In this blog post, I will demonstrate the steps to configure default apps on Windows using Intune. Default apps on Windows refer to the programs or applications that are configured to open and handle specific file types on your computer automatically. For example, when you open a document with a .docx extension, it will automatically open in Microsoft Word.
Similarly, a saved document with a .pdf extension will be opened using Adobe Reader. You can also set a default web browser, such as Microsoft Edge or Google Chrome, to handle web links and web-related tasks. These default app settings streamline the user experience and make it more convenient to open files and perform various tasks on your computer.
In an organization, it’s often a good practice to configure a standard set of applications as default apps for all users. This ensures consistency and makes it easier for users to work with the expected software. Setting default apps simplifies tasks and minimizes confusion when dealing with various file types and tasks within the organization’s ecosystem.
You have two primary methods for configuring default apps in Windows 10/11 for your organization. One option is to use an OMA-URI like ApplicationDefaults/DefaultAssociationsConfiguration. The other involves applying default association configurations by using Settings catalog policy. In this blog post, we’ll focus on configuring default apps using a Settings catalog policy.
Contents
Step 1: Generate Default app Association XML
Configure Default apps on a Windows device manually
- Login to any Windows 10 or Windows 11 device.
- Manually configure the default apps that you intend to configure through Intune.
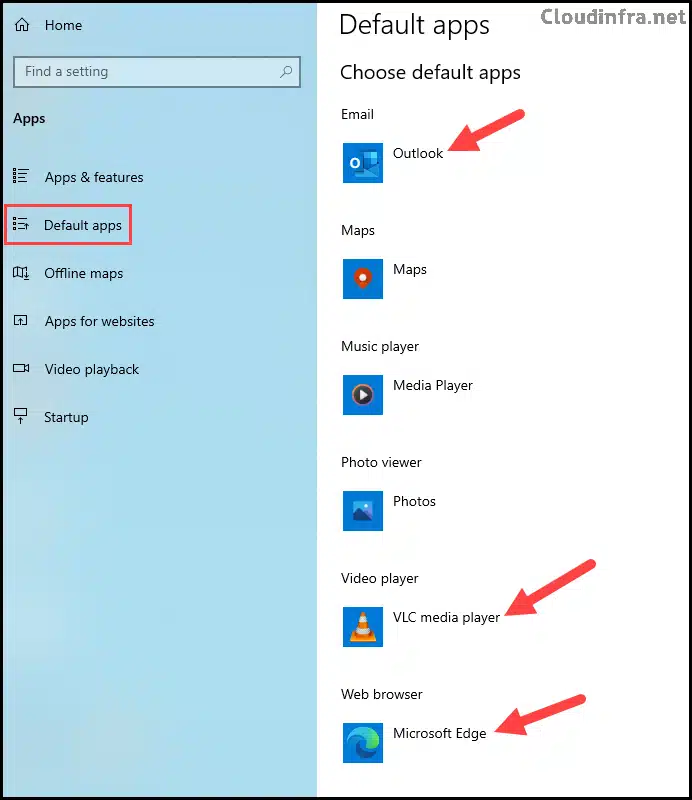
For example, I’d like to set the following default apps on the target devices:
- Email: Outlook
- Video Player: VLC
- Web Browser: Microsoft Edge
Generate App Associations XML File
To generate an app association XML file, follow the steps below on the same device we used in Step 1 to configure default apps manually.
- Create an empty folder anywhere in your system. For example: C:\temp.
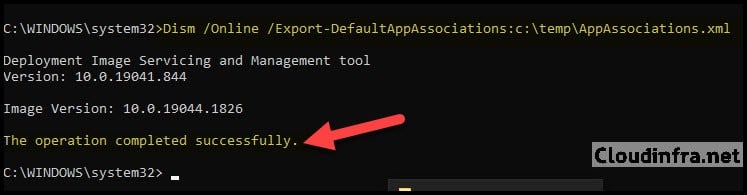
- Open the command prompt as an administrator and run the below command:
Dism /Online /Export-DefaultAppAssociations:"C:\temp\AppAssociations.xml"
- Open the AppAssociations.xml file and delete all the app associations except for Microsoft Edge, VLC, and Outlook.
- You can customize the file by removing unnecessary lines. For instance, if you don’t want to associate .pdf files with Microsoft Edge, you can delete the .pdf line from the XML and continue.
