In this blog post, I will show you the steps to block/whitelist Edge extensions using Intune. This will give you greater control over which extensions can be used on your organization’s devices, helping to keep your data secure and your employees productive.
Permitting users to install browser extensions can pose a security risk, as they may inadvertently add a malicious extension that could harm the device or the organization. As an Intune administrator, managing and controlling the extensions that end users can install is essential.
A best practice is blocking all extension installations and only permitting specific extensions approved by the administrator. This approach ensures that the extensions are secure and regularly updated.
If you manage your organization’s devices through Intune, you can create a device configuration profile that includes settings for allowing or blocking extensions in Microsoft Edge. You can then apply this profile to the Windows devices.
We’ll use the Settings Catalog settings for this task. For configuring this policy, we will need app Extension’s ID. Let’s check the steps to get the Extension’s ID and create an Intune policy.
Contents
Step 1: Find the Extension’s ID for Whitelisting
Let’s check the steps to get the Extension’s ID from Microsoft Edge browser.
- Launch the Microsoft Edge browser.
- Click on the three dots on the top right-hand side corner.
- Click on Extensions.
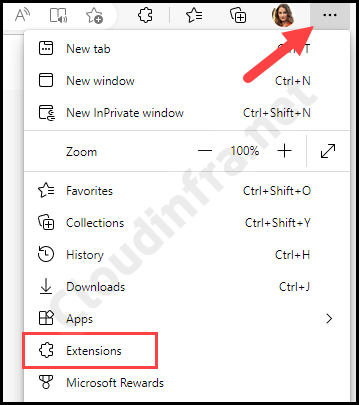
- Click on Manage extensions > Get extensions for Microsoft Edge.
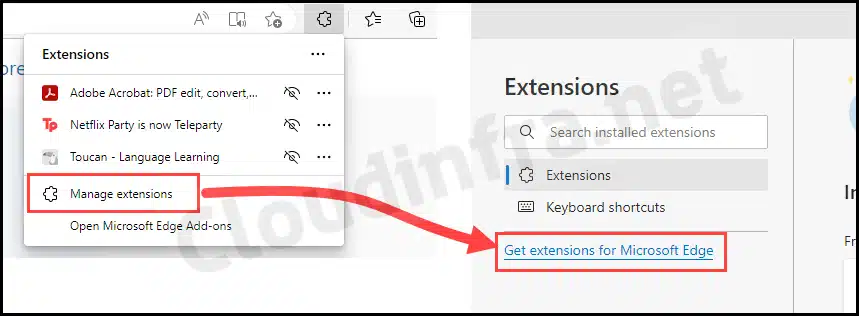
- Search for the Extension that you want to whitelist. Let’s take Adobe Acrobat as an example. Please search for the Extension and then click on it.

- At the top of the page, in the browser’s address bar, you should be able to locate the Extension ID as a part of the URL. Copy the Extension ID and paste it into a notepad.

- Repeat this process for all other extensions you want to whitelist, copying their Extension IDs into the notepad. You’ll need these Extension IDs when creating a policy in Intune.
Step 2: Block All Extensions in Edge and Whitelist Only Approved Ones
You can either Block All Extensions in Edge and Whitelist only the ones you want to allow. Secondly, you also have the option to block specific Extensions while allowing the rest of the Extensions. The first approach is more controlled as it allows only the approved extensions to be accessible to users while remaining ones remain blocked. Let’s configure it via Intune admin center.
- Sign in to the Intune admin center > Devices > Configuration > Create > New Policy.
- Select Platform as Windows 10 and later
- Profile type as Settings catalog
- Click Create.
Download Microsoft Edge ADMX template and Import an ADMX file into Intune.
Read Next
- Basics Tab: Provide a Name and Description of the Policy and click Next.
