In this blog post, I will show you Intune policies to configure UAC (User account control) using Intune. User Account Control (UAC) is a security feature in Windows that helps prevent unauthorized changes to the operating system. It does this by prompting users for permission or an administrator password before allowing actions that could potentially affect the computer’s stability or security.
Key Functions of UAC
- Prevent Unauthorized Changes: UAC stops applications and processes from making changes to system settings or files without explicit permission.
- Run Applications with Least Privilege: By default, even administrator accounts run applications with standard user privileges. Elevated permissions are granted only when approved by the user.
- Enhance Security: Limits the ability of malware to compromise the system by requiring user consent for critical actions.
How UAC Prompts Work
- Standard Users: Must enter an administrator’s username and password to proceed.
- Administrators: Receive a prompt asking to allow or deny the action.
Contents
Configure UAC (User Account Control) Intune Policy
Let’s configure UAC (User account control) on Windows 10/11 computers using an Intune Policy:
- Sign in to Intune admin center > Devices > Windows > Configuration > Create > New Policy.
- Platform: Windows 10 and later
- Profile type: Settings catalog
- Click Create.
- On the Basics tab, provide a Name and Description of the policy and click Next.
- On Configuration settings tab, click on + Add settings and use the Settings picker to search using Local Policies security options keyword and select Local Policies security options category. Scroll down at the end to find all User Account Control related settings.
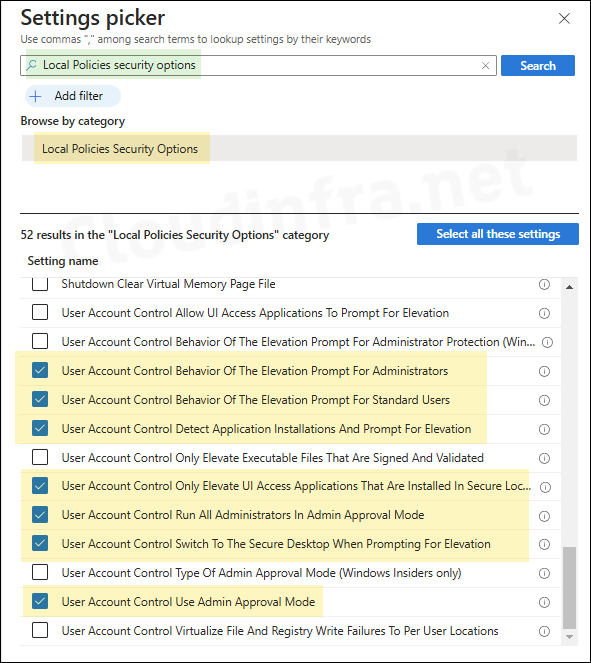
Refer to the Microsoft documentation to read detailed information on each User Account Control setting: User Account Control settings list.
| Setting Name | Description |
|---|---|
| User Account Control Switch To The Secure Desktop When Prompting For Elevation | Enabled |
| User Account Control Only Elevate UI Access Applications That Are Installed In Secure Locations | Enabled: Application runs with UIAccess integrity only if it resides in secure location. |
| User Account Control Run All Administrators In Admin Approval Mode | Enabled |
| User Account Control Use Admin Approval Mode | Enable |
| User Account Control Detect Application Installations And Prompt For Elevation | Enable |
| User Account Control Behavior Of The Elevation Prompt For Standard Users | Prompt for credentials Prompt for consent on the secure desktop Automatically deny elevation requests |
| User Account Control Behavior Of The Elevation Prompt For Administrators | Elevate without prompting Prompt for credentials on the secure desktop Prompt for consent on the secure desktop Prompt for credentials Prompt for consent Prompt for consent for non-Windows binaries (default) |
| Other User Account Control (UAC) Settings | Description |
|---|---|
| User Account Control Allow UI Access Applications To Prompt For Elevation | This policy setting controls whether User Interface Accessibility (UIAccess or UIA) programs can automatically disable the secure desktop for elevation prompts used by a standard user. • Enabled: UIA programs, including Windows Remote Assistance, automatically disable the secure desktop for elevation prompts. If you do not disable the “User Account Control: Switch to the secure desktop when prompting for elevation” policy setting, the prompts appear on the interactive user’s desktop instead of the secure desktop. • Disabled: (Default) The secure desktop can be disabled only by the user of the interactive desktop or by disabling the “User Account Control: Switch to the secure desktop when prompting for elevation” policy setting. |
| User Account Control Behavior Of The Elevation Prompt For Administrator Protection (Windows Insiders only) | User Account Control: Configure type of Admin Approval Mode. This policy setting controls whether Administrator protection is applied to admin approval mode elevations. If you change this policy setting, you must restart your computer. This policy is only supported on Windows Desktop, not Server. The options are: • Admin Approval Mode is running in legacy mode (default). • Admin Approval Mode is running with Administrator protection. This setting is only available to Windows Insiders |
| User Account Control Type Of Admin Approval Mode (Windows Insiders only) | User Account Control: Configure type of Admin Approval Mode. This policy setting controls whether Administrator protection is applied to admin approval mode elevations. If you change this policy setting, you must restart your computer. This policy is only supported on Windows Desktop, not Server. The options are: • Admin Approval Mode is running in legacy mode (default). • Admin Approval Mode is running with Administrator protection. This setting is only available to Windows Insiders |
| User Account Control Virtualize File And Registry Write Failures To Per User Locations | Virtualize file and registry write failures to per-user locations This policy setting controls whether application write failures are redirected to defined registry and file system locations. This policy setting mitigates applications that run as administrator and write run-time application data to %ProgramFiles%, %Windir%, %Windir%\system32, or HKLM\Software. The options are: • Enabled: (Default) Application write failures are redirected at run time to defined user locations for both the file system and registry. • Disabled: Applications that write data to protected locations fail. |
| User Account Control Detect Application Installations And Prompt For Elevation | Detect application installations and prompt for elevation This policy setting controls the behavior of application installation detection for the computer. The options are: Enabled: (Default) When an application installation package is detected that requires elevation of privilege, the user is prompted to enter an administrative user name and password. If the user enters valid credentials, the operation continues with the applicable privilege. Disabled: Application installation packages are not detected and prompted for elevation. Enterprises that are running standard user desktops and use delegated installation technologies such as Group Policy Software Installation or Systems Management Server (SMS) should disable this policy setting. In this case, installer detection is unnecessary. |
