In this blog post, I will show you the steps to disable WHfB Post logon Provisioning using Intune. Let’s understand the background of it and then check the steps to disable it.
Background
A common practice in many organizations is to disable Windows Hello for Business tenant-wide, while allowing it for specific users or devices. This ensures that users won’t be prompted with the mandatory WHfB screen during the device enrollment process, allowing them to configure it when ready.
This kind of setup can be achieved by below two steps:
- Disable WHfB from Windows Enrollment Settings – Go to Intune admin center > Devices > Enrollment > Click on Windows Hello for Business under Windows tab and set Configure Windows Hello for Business setting to Disabled.
- Enable WHfB using Device Configuration Profile > Identity Protection template.
By following both of these steps, users will have the ability to configure WHfB post-logon. However, users will be prompted to configure WHfB every time they sign out, back in, or restart the device. While they can skip it, the prompt will reappear the next time they attempt to sign in to the device.
This can be unpleasant, and there are situations where you might want to disable it, ensuring users won’t encounter the WHfB screen after login. However, you still want to ensure users can go to the Settings App and configure WHfB when ready.
This blog post will address this issue using Intune Device Remediations. Intune device remediations require Enterprise licensing. If you don’t meet the license criteria, you can use the provided PowerShell scripts and deploy them using the Devices > Scripts and remediations > Platform scripts method.
Contents
Download PowerShell Scripts
- Download Detect-WHfB-reg.ps1 script: Detect-WHfB-reg.ps1.
- Download Remediate-WHfB-reg script: Remediate-WHfB-reg.ps1.
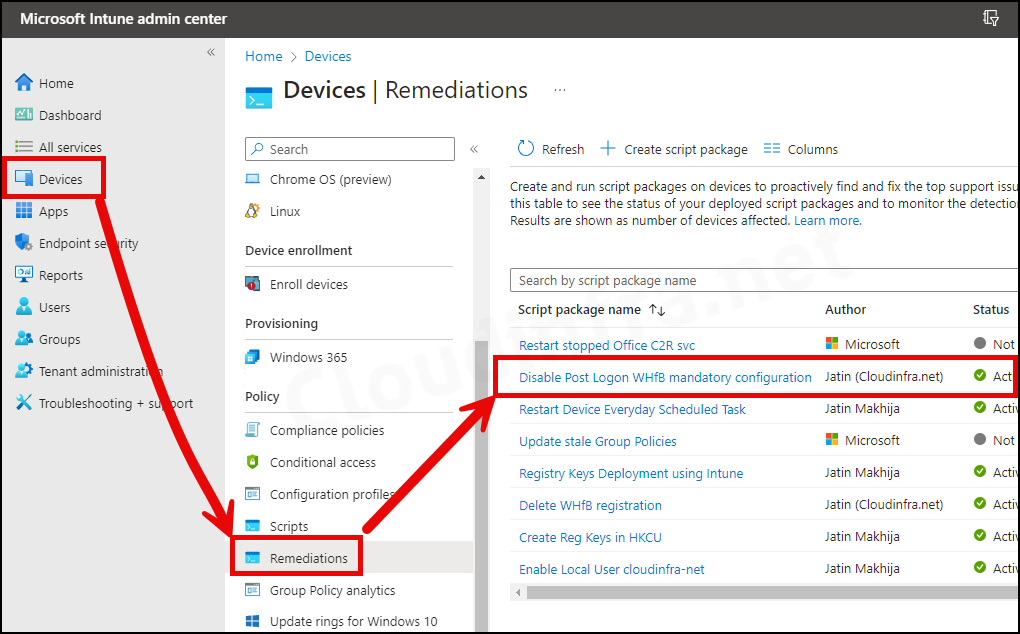
Create a Remediations Script Package
- Sign in to the Intune admin center > Devices > Scripts and remediations.
- Click on + Create.
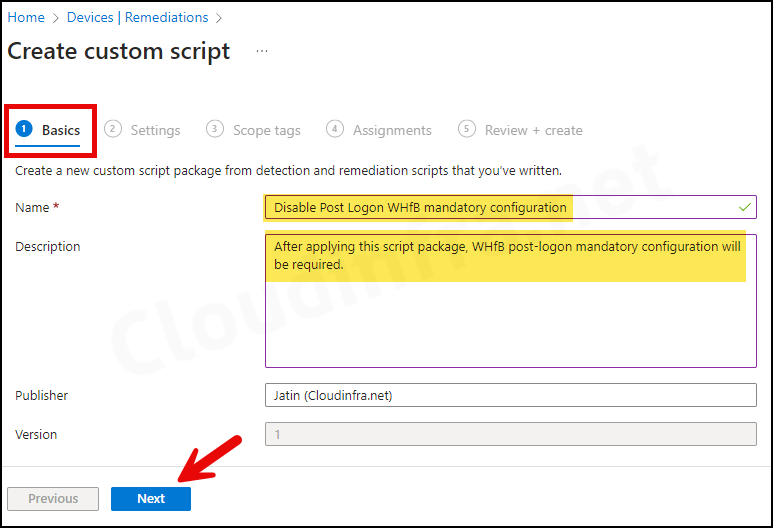
- Basics Tab: Provide the Name and Description of the script package.
