In this post, I will show you how to add a group tag to Autopilot devices using PowerShell. Group tags are one of the most effective ways to segment Windows Autopilot devices and drive clean targeting for Autopilot deployment profiles, ESP, apps, and policies. A group tag set in Intune maps to the OrderID attribute on the Microsoft Entra device object, which is why you can build dynamic device groups based on [OrderID]:<GroupTag>.
The dynamic query to group all Autopilot devices is:
(device.devicePhysicalIds -any (_ -startsWith "[ZTDid]"))Using dynamic device membership queries, you can also create groups that target autopilot devices with a specific group tag or order ID. In this example, cloudinfra-device represents the group tag assigned to the autopilot devices.
Dynamic device membership query for Group tag: cloudinfra-device
(device.devicePhysicalIds -any (_ -eq "[OrderID]:cloudinfra-device"))Contents
AutoPilot Group Tag Use Case
When multiple partner companies share a single Microsoft 365 tenant to manage users, apps, and devices in Intune, device targeting can quickly become complex. To understand autopilot group tag usage, let’s take an example: A tenant named cloudinfra-m365-tenant is shared by partner1, partner2, partner3, and others. All partners enroll devices using Windows Autopilot and add them into a single Entra dynamic device group called Win-Org-All-Autopilot-Devices.
All partners in the tenant enroll their devices into Intune using autopilot and place them in a group called Win-Org-All-Autopilot-Devices using dynamic device membership rules (device.devicePhysicalIDs -any (_ -contains “[ZTDID]”)). This approach allows Win-Org-All-Autopilot-Devices group to include Autopilot devices from all partners. As a result, any policies, apps, or configurations deployed to this group will apply to every partner’s devices.
To keep deployments scoped correctly, assign a unique group tag per organization and create separate Entra dynamic device groups per partner using the tag. Autopilot devices can be grouped using devicePhysicalIds values like OrderID (Group Tag), which is why the query format is [OrderID]:<tag>. You can still keep Win-Org-All-Autopilot-Devices for reporting purposes but only use partner-specific Entra groups when assigning profiles and apps to prevent cross-partner impact.
Below table shows an example of multiple partners using the same Intune tenant, with their respective group tags assigned to their devices.
| Organization Name | Group Tag |
|---|---|
| cloudinfra-m365-tenant | cloudinfra-device |
| Partner1 | partner1-device |
| Partner2 | partner2-device |
| Partner3 | partner3-device |
Accordingly, Entra dynamic device security groups are created for each partner to group the devices based on their group tag.
| Organization Name | Dynamic Group Membership Query | Dynamic Group Membership Query |
|---|---|---|
| cloudinfra-m365-tenant | cloudinfra-autopilot-devices | (device.devicePhysicalIds -any (_ -eq “[OrderID]:cloudinfra-device”)) |
| Partner1 | partner1-autopilot-devices | (device.devicePhysicalIds -any (_ -eq “[OrderID]:partner1-device”)) |
| Partner2 | partner2-autopilot-devices | (device.devicePhysicalIds -any (_ -eq “[OrderID]:partner2-device”)) |
| Partner3 | partner3-autopilot-devices | (device.devicePhysicalIds -any (_ -eq “[OrderID]:partner3-device”)) |
Method 1: Add a Group Tag to an Autopilot Device Manually
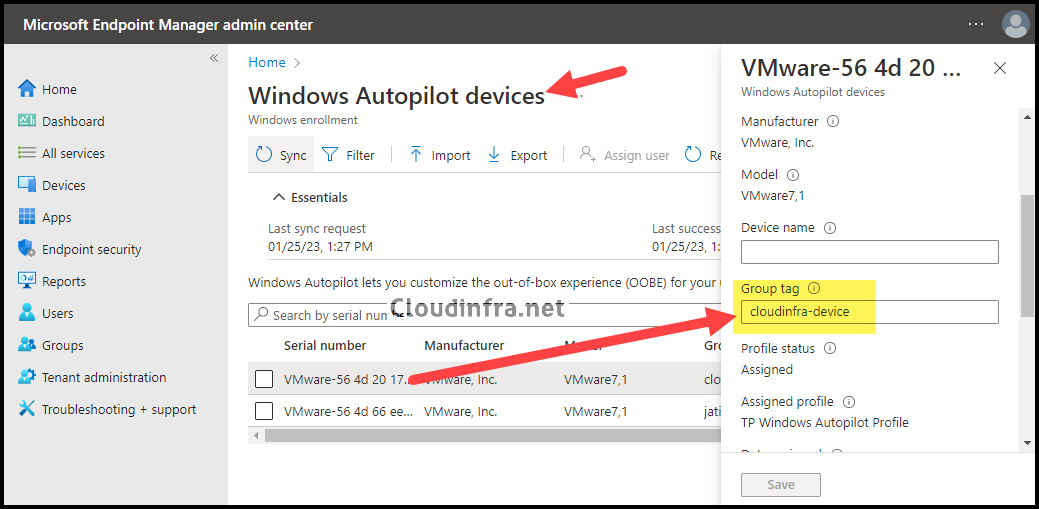
Let’s first understand how to add a group tag to an autopilot device manually from Intune admin center. In the next section, I will show you how to add a group tag to one autopilot device and multiple autopilot devices using PowerShell.