AppAssociations.xml
<?xml version="1.0" encoding="UTF-8"?> <DefaultAssociations> <Association Identifier=".avi" ProgId="VLC.avi" ApplicationName="VLC media player" /> <Association Identifier=".wmv" ProgId="VLC.wmv" ApplicationName="VLC media player" /> <Association Identifier=".m4v" ProgId="VLC.m4v" ApplicationName="VLC media player" /> <Association Identifier=".mkv" ProgId="VLC.mkv" ApplicationName="VLC media player" /> <Association Identifier=".mov" ProgId="VLC.mov" ApplicationName="VLC media player" /> <Association Identifier=".mp2v" ProgId="VLC.mp2v" ApplicationName="VLC media player" /> <Association Identifier=".mp4" ProgId="VLC.mp4" ApplicationName="VLC media player" /> <Association Identifier=".mp4v" ProgId="VLC.mp4v" ApplicationName="VLC media player" /> <Association Identifier=".htm" ProgId="MSEdgeHTM" ApplicationName="Microsoft Edge" /> <Association Identifier=".html" ProgId="MSEdgeHTM" ApplicationName="Microsoft Edge" /> <Association Identifier=".pdf" ProgId="MSEdgeHTM" ApplicationName="Microsoft Edge" /> <Association Identifier="http" ProgId="MSEdgeHTM" ApplicationName="Microsoft Edge" /> <Association Identifier="https" ProgId="MSEdgeHTM" ApplicationName="Microsoft Edge" /> <Association Identifier="read" ProgId="MSEdgeHTM" ApplicationName="Microsoft Edge" /> <Association Identifier="mailto" ProgId="Outlook.URL.mailto.15" ApplicationName="Outlook" /> </DefaultAssociations>
Step 2: Encode App associations XML to base64 format
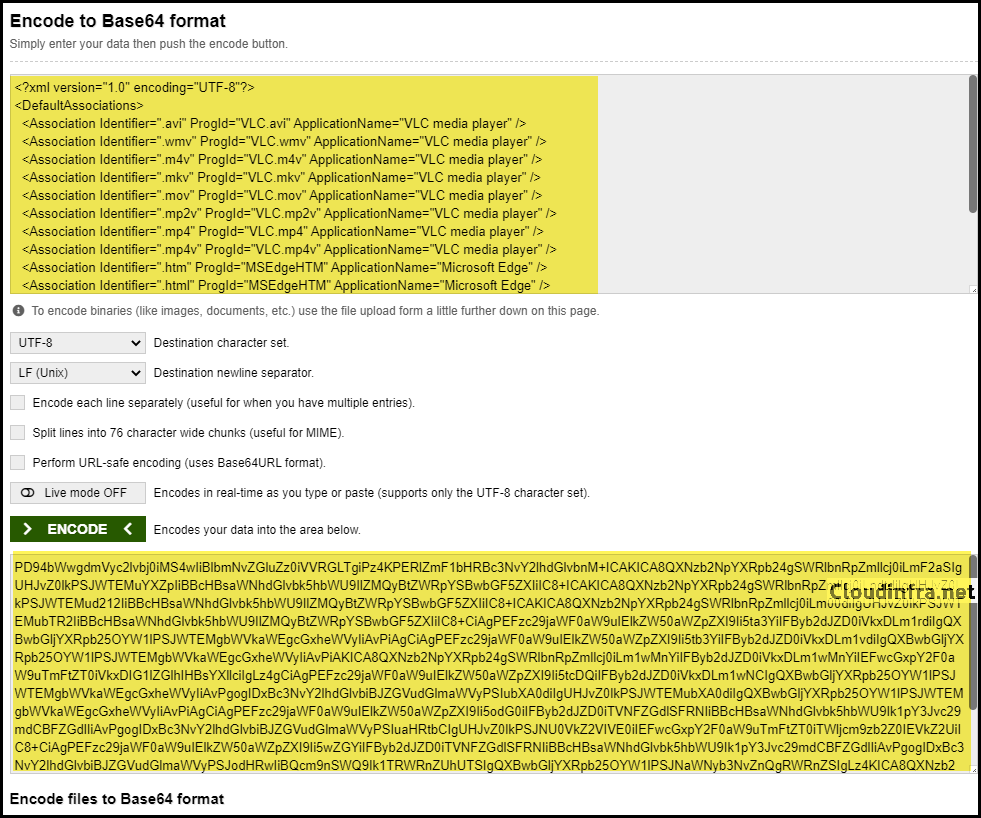
Use a base64 encoder application to convert AppAssociation.XML to a base64 encoded XML
- Click on the base64encode link.
