In this blog post, I will show you the steps to Enable/Disable local admin using Intune remediations. Windows computers have an Administrator account (SID S-1-5-domain-500, display name Administrator), this is the first account created during the Windows installation.
The Administrator account has full control of the files, directories, services, and other resources on the local device. The default Administrator account can’t be deleted or locked out but can be renamed or disabled. An Administrator account can’t be removed from the Administrators group.
Best practice is to use a non-administrator account to log on to the PC and elevate to an administrator account when required, e.g., installing applications or performing configuration tasks on your device.
However, if you are using Windows LAPS and managing a built-in Administrator account, It must be enabled before you can deploy the LAPS policy to the device. You can enable or disable a built-in Administrator account simply using a Settings catalog policy Accounts Enable Administrator Account status.
However, if you try to re-enable the Administrator account using Settings catalog policy after it was disabled and the current Administrator password doesn’t meet the password requirements. You can’t re-enable it using Settings catalog policy shown in this blog post.
An alternative approach is to use PowerShell scripts, which can first set a password for the local user account that meets the complexity requirements and then enable the account.
Contents
Important Points
- The local admin account used in the script is named cloudinfra-net [This is the built-in Administrator account, I have renamed it to cloudinfra-net].
- You can replace the variable
$userto target a specific local admin account as needed. For instance, if you are retaining the default name for the built-in Administrator account, you can update the value of the variable $user in the script,$user = "Administrator". This allows you to target the appropriate local admin account in your scripts.
- In the remediation script, you’ll observe that it uses a plaintext password provided within the script. It’s important to note that this password is not intended to be permanent for the local administrator account, as this account will be managed by Windows LAPS. LAPS automatically rotates local admin password.
Enable/Disable built-in Administrator Account using Intune Remediations
Using the scripts, we will check if the built-in local administrator account is disabled or not. If it’s disabled, it will set a complex password for a local admin user account and enable the account. Please note that you can use the same script for disabling the built-in Administrator account. You would need to use Disable-Localuser cmdlet instead of Enable-Localuser cmdlet to disable the account.
- Sign in to the Intune admin center > Devices > Scripts and remediatons.
- Click on + Create under the Remediations tab.
- Basics: The basics tab will provide information about the script package, such as name, description, and publisher.
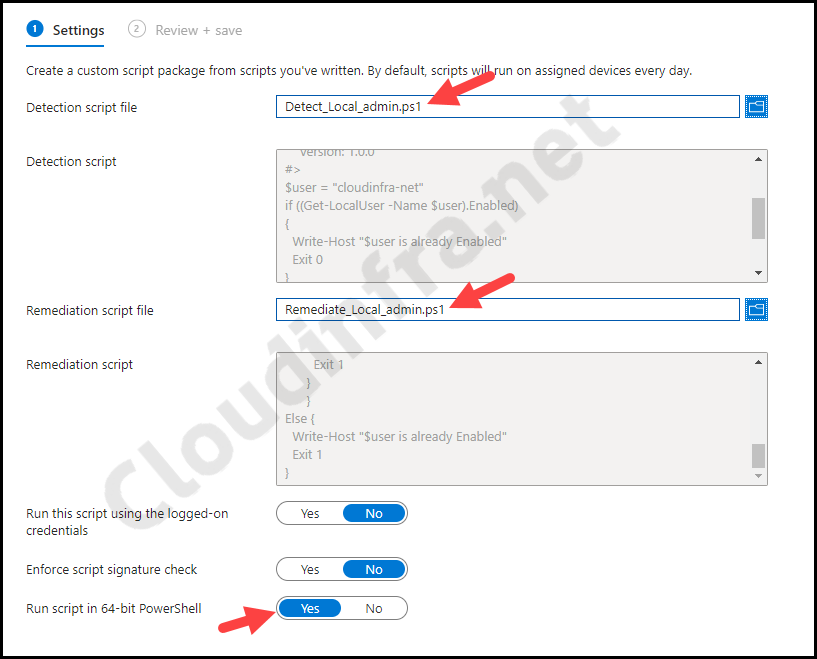
- Settings Tab: Create a detection script using the PowerShell code below. Save it as Detect_Local_Admin.ps1.
