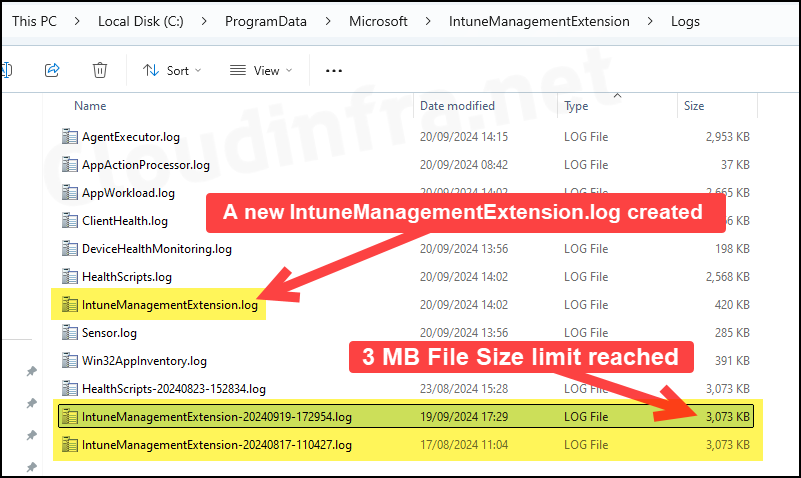
Intune Management Extension log files have a maximum size limit of 3 MB. Once this limit is reached, the file is renamed, and a new log file is generated.
Intune Management Extension log Files
Let’s dive into the details of each log file, starting with the list of files created in the Logs folder. In total, I found 10 log files.
- AgentExecutor.log
- AppActionProcessor.log
- AppWorkload.log
- ClientHealth.log
- ClientCertCheck.log
- DeviceHealthMonitoring.log
- HealthScripts.log
- IntuneManagementExtension.log
- Sensor.log
- Win32AppInventory.log
1. AgentExecutor.log
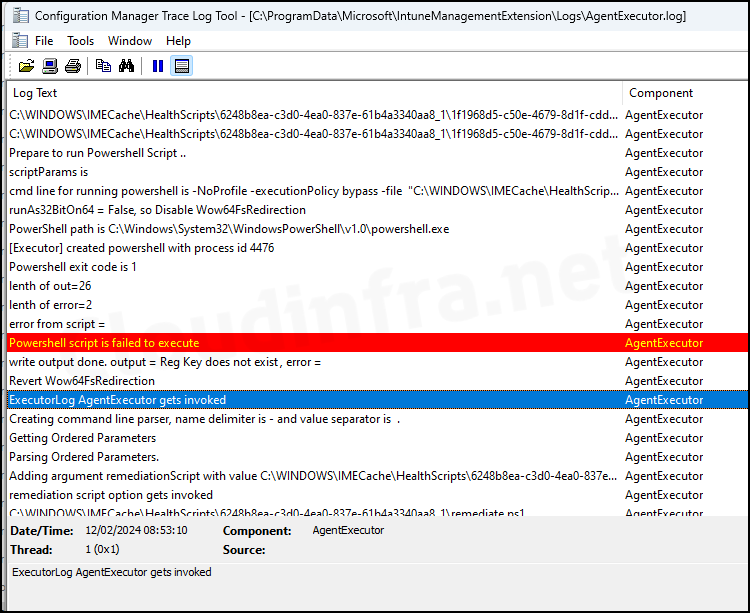
AgentExecutor.exe is located in C:\Program Files (x86)\Microsoft Intune Management Extension. If you’ve created any Intune remediation tasks or targeted a PowerShell script to a device, AgentExecutor.exe will be invoked, and its actions will be logged in the AgentExecutor.log file.
Intune remediation scripts are cached in C:\WINDOWS\IMECache\HealthScripts\ under their respective deployment IDs. You can track the execution status and other related activities in the AgentExecutor.log file.
