In this blog post, I will show you the steps to enable/disable built-in administrator account using Intune. Windows computers have an Administrator account (SID S-1-5-domain-500, display name Administrator), this is the first account created during the Windows installation.
The Administrator account has full control of the files, directories, services, and other resources on the local device. The default Administrator account can’t be deleted or locked out but can be renamed or disabled. An Administrator account can’t be removed from the Administrators group.
Best practice is to use a non-administrator account to log on to the PC and elevate to an administrator account when required, e.g., installing applications or performing configuration tasks on your device.
However, if you are using Windows LAPS and managing a built-in Administrator account, It must be enabled before you can deploy the LAPS policy to the device.
This blog post will explore two methods for enabling the built-in local administrator account. The first approach involves using a Device Configuration Profile, and the alternative method is through Intune device remediations.
Contents
Enable/Disable Built-in Administrator Account Using Intune
Let’s check the steps to enable or disable the built-in local administrator account on Windows 10/11 devices using Intune admin center.
- Sign in to the Intune admin center > Devices > Configuration > Create > New Policy.
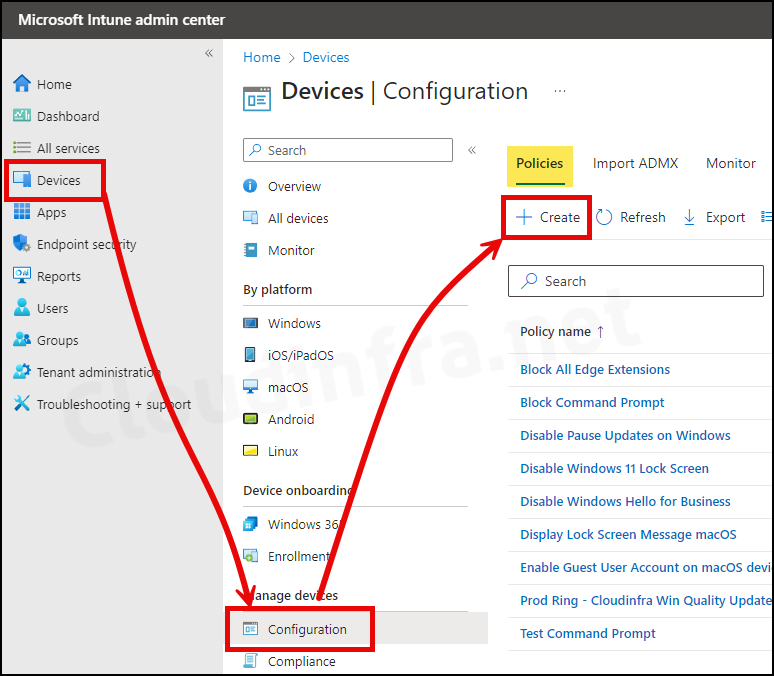
- Select Platform as Windows 10 and later
- Profile type as Settings Catalog
- Click on the Create button.
- Basics: Provide a Name and Description of the profile. Click on Next.
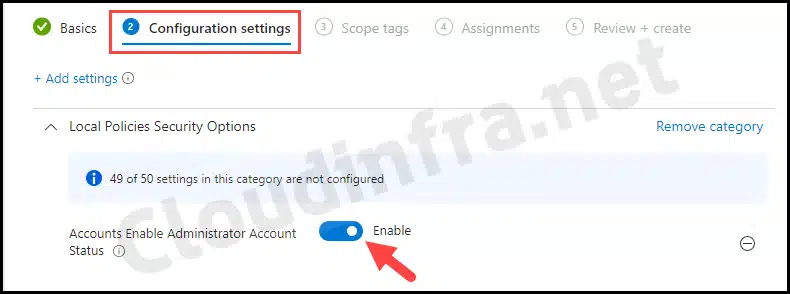
- Configuration settings: Click on the Add settings link, search for Local Policies Security Options, and Check the Accounts Enable Administrator Account status policy setting. Then, toggle the switch to Enable.
The OMA-URI setting which is used in the background for managing built-in local Administrator account is: ./Device/Vendor/MSFT/Policy/Config/LocalPoliciesSecurityOptions/Accounts_EnableAdministratorAccountStatus
Policy CSP – LocalPoliciesSecurityOptions
- Scope tags: Scope tags can control which objects are visible to the admins. Currently, we do not have this requirement to restrict this deployment. Click on Next to proceed to the next step.
- Assignments : Click Add groups and select the Entra security group containing Windows 10/11 devices.
- Review + Create: Review the deployment and click on Create.
Sync Intune Policies
The device check-in process might not begin immediately. If you’re testing this policy on a test device, you can manually kickstart Intune sync from the device itself or remotely through the Intune admin center.
Alternatively, you can use PowerShell to force the Intune sync on Windows devices. Restarting the device is another way to trigger the Intune device check-in process.
Monitoring Deployment Progress
To monitor the deployment progress of a Device configuration profile, follow the below steps:
- Sign in to the Intune admin center > Devices > Configuration.