Detect_Local_Admin.ps1
<#
.DESCRIPTION
This script will check if the local user account is enabled or not.
Author: Jatin Makhija
Site: cloudinfra.net
Version: 1.0.0
#>
$user = "cloudinfra-net"
if ((Get-LocalUser -Name $user).Enabled)
{
Write-Host "$user is already Enabled"
Exit 0
}
Else {
Write-Host "$user is not Enabled"
Exit 1
}
- Create a remediation script using the PowerShell code below. Save it as Remediate_Local_Admin.ps1.
Remediate_Local_Admin.ps1
<#
.DESCRIPTION
This script will check if the local user account is enabled or not.
If its not Enabled, then it will reset its password and then Enable
the local user account.
Author: Jatin Makhija
Site: cloudinfra.net
Version: 1.0.0
#>
$user = "cloudinfra-net"
if (((Get-localuser -Name $user).Enabled) -eq $false)
{
try{
Write-Host "Resetting password and Enabling User"
$password = ConvertTo-SecureString "HnjIUNkje&*930" -AsPlainText -Force
$UserAccount = Get-LocalUser -Name $user
$UserAccount | Set-LocalUser -Password $Password
Enable-LocalUser -Name $user
Exit 0
}
Catch {
Write-Host "$user is already Enabled"
Write-error $_
Exit 1
}
}
Else {
Write-Host "$user is already Enabled"
Exit 1
}
- Detection script file – Browse to the Detection script Detect_Local_Admin.ps1
- Remediation script file – Browse to Remediation script file Remediate_Local_Admin.ps1
- Run this script using the logged-on credentials – No
- Enforce script signature check – No
- Run script in 64-bit Powershell – Yes
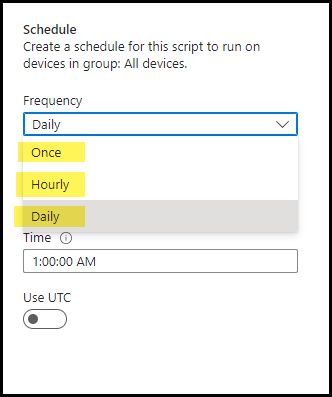
- Assignments: Click on Add group to add an Entra security group containing users or devices. You can also select the Schedule to run this PowerShell script. You have three options: Once, hourly, or Daily. For further guidance on assignment strategy, see Intune assignments: User groups vs. Device groups.
- Review + Create: Review the deployment and click on Create.
Sync Intune Policies
The device check-in process might not begin immediately. If you’re testing this policy on a test device, you can manually kickstart Intune sync from the device itself or remotely through the Intune admin center.
Alternatively, you can use PowerShell to force the Intune sync on Windows devices. Restarting the device is another way to trigger the Intune device check-in process.
End User Experience
After the deployment is completed successfully, the specified local user account will be enabled, and a complex password will be set.
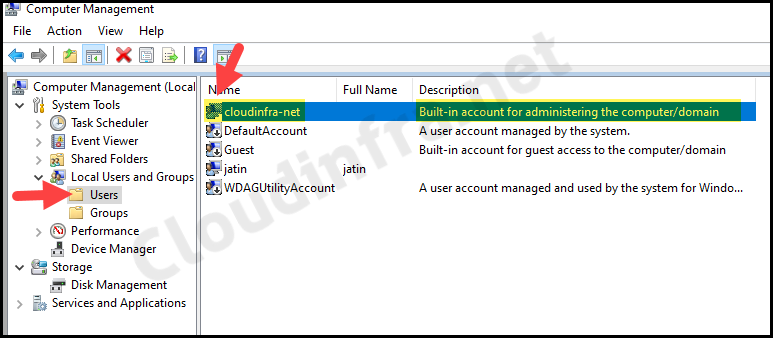
- Click on Start > search for Computer Management.
- Then go to Local Users and Groups > Users.
- Check if cloudinfra-net local admin account has been enabled.
Monitor the Script package
- Sign in to the Intune admin center > Devices > Scripts and Remediations.
- Click on the Remediation script package you want to monitor—for example, Restart Device Everyday Scheduled Task.