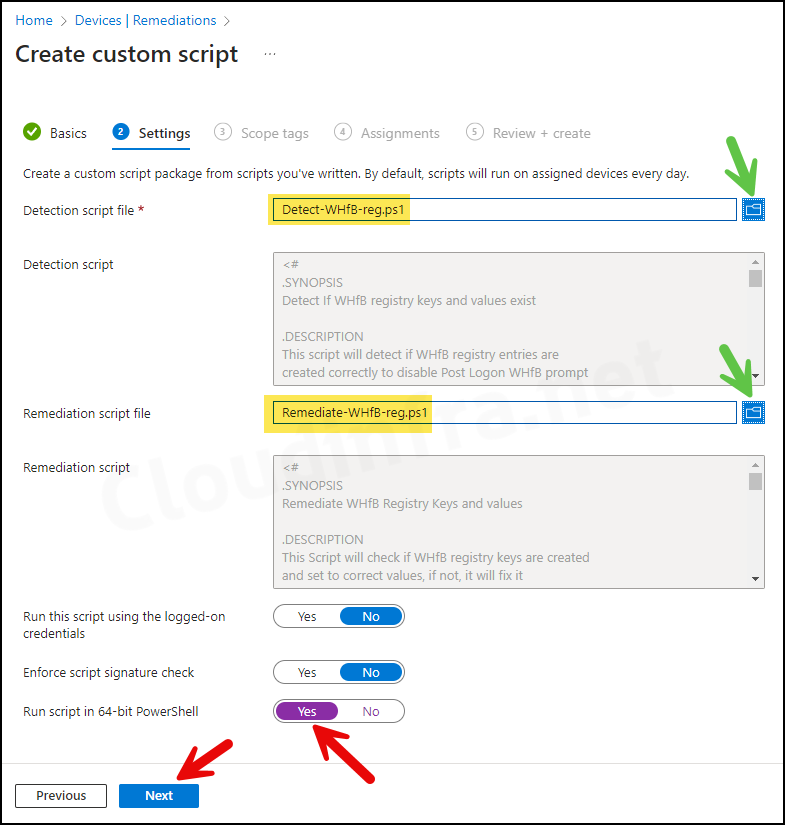
- Settings Tab
- Detection script file – Browse to the Detection script Detect-WHfB-reg.ps1.
- Remediation script file – Browse to the Remediation script file Remediate_WHfB-reg.ps1.
- Run this script using the logged-on credentials – No
- Enforce script signature check – No
- Run script in 64-bit Powershell – Yes
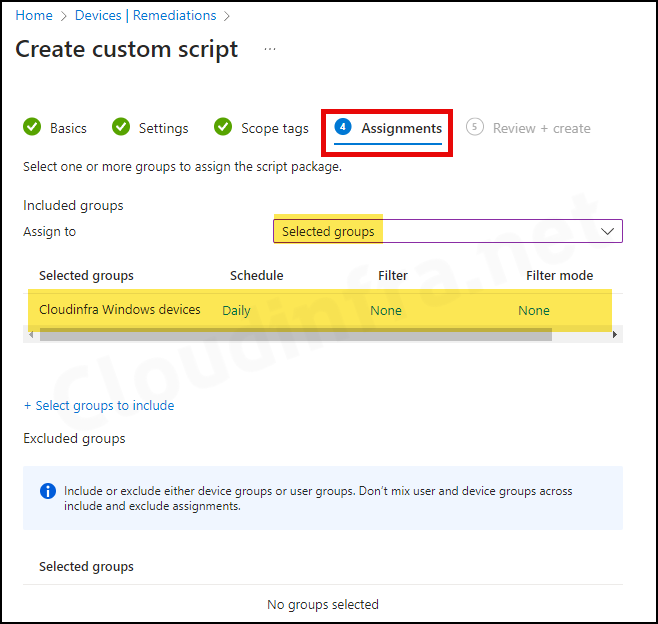
- Scope tags: Click on Next.
- Assignments: Click Add group to include an Entra security group containing users/devices. Select the schedule for running this script package to Once, Hourly, or Daily.
- Review + create: Review the deployment and click on Create.
Sync Intune Policies
The device check-in process might not begin immediately. If you’re testing this policy on a test device, you can manually kickstart Intune sync from the device itself or remotely through the Intune admin center.
Alternatively, you can use PowerShell to force the Intune sync on Windows devices. Restarting the device is another way to trigger the Intune device check-in process.