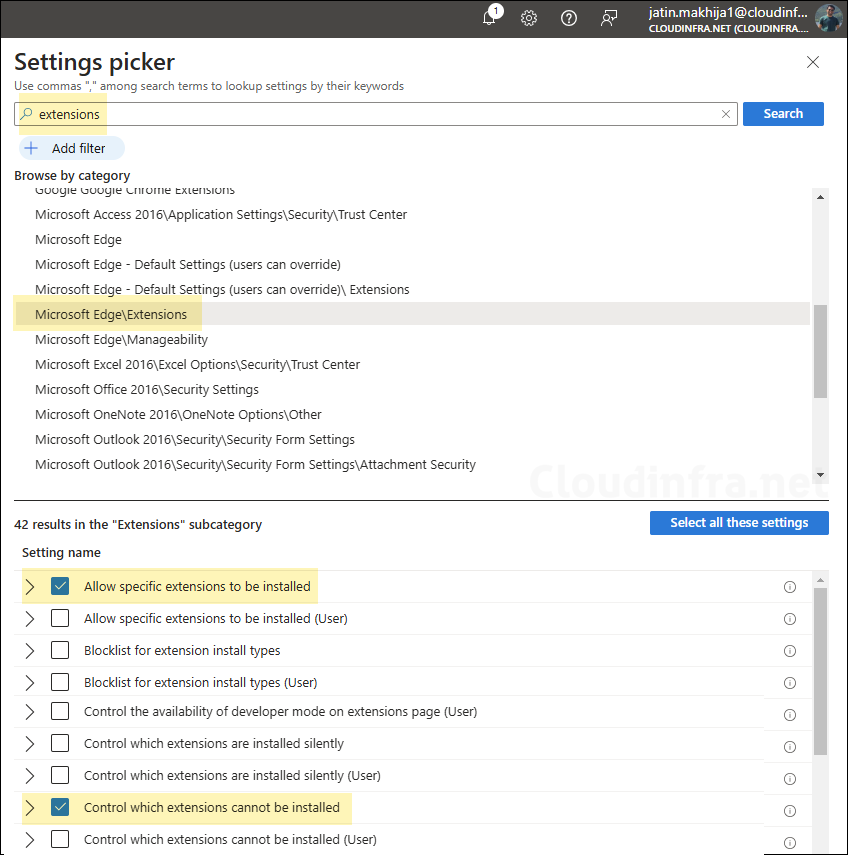
- Configuration Settings: Click on Add Settings and use the Settings picker to search using the keyword extensions. Select the category Microsoft Edge\Extensions and select Control which extensions cannot be installed and then Allow specific extensions to be installed.
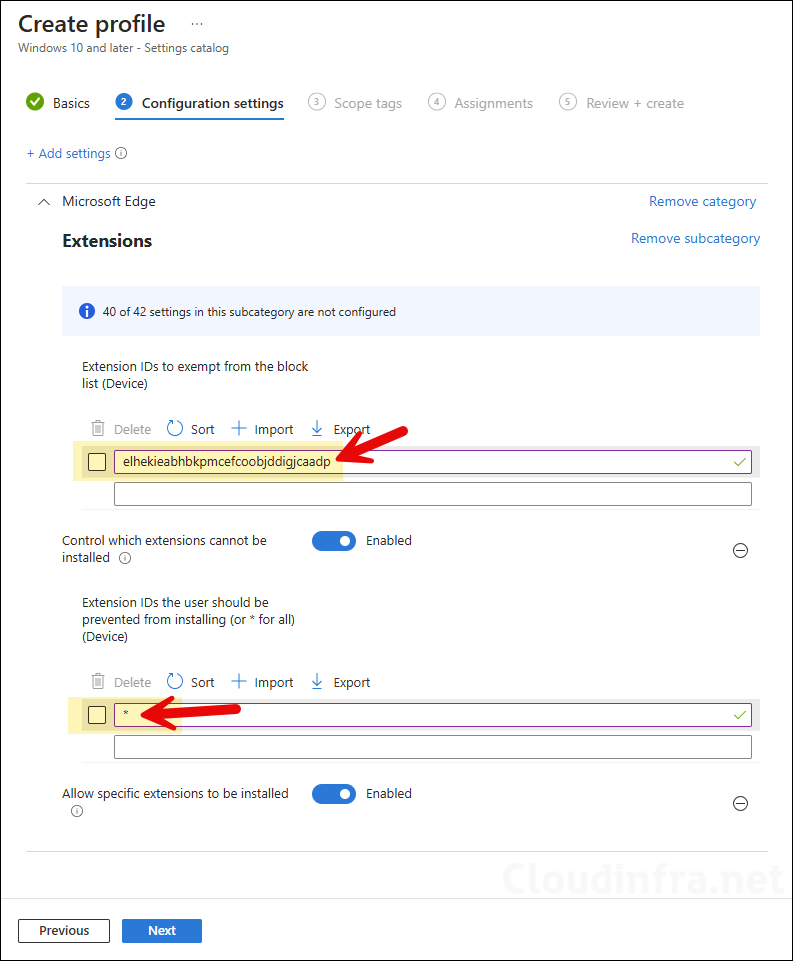
- Control which extensions cannot be installed: Enable this setting and add * in the text box, and click OK to save. This will block all Extensions in Edge.