- Go to Intune admin center > Devices > Enrollment.
- Under the Windows tab, click on Devices under Windows Autopilot category.
- Find a device you want to apply a group tag to and click on it.
- Find the Group tag field, type the name of a group tag, and Save.
- Repeat the process to add a group tag for the rest of the devices.
If you have created a dynamic Entra security group based on the group tag, it may take some time to update the Entra ID dynamic group membership. You can check back later and refresh the Entra group to see if the device has been added to the appropriate dynamic group.
Method 2: Add a Group Tag to Autopilot Devices Using PowerShell
Follow below steps to add a group tag to autopilot devices using PowerShell.
Add a Group Tag to One Autopilot Device Using PowerShell
Let’s first look at how to add a group tag to a single Autopilot device using PowerShell. For this task, you will need the Microsoft Graph PowerShell module. You can either install the complete Microsoft Graph module or install only the required submodule as shown below. Open the PowerShell console and run below commands:
Install Microsoft.Graph.DeviceManagement.Enrollment PowerShell module
Install-Module Microsoft.Graph.DeviceManagement.Enrollment -Scope CurrentUser -ForceImport Microsoft.Graph.DeviceManagement.Enrollment PowerShell module
Import-Module Microsoft.Graph.DeviceManagement.EnrollmentConnect to Graph with required scopes
Connect-MgGraph -Scopes "DeviceManagementServiceConfig.ReadWrite.All"After establishing a connection to Microsoft Graph with the required scopes, use below script to update the group tag on a single Autopilot device. This is an example script; update the values for $serialnumber and $grouptag variables before executing.
Update Group tag on a given autopilot device (example)
$SerialNumber = "VMware-56 4d 1a 20 ef fe a5 01-24 01 4c ff 8f 2a 3c 82"
$GroupTag = "cloudinfra-device"
$device = Get-MgDeviceManagementWindowsAutopilotDeviceIdentity -All | Where-Object { $_.SerialNumber -eq $SerialNumber } | Select-Object -First 1
if (-not $device) {
throw "Autopilot device not found for SerialNumber: $SerialNumber"
}
Update-MgDeviceManagementWindowsAutopilotDeviceIdentityDeviceProperty -WindowsAutopilotDeviceIdentityId $device.Id -GroupTag $GroupTag
Once the group tag is applied, use below command to verify:
Verify Group tag
Get-MgDeviceManagementWindowsAutopilotDeviceIdentity -WindowsAutopilotDeviceIdentityId $device.Id | fl Id, SerialNumber, DisplayName, GroupTag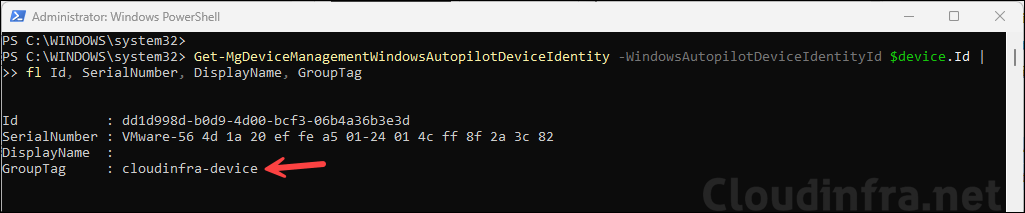
Add a Group Tag to All Autopilot Devices Using PowerShell
Let’s see how to add a group tag to a list of Autopilot devices using PowerShell. In this approach, you export the device IDs of all Autopilot devices to a text file and then use that file to apply the group tag. Remove any device IDs from the file you do not want to apply the tag to, or if you want to apply a different tag.
Below steps will require a connection to Microsoft Graph. If you are already connected, you can skip the connection step. Otherwise, install the required module first.