Monitor the Script package
- Sign in to the Intune admin center > Devices > Scripts and remediations
- Click on the Remediation script package you want to monitor.
- Go to the Overview to find the deployment status of the script package.
End User Experience
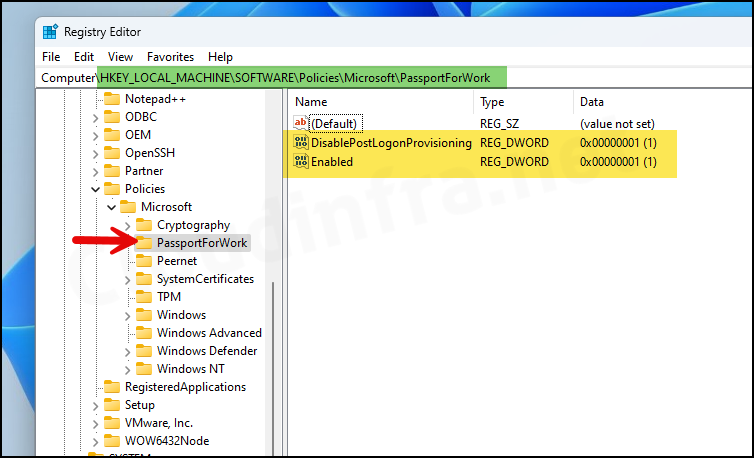
After a successful deployment, you’ll observe that registry keys to disable WHfB post-logon provisioning have been created. To confirm this, follow the steps below:
- Press the Windows key + R to open the Run dialog box
- Type regedit and press Enter to open the Registry Editor.
- Navigate to HKEY_LOCAL_MACHINE\SOFTWARE\Policies\Microsoft, and you will find the PassportforWork registry key.
- Within the PassportforWork registry key, locate two entries named DisablePostLogonProvisioning and Enabled. Ensure that both entries are set to a value of 1.
Where can you find logs for Intune device remediation scripts?
You can monitor Intune device remediation scripts using the Intune admin center. However, to verify the execution of detection and remediation scripts, you can also review the IntuneManagementExtension.log file. There are more ways to verify PowerShell script deployment, refer to this guide: Deploy a PowerShell Script using Intune.
- Browse to C:\ProgramData\Microsoft\IntuneManagementExtension\Logs and open the most recent IntuneManagementExtension.log log file. You can sort the files list using the Date modified column.
- Open the file and search for the Intune device remediation script package using its policy ID. You will find Detection and Remediation scripts with Exit codes, which confirm that the scripts are working fine.
Conclusion
In this blog post, we have used Intune device remediations method for disabling WHfB post login provisioning. As it requires Enterprise license to use, you can deploy the powershell script directly. You can also package the scripts into .intunewin file, however that will make it more complex.

A simpler way to do this would be to just use a Configuration Profile with Custom CSP:
./Device/Vendor/MSFT/Policy/Config/WindowsLogon/OverrideShellProgram
(https://learn.microsoft.com/en-us/windows/client-management/mdm/passportforwork-csp#devicetenantidpoliciesdisablepostlogonprovisioning)
Life saver!
Hello
Iam trying to remove Pincode, Fingerprint and Face-ID from our company PC’s to force employees to use their actual password,
After completing these steps i can see the regedit keys but the pincode / fingerprint is not disabled on my test PC.
are there anything iam missing for it to disable the options for WHfB?
Mikkel Henriksen
Introduction
Windows Hello for Business is a private and secure identity verification method built into Windows 10. However, there may be instances where you need to delete your Windows Hello for Business registration. This article provides a step-by-step guide on how to do this.
Body
Step 1: Open Command Prompt
First, you need to open the Command Prompt as an administrator. To do this:
Press the Windows key + X and select Command Prompt (Admin) from the menu.
Step 2: Delete the WinBioDatabase
The next step is to delete the WinBioDatabase. This can be done by running the following command in the Command Prompt:
del /F /Q C:\Windows\System32\WinBioDatabase\*
This command deletes all files in the WinBioDatabase directory.
Step 3: Delete the Hello Container
Finally, you need to delete the Hello Container using the certutil.exe tool. Run the following command in the Command Prompt:
certutil.exe -DeleteHelloContainer
This command deletes the Hello Container, effectively removing your Windows Hello for Business registration.
🔗 Relevant links
Windows Hello for Business Overview
Certutil tasks for managing a certification authority
Command Prompt: frequently asked questions
if you have other Win-Hello configs set through Intune (such as min. PIN, cloudtrust, no cap/etc), doing it this way bypasses all the configs in Intune. It leaves everything at default.
I found this too. I changed the location to be the location that Intune uses and everything works.
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Policies\PassportForWork\{TENANT ID}\Device\Policies