In this blog post, I will show you the steps to delete Windows Hello for Business registrations using Intune. Windows Hello for Business (WHfB) is a secure authentication method that utilizes biometrics (face/fingerprint) or a PIN for user authentication. You may have completely disabled WHfB in your organization, but you also want to Delete Windows Hello for Business registration from the device.
A Windows Hello for Business (WHfB) container is a logical grouping that stores the user’s keys, certificates, and credentials managed by Windows Hello.
You can remove the Windows Hello for Business container on a Windows 10/11 device using a straightforward command: certutil.exe -deleteHelloContainer which needs to be run under the user context. Open a command prompt and execute this command. After that, restart your device to complete the change.
I’ll use Intune Device Remediations to delete Windows Hello for Business (WHfB) registration information for the logged-on user. I’ve created two PowerShell scripts. The first one detects if a user’s WHfB configuration exists, and if it does, it triggers the remediation script, which executes the certutil.exe command mentioned earlier.
Intune Device Remediations requires users to have one of the following licenses. If you are not meeting the license criteria, then you can simply deploy Remediate_WHfB.ps1 script via Intune admin center > Devices > Scripts and remediations > Platform scripts option. For more information, refer to the blog post: How to deploy a PowerShell script using Intune.
Source: Microsoft
- Windows 10/11 Enterprise E3 or E5 (included in Microsoft 365 F3, E3, or E5)
- Windows 10/11 Education A3 or A5 (included in Microsoft 365 A3 or A5)
- Windows 10/11 Virtual Desktop Access (VDA) per user
Contents
Download PowerShell Scripts
- Download Detect-WHfB.ps1 script: Detect-WHfB.ps1.
- Download Remediate_WHfB.ps1: Remediate-WHfB.ps1.
Create a Remediations Script Package
- Sign in to the Intune admin center > Devices > Scripts and remediations
- Click on + Create.
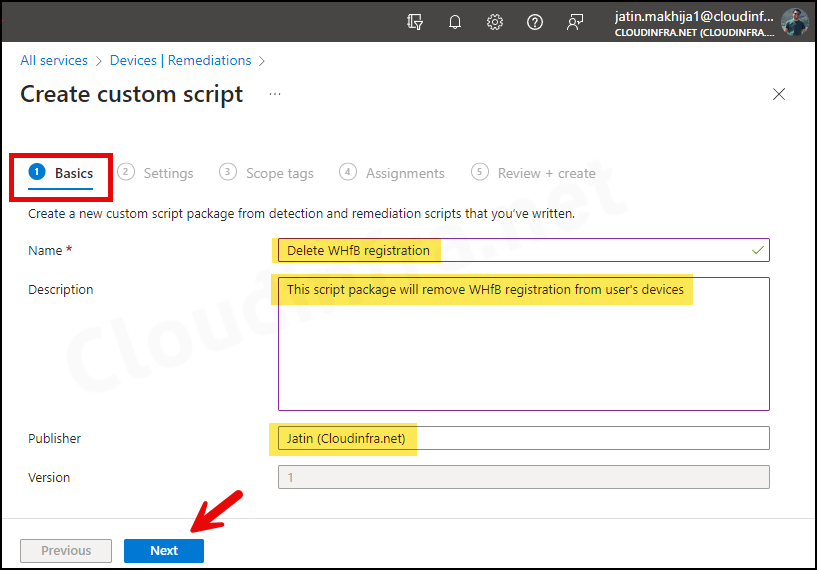
- Basics Tab: Provide the Name and Description of the script package.