- Copy the contents of the App associations XML file into the encoder and click on the Encode button.
- You will get an Output. Copy and paste the Output somewhere in Notepad.
Step 3: Create a Device Configuration Profile
- Sign in to the Intune admin center > Devices > Configuration > Create > New Policy.
- Select Platform type as Windows 10 and later
- Select Profile type as Settings Catalog
- Click on Create
- Basics: Provide a Name and Description of the Policy.
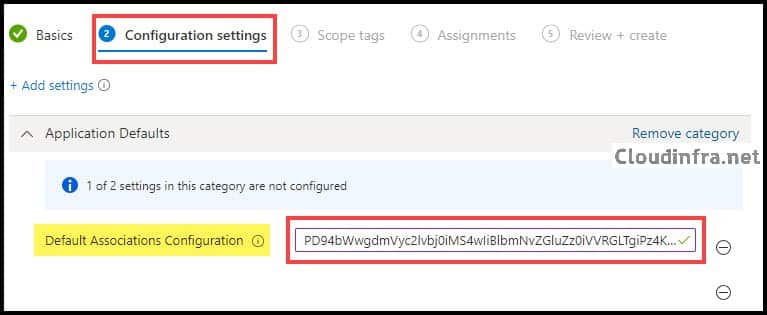
- Configuration settings
- Click on + Add settings
- Search for Application Defaults in the Settings Picker
- Select Default Associations Configuration setting.
- Copy the base64 encoded value generated in the previous step in the Default Associations configuration text box.
It’s important to note that if you already have another device configuration profile with Default Associations Configuration, creating a new Default Association Configuration will result in a conflict, and the new configuration will not be applied. Ensure that only one Device Association Configuration is applied to a device.
Note
- Assignments: Select Add groups and opt for an Entra security group containing Windows 10/11 devices or Entra ID users.
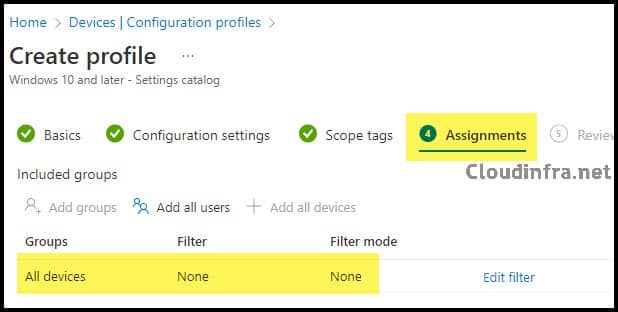
- Review + create: Review the policy summary and click Create.
Sync Intune Policies
The device check-in process might not begin immediately. If you’re testing this policy on a test device, you can manually kickstart Intune sync from the device itself or remotely through the Intune admin center.
Alternatively, you can use PowerShell to force the Intune sync on Windows devices. Restarting the device is another way to trigger the Intune device check-in process.
End User Experience
1. Confirm Default Apps association deployment from Settings App
- Go to the Settings App on the device.
- Click on Apps > Default Apps.
- You will find that the Default Apps are configured now as per the configuration via the Device configuration profile.
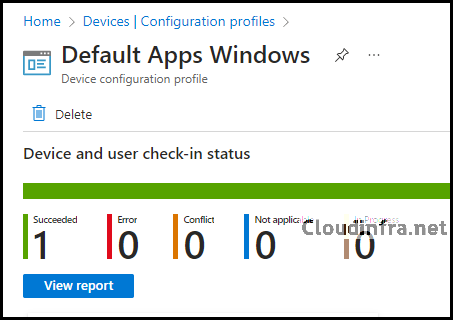
2. Confirm Default Apps association deployment from Intune admin center
- Sign in to the Intune admin center > Devices > Configuration.
- Search for the deployed default apps.
- The deployment status can be checked in the Overview section. You can also click on View Report to find more information about the deployment status.