- Go to the Overview page and check the Detection Script and Remediation Script status.
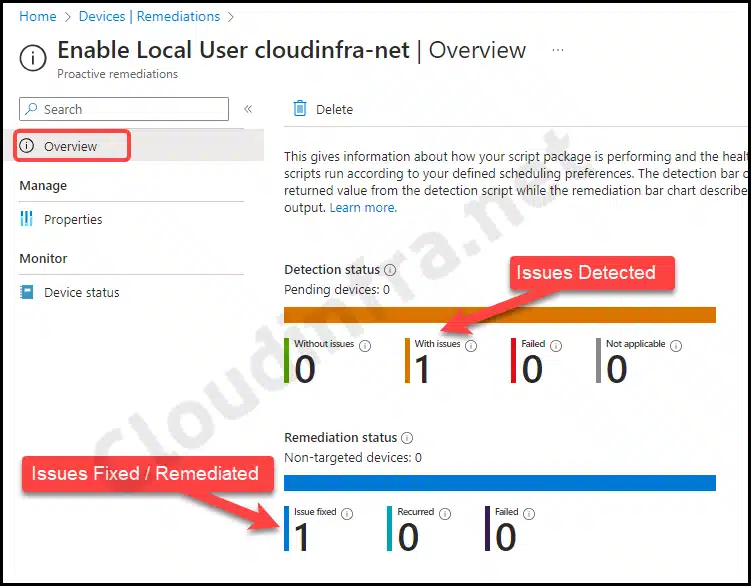
- The screenshot below shows that our Detection script has identified issues, specifically detecting that the local admin account was disabled. The Remediation Status indicates that the issue has been resolved with an Issue Fixed. This suggests that the remediation PowerShell script successfully reset the password and enabled the local admin account.
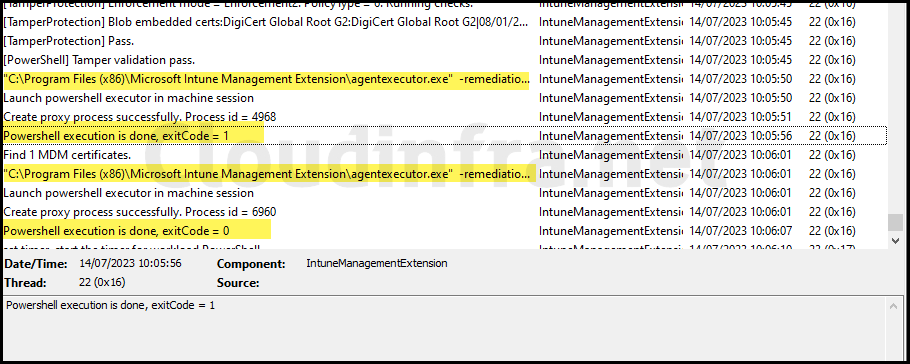
Find Intune Device Remediation Logs
To access Intune device remediation logs and locate the log file related to this script package deployment, follow these steps:
- Browse to C:\ProgramData\Microsoft\IntuneManagementExtension\Logs.
- Look for this directory’s most recent version of the IntuneManagementExtension.log file.
- For a more user-friendly log viewing experience, consider using a tool like CMTrace.
Conclusion
In this blog post, we’ve explored how to enable the built-in local administrator account using Intune Device Remediations, which offers an alternative approach to achieving this compared to Settings Catalog.
Both approaches are effective. The alternative method using Intune remediations involves PowerShell scripts that initially reset the password of the local administrator account to ensure it meets password complexity requirements before enabling the account.

This is a great article! Really thorough, including monitoring/logs was the key for me.
Thanks for this! But what happened if powershell is blocked on the devices? Is there any other ways to do it? Also is there an easy way to rename the administrator default admin account with Intune?
Hi Valentino, You could use a settings catalog policy Accounts Enable Administrator Account status to enable or disable Administrator account. For renaming the default administrator account on Windows, there is another settings catalog policy called Accounts Rename Administrator Account. You can refer to below posts for further guidance on this.
https://cloudinfra.net/enable-disable-built-in-administrator-account-using-intune/
https://cloudinfra.net/rename-built-in-administrator-account-using-intune