Instead of blocking all extensions using a wild card character *. You can also provide the extension IDs to block only specific extensions in Microsoft Edge.
In this scenario, we are Blocking All Edge Extensions and using Allow specific extensions to be installed, setting to whitelist specific Extensions.
Note
- Allow specific extensions to be installed: Enable this setting and provide the Extension IDs to Whitelist in Edge browser. In our example, we are whitelisting the Adobe Acrobat extension, therefore we have provided the Extension ID of Adobe Acrobat.
- Assignments tab: Click Add groups and select Entra security group containing Windows 10/11 devices or users.
- Review + Create: Review the device configuration profile on the Review + Create tab and click Create.
Sync Intune Policies
The device check-in process might not begin immediately. If you’re testing this policy on a test device, you can manually kickstart the Intune sync from the device itself or remotely through the Intune admin center.
Alternatively, you can use PowerShell to force the Intune sync on Windows devices. Restarting the device is another way to trigger the Intune device check-in process.
End User Experience
After successfully deploying this policy, open the Edge browser to test whether the installation of all extensions is blocked and whether only the specific extension (in this case, Adobe Acrobat) is allowed according to the Whitelist.
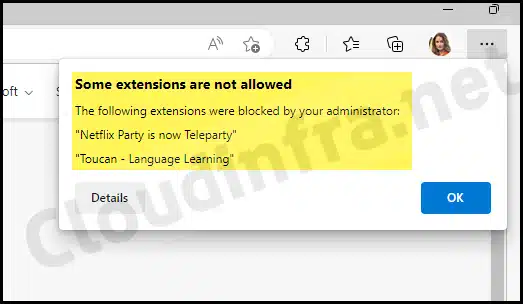
If any existing extensions were installed when this policy was applied, they will also be blocked. An error may show up on Edge – Some extensions are not allowed. Only the extensions that you Whitelist from Intune will be allowed.
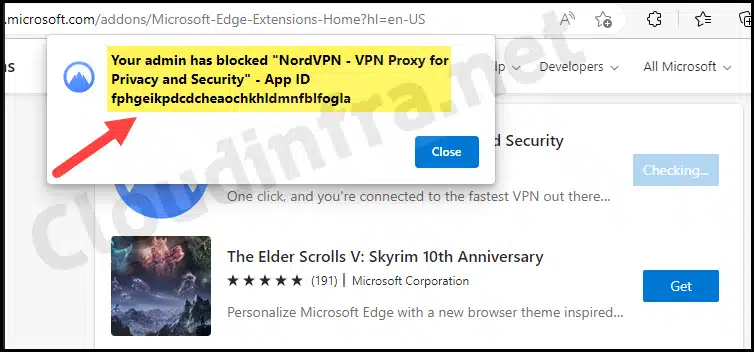
Now, let’s check if we can install any other extension in Edge. An error message is displayed when attempting to install the Nord VPN browser extension: Your admin has blocked <extension name> for Privacy and Security – App ID <AppID>.
Conclusion
In this blog post, we’ve explored the straightforward process of creating block lists and whitelists for extensions using Intune for the Microsoft Edge browser. You don’t need to use OMA-URI settings; you can leverage Settings catalog to create blocklists and Whitelists of Edge extensions and apply them to end-user devices.

What is the best way to remove extensions already installed?
Hey Tom, Is there any particular reason for removing the extension? Blocking it makes it unusable anyway. The best way to manage is to Block All Edge extensions and Whitelist only the ones that are approved by your organization.