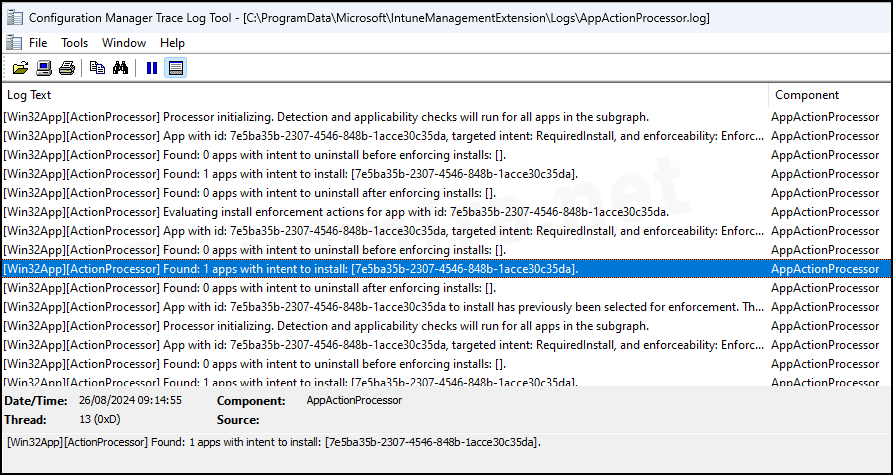
2. AppActionProcessor.log
The AppActionProcessor.log file contains information about applications with an intent to install or uninstall. The Action Processor also performs detection and app applicability checks for all apps.
3. AppWorkload.log
This log file was introduced recently with Intune Service release 2408. To make troubleshooting Win32 app deployments easier, logs related to these deployments are now logged in the AppWorkload.log file, instead of the IntuneManagementExtension.log file as it was done previously. For detailed information about the AppWorkload.log file, please refer to the link: About AppWorkload.log Intune Log File.
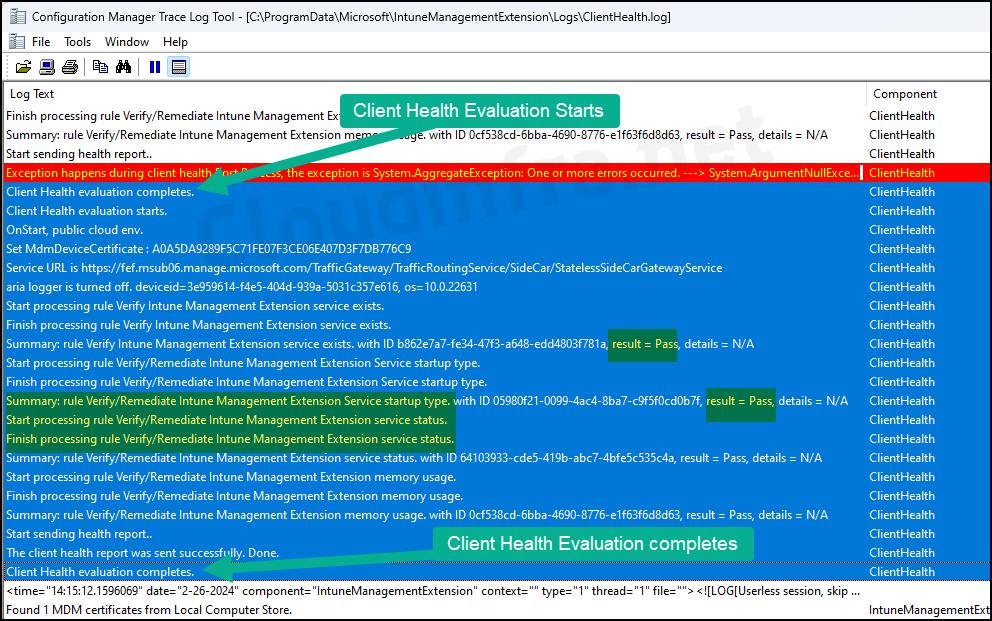
4. ClientHealth.log
The log file for tracking the health of the Intune Management Extension agent/service regularly records the Client Health evaluation process on the client device. As shown in the screenshot below, this evaluation starts at regular intervals and sends the health report back to the Intune service.
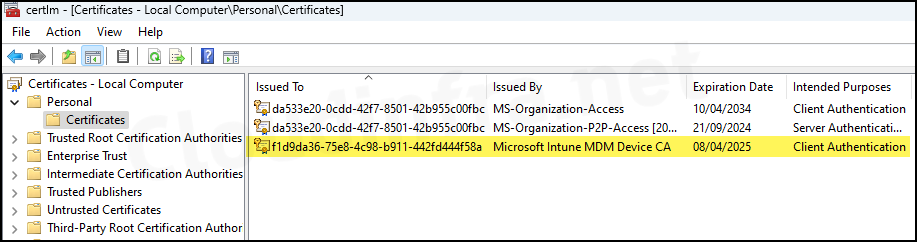
5. ClientCertCheck.log
The ClientCertCheck.exe file, located in C:\Program Files (x86)\Microsoft Intune Management Extension, regularly checks and verifies that the MDM certificates are installed correctly on the device.
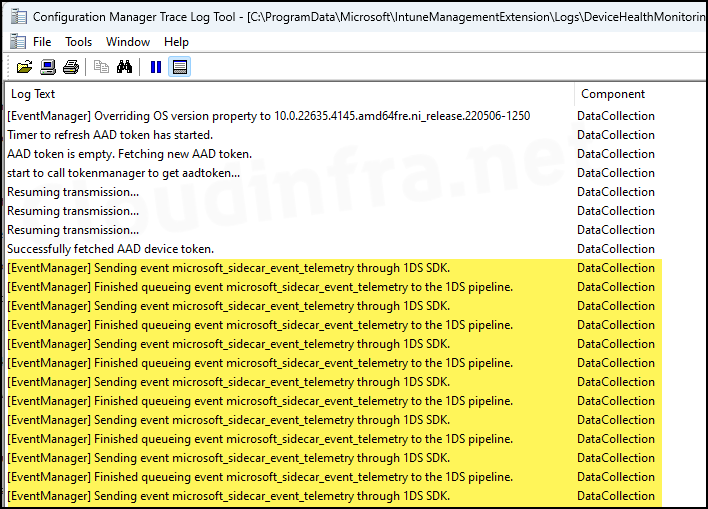
6. DeviceHealthMonitoring.log
Telemetry in Windows 10/11 automatically collects and sends system usage information to Microsoft. The DeviceHealthMonitoring.log file logs events related to this data collection. It uses the 1DS SDK, which is Microsoft’s first-party open-source logging library designed for handling text-based events and sending data to public-facing endpoints.
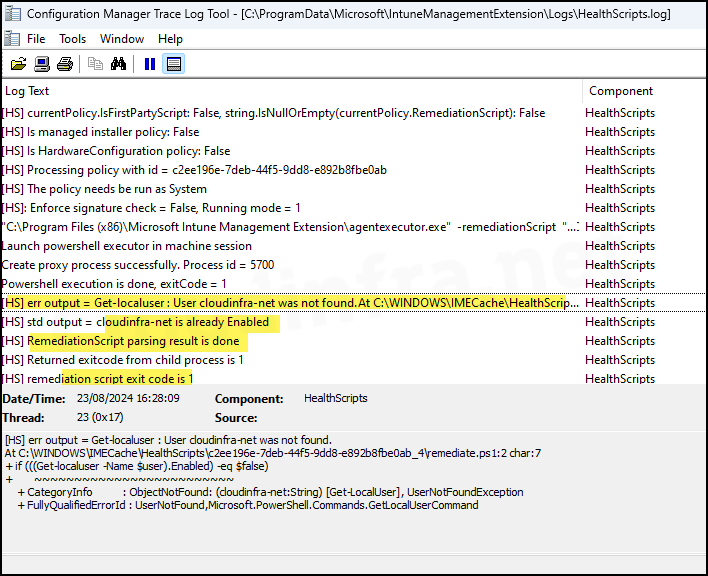
7. HealthScripts.log
HealthScripts component of the Intune Management Extension checks for any assigned Intune detection and remediation scripts on the device and executes them according to their schedule. Logs for these actions are generated and updated in the HealthScripts.log file, which also contains exit codes generated by the detection and remediation scripts.
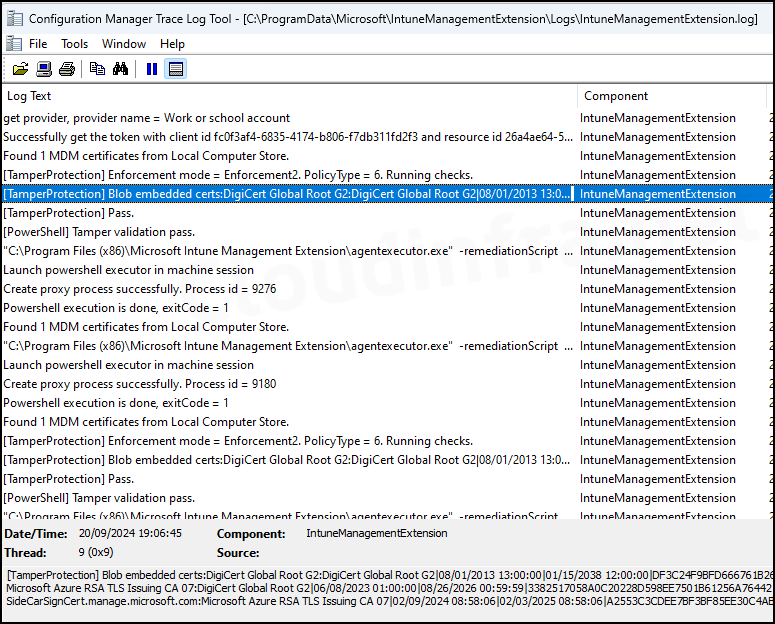
8. IntuneManagementExtension.log
When troubleshooting issues related to any policy, Intune device check-ins, Intune remediations, or errors associated with any IME component, the relevant information will be logged in this file.
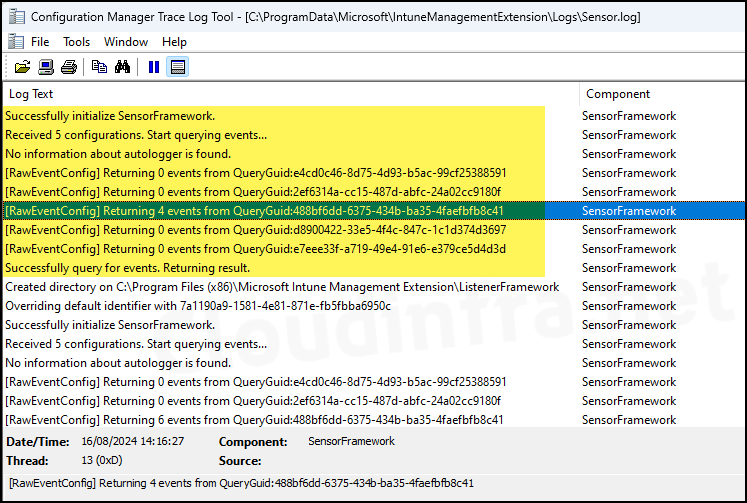
9. Sensor.log
Microsoft.ConfigurationManagement.SensorFramework.dll provides various information about device usage and events. However, for troubleshooting app deployment or device check-in issues, this file may not be particularly helpful. You can still open the file and review its contents. Below is a snippet of this log file for reference.
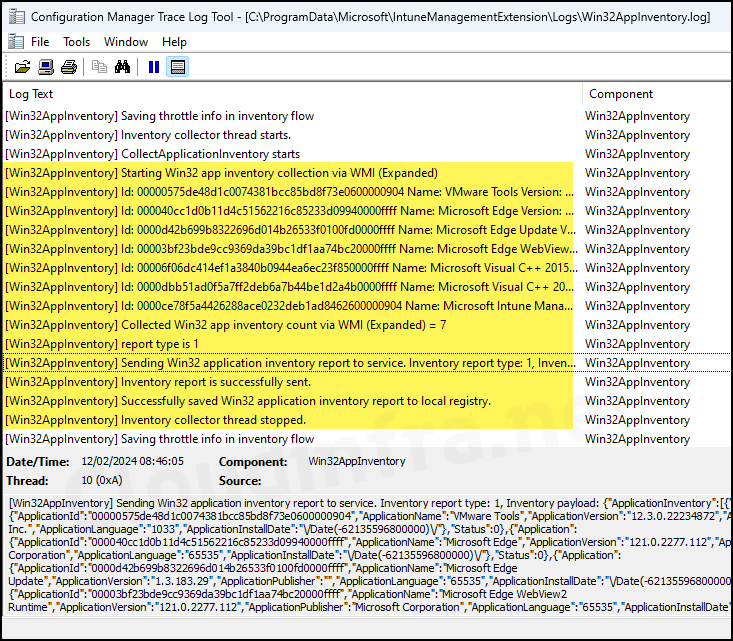
10. Win32AppInventory.log
This log file records events related to the collection of Win32 app inventory via WMI and sends the report to the Intune service. Additionally, it saves the report to the local registry.
Conclusion
In summary, the Intune Management Extension (IME) plays a critical role in managing and troubleshooting Win32 app deployments and device health within the Intune ecosystem. With various log files, such as AppWorkload.log, AgentExecutor.log, HealthScripts.log, and DeviceHealthMonitoring.log, administrators can effectively monitor application installations, script executions, and device health evaluations. The introduction of new log files and tools like CMTrace.exe enhances the troubleshooting process, allowing for easier identification of issues related to app deployment, device check-ins, and MDM certificate verification.