- Choose the Device Configuration profile you want to work with, and at the top of the page, you’ll see a quick view of the Success, Failure, Conflict, Not Applicable, and In Progress status.
- Click on View report to access more detailed information.
End User Experience
Let’s check the result of this policy from one of the target devices:
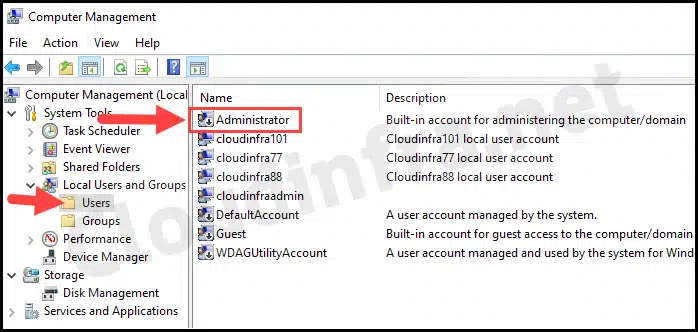
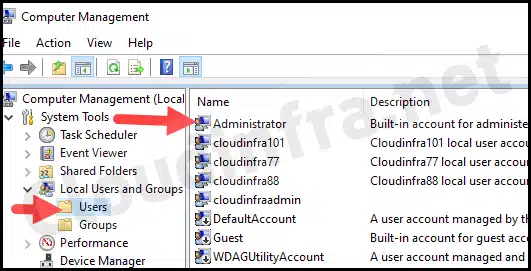
- Go to Start > search for Computer Management.
- Then go to Local Users and Groups > Users.
- Check the status of the Administrator Account; it should now be Enabled.
Troubleshooting
Even after applying this policy, a built-in Administrator account may still not be enabled. The deployment’s status may show an Error Code 65000. Event Viewer logs also show that the deployment has failed.
- Go to the Device and Click Start > Search for Event Viewer.
- Go to Applications and Services Logs > Microsoft > Windows > DeviceManagement-Enterprise-Diagnostics-Provider > Admin.
MDM ConfigurationManager: Command failure status. Configuration Source ID: (7CCD9C30-BFE5-4CE3-97C8-FC5E16474D01), Enrollment Name: (MDMDeviceWithAAD), Provider Name: (Policy), Command Type: (Add: from Replace or Add), CSP URI: (./Device/Vendor/MSFT/Policy/Config/LocalPoliciesSecurityOptions/Accounts_EnableAdministratorAccountStatus), Result: (Unknown Win32 Error code: 0xc000006c).
Error Event ID 404
The error message provided doesn’t help much. On the device itself, we observed an Error Event ID 404, and in the Intune admin center, the Error code is 65000. Upon re-checking Microsoft’s documentation, it was discovered that it won’t be enabled if the local built-in Administrator account doesn’t meet password complexity requirements.
To fix this issue, refer to the blog post: Enable/Disable Local Admin Account Using Intune Remediations, which shows a different way of Enabling a built-in Administrator account by setting a complex password first to meet the password complexity requirements.
Windows Registry
In most scenarios, checking the Windows registry to verify policy deployment may not be necessary. The Intune admin center is the recommended place to monitor the policy. However, as an advanced troubleshooting step, you can check the Windows registry to confirm if the policy has been applied successfully.
- Open the Registry Editor.
- Navigate to HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\PolicyManager\providers\AdministratorGUID\default\Device\LocalPoliciesSecurityOptions
- You will find a registry entry named Accounts_EnableAdministratorAccountStatus on the right-hand side with the value 1. This confirms that Intune successfully enabled the built-in administrator account.
Conclusion
In this blog post, we have learnt the steps to Enable or Disable a built-in local administrator account. If you enable a local administrator account, ensure the built-in local administrator meets password complexity requirements; otherwise, you may get Error 65000 shown on the Intune admin center after you deploy the device configuration profile.

Hello,
How did you set the password of local administrator account to meet the complexity requirement? Manually resetting it or by Intune? Is the complexity requirement of Local Security Policy or Intune?
Regards
I did changed the password manually on the device but if you have a perform this on devices in bulk then you could create a powershell script and using that change password of the Administrator account to meet complexity requirements. I believe its a local security policy which does not allow a simple password for Administrator account.
[Update]: I have created a blog post on how to Enable/Disable built in Administrator account using Intune Proactive Remediations which used Powershell scripts. Hope this will help you to fix this issue: https://cloudinfra.net/enable-disable-local-admin-account-using-intune-remediations/
Hi Jatin,
This policy doesn’t work when Security Baselines are configured. Do you know which Security Baseline setting is blocking this Configuration Profile?
https://learn.microsoft.com/en-us/mem/intune/protect/security-baseline-settings-mdm-all?pivots=mdm-november-2021
Kind regards,
Wander
Under Local Policies Security Options you have to change “User Account Control Behavior of the Elevation Prompt for Standard Users” to “Prompt for credentials”.