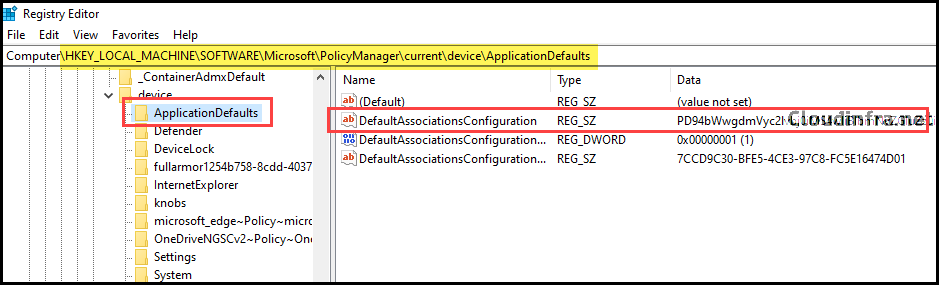
3. Confirm Default Association Configuration deployment from Registry
- Go to Start > Type regedit and click on Registry Editor.
- Find the Registry Key HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\PolicyManager\current\device\ApplicationDefaults.
- You can check a Registry Entry on the right-hand side: DefaultAssociationsConfiguration, which should now be set to base64 encoded value configured via Intune.
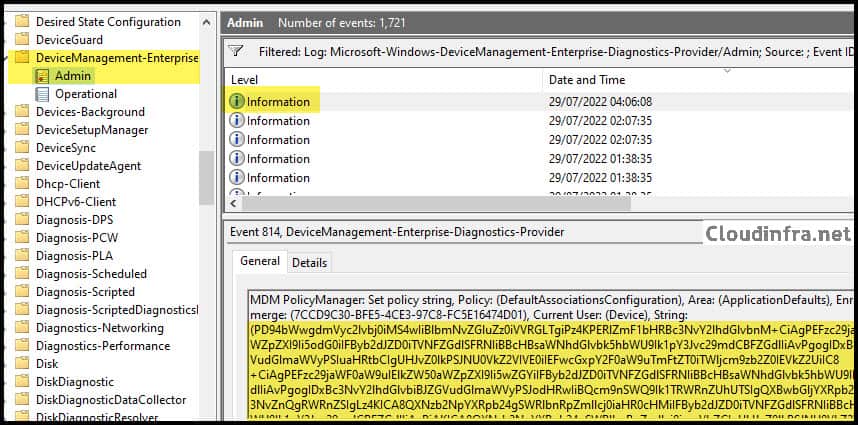
4. Confirm Default Association Configuration deployment using Event Viewer
- Go to Start > Search for Event Viewer and click on it to Launch Event Viewer MMC.
- Expand Application and Services logs > Microsoft > Windows.
- Find DeviceManagement-Enterprise-Diagnostics-Provider folder.
- Click on Admin and Filter for Event ID 814.
- Go through the logs to find this particular policy status.
Conclusion
In this blog post, we have seen how to configure default apps on Windows using Intune. We have configured VLC, Microsoft Edge, and Outlook apps as default apps on the device. However, you can adjust default app associations per your requirements.
You can also use an OMA-URI setting to configure default apps, but using the Settings Catalog option seems simpler. If you wish to use OMA-URI, then you can create a Custom device configuration profile and then Add below OMA-URI Setting:
| Name | DefaultAppsonWindows |
| Description | Set Default apps on windows devices |
| OMA-URI | ./Vendor/MSFT/Policy/Config/ApplicationDefaults/DefaultAssociationsConfiguration |
| Data type | String |
| Value | base64 encoded output value |

Hello Jatin,
Thanks for the article, I created the profile as per article and applied it on Hyper-V Virtual machine. Profile is successfully applied. Can see the in registry Key also in logs but in Default application for mailto is not changed to outlook. also in EventLog it is showing error like for enrollment ID requesting Set : The operating system drive is not protected by Bitlocker Drive Encryption.
Hi —
Does this device configuration make immediate changes for existing users? Or is this only for new user log-ins on the device?
Hi JoeZ,
1. Does this device configuration make immediate changes for existing users? – It may not be an immediate change for the user, At the next Intune Device check-in the Profile will be applied and default apps will be configured.
2. Is this only for new user log-ins on the device? – It will apply to all the users you have targeted under Assignments either via Azure AD group or by adding All Devices or All users.
Hello
Great guide thank you. I’ve followed everything but I cannot seem to get this to deploy? Intune doesn’t apply anything and states ‘not applicable’
I am targeting a security group which contains our test server
Any advice would be great~!
Hey Matt, thanks for the feedback. Could you please try adding a Windows 10 or Windows 11 device to this test group and see if it works? I didn’t test this policy on a server, and it appears that the policy might not be applicable to the Server platform. The only way to confirm this is to test it on Windows 10 or Windows 11 devices.