Install Microsoft.Graph.DeviceManagement.Enrollment PowerShell module
Install-Module Microsoft.Graph.DeviceManagement.Enrollment -Scope CurrentUser -ForceImport Microsoft.Graph.DeviceManagement.Enrollment PowerShell module
Import-Module Microsoft.Graph.DeviceManagement.EnrollmentConnect to Graph with required scopes
Connect-MgGraph -Scopes "DeviceManagementServiceConfig.ReadWrite.All"Fetch all Autopilot device IDs in a txt file
Get-MgDeviceManagementWindowsAutopilotDeviceIdentity -All | Select-Object -ExpandProperty Id | Out-File C:\Temp\AutopilotDeviceIDlist.txt -Encoding utf8
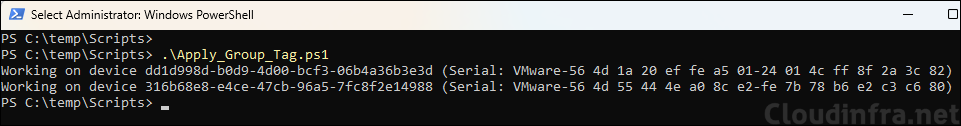
Copy the PowerShell code below and paste it into Notepad, then save the file with a .ps1 extension. Update the group tag and the file path C:\Temp\AutopilotDeviceIDlist.txt if required. After that, run the script. It will apply the specified group tag to all Autopilot devices listed in the AutopilotDeviceIDlist.txt file.
Apply_Group_Tag.ps1
# Provide a Group Tag
$GroupTag = "cloudinfra-device"
# Get the IDs in a variable $DeviceIDs
$DeviceIDs = Get-Content "C:\Temp\AutopilotDeviceIDlist.txt"
foreach ($deviceID in $DeviceIDs) {
try {
$currentdevice = Get-MgDeviceManagementWindowsAutopilotDeviceIdentity -WindowsAutopilotDeviceIdentityId $deviceID -ErrorAction Stop
Write-Host "Working on device $deviceID (Serial: $($currentdevice.SerialNumber))"
Update-MgDeviceManagementWindowsAutopilotDeviceIdentityDeviceProperty -WindowsAutopilotDeviceIdentityId $deviceID -GroupTag $GroupTag -ErrorAction Stop
}
catch {
Write-Warning "Failed on deviceId $deviceID. $($_.Exception.Message)"
}
}
Verify Group tag on Autopilot devices
Run below command to get the list of all autopilot devices with group tag information. Check and confirm if the group tag was applied successfully.
Get-MgDeviceManagementWindowsAutopilotDeviceIdentity -All | Select-Object Id, SerialNumber, DisplayName, GroupTag | Format-Table -AutoSizeExport the list of All Autopilot devices with Group tag
You can also export the list of autopilot devices with group tag information. Simply modify above command and use Export-CSV cmdlet to export the information to a CSV file.
Get-MgDeviceManagementWindowsAutopilotDeviceIdentity -All | Select-Object Id, SerialNumber, DisplayName, GroupTag | Export-Csv C:\Temp\AutopilotDeviceInfo_GroupTag.csv -NoTypeInformation -Encoding UTF8Remove a Group tag from Autopilot devices using PowerShell
You can also sign into the Intune admin center and remove the group tag assigned to the devices manually. But it will be much quicker to use PowerShell for this task. Let’s take a look:
First, export the list of device IDs to a text file. Open the file, remove the device IDs for which you do not want to clear the group tag, and then save the file.
Fetch all Autopilot device IDs in a txt file
Get-MgDeviceManagementWindowsAutopilotDeviceIdentity -All | Select-Object -ExpandProperty Id | Out-File C:\Temp\AutopilotDeviceIDlist.txt -Encoding utf8Use the PowerShell script below to clear the group tag for all devices listed in the C:\Temp\AutopilotDeviceIDlist.txt file.
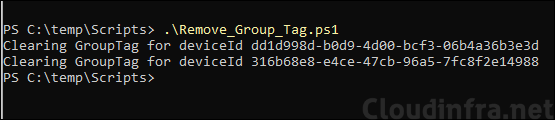
Clear group tag for all devices in the AutopilotDeviceIDlist.txt
$GroupTag = ""
$DeviceIDs = Get-Content "C:\Temp\AutopilotDeviceIDlist.txt"
foreach ($deviceID in $DeviceIDs) {
try {
Write-Host "Clearing GroupTag for deviceId $deviceID"
Update-MgDeviceManagementWindowsAutopilotDeviceIdentityDeviceProperty `
-WindowsAutopilotDeviceIdentityId $deviceID `
-GroupTag $GroupTag `
-ErrorAction Stop
}
catch {
Write-Warning "Failed on deviceId $deviceID. $($_.Exception.Message)"
}
}

how to upload hardware hash vai Microsoft graph and without entering intune administrator credentials
You have to create app registration
Thanks LiamJ74,
@unknownuser231: To create an Intune app registration, refer to the link: https://cloudinfra.net/how-to-force-intune-sync-using-powershell/#c
Two questions:
1) Is there a limit to the number of group tags per Device?
2) Is there any best practice to the total number of Intune group tags an organization may have?
An important question is, how does one limit Partner1 from updating the group tag on Autopilot devices belonging to Partner2 and Partner3? Autopilot devices appear to not utilize scope tags in Intune.