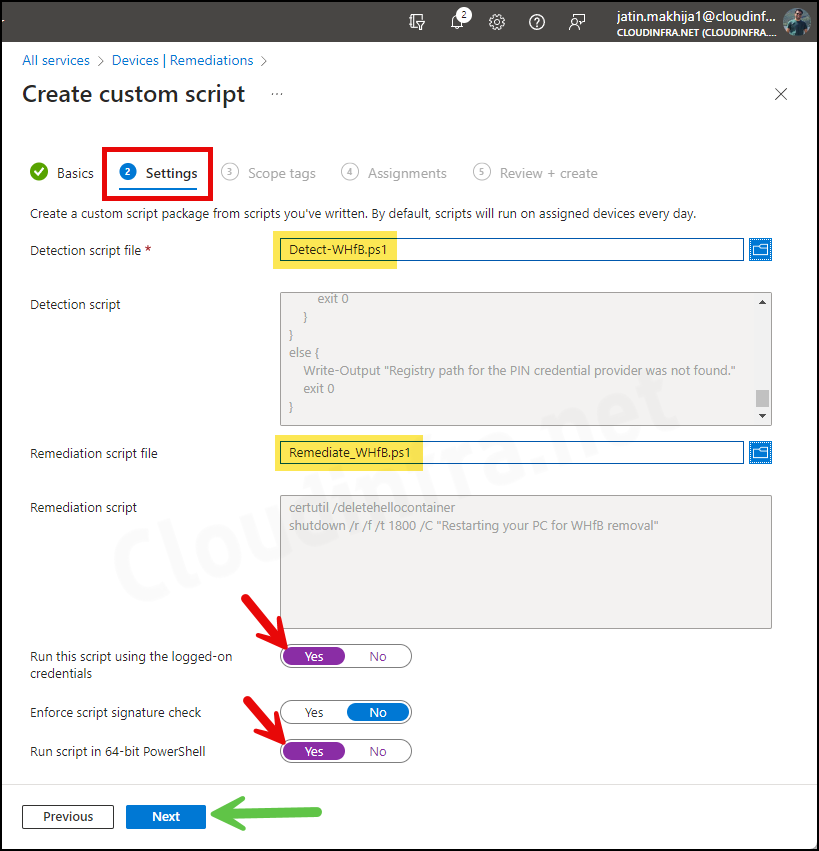
- Settings Tab:
- Detection script file – Browse to the Detection script Detect-WHfB.ps1.
- Remediation script file – Browse to the Remediation script file Remediate_WHfB.ps1.
- Run this script using the logged-on credentials – Yes
- Enforce script signature check – No
- Run script in 64-bit Powershell – Yes
- Scope tags (optional): A scope tag in Intune is an RBAC label you add to resources (policies, apps, devices) to limit which admins can see and manage them. For more Information, read: How to use Scope tags in Intune.
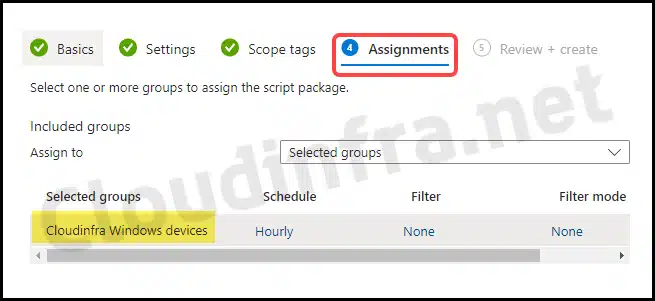
- Assignments: Click on Add group to add an Entra security group containing users or devices. You can also select the Schedule to run this script package. You have three options: Once, hourly, or Daily. For further guidance on assignment strategy, see Intune assignments: User groups vs. Device groups.
- Review + create: Review the deployment and click on Create.
Sync Intune Policies
The device check-in process might not begin immediately. If you’re testing this policy on a test device, you can manually kickstart Intune sync from the device itself or remotely through the Intune admin center.
Alternatively, you can use PowerShell to force the Intune sync on Windows devices. Restarting the device is another way to trigger the Intune device check-in process.
Monitor the Script package
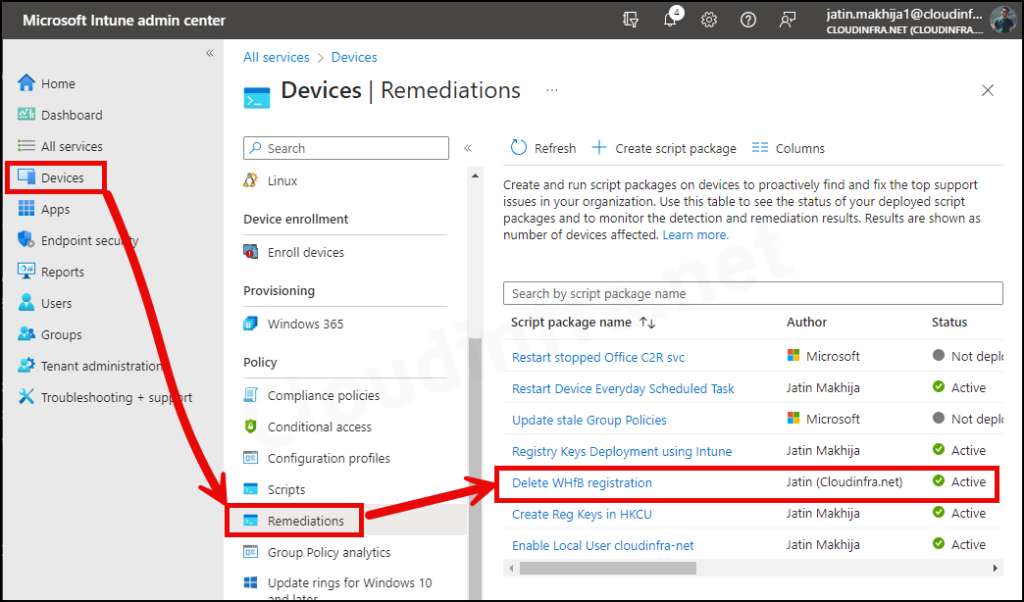
- Sign in to the Intune admin center > Devices > Scripts and remediations.
- Click on the Remediation script package you want to monitor.
- Go to the Overview to find the deployment status of the script package.
End User Experience
End-users won’t receive any notifications after deploying this script package to targeted devices. The script package will run silently in the background, to check if WHfB is configured. If yes, then the script will delete the WHfB registration.
Intune Device Remediations Logs
You can monitor Intune device remediation scripts using the Intune admin center. However, to verify the execution of detection and remediation scripts, you can also review the IntuneManagementExtension.log file. There are more ways to verify PowerShell script deployment, refer to this guide: Deploy a Powershell Script using Intune.
- Browse to C:\ProgramData\Microsoft\IntuneManagementExtension\Logs and open the most recent IntuneManagementExtension.log log file. You can sort the files list using the Date modified column.
- Open the file and search for the Intune device remediation script package using its policy ID. You will find Detection and Remediation scripts with Exit codes, which confirm that the scripts are working fine.

certutil /deletehellocontainer
Running the command above manually appeared to succeed but after a reboot Windows Hello was forced on me again.
You need to disable Hello for Business through policy (Intune configuration profile using Settings Catalog). All this script does is delete the container on the local device. However, if Hello is enabled through policy then the user will simply be prompted to set it up again on the next reboot.
Yes, you can disable it first using the Intune Device configuration profile. Please refer to the post for more information: https://cloudinfra.net/disable-windows-hello-for-business-using-intune/
Thank you so much for your support you are a rock in our scenario a common PIN was set for all users and instructed all users later to change PIN but the majority of users did not change PIN so later for Intune implementation the task was assigned to me and I have disabled all Windows Hello from Intune but the problem was those users who already using windows hello the option was disabled from Intune but still they could use the old PIN and new users were unable to use a pin,
this script rescues me when I implement it on all users so it will check if not Windows Hello so script will skip if implemented so it will remove Windows Hello thing worked perfectly thanks a lot.
Hello,
I’m trying out your fantastic instructions, but am hitting a wall on the remediation. It’s failing. When I tried testing the command locally, I’m seeing this error. I tried it at the Admin version and standard prompt. Ideas?
certutil.exe -deleteHelloContainer
CertUtil: -DeleteHelloContainer command FAILED: 0x80090010 (-2146893808 NTE_PERM)
CertUtil: Access denied.
Hi Susan,
I’m seeing the same thing, did you find a solution?
Thanks!
Hello Susan,
I got same issue.
To avoid it, you should run this script with logged on user-credentials.(Above in the settings tab)
With admin rights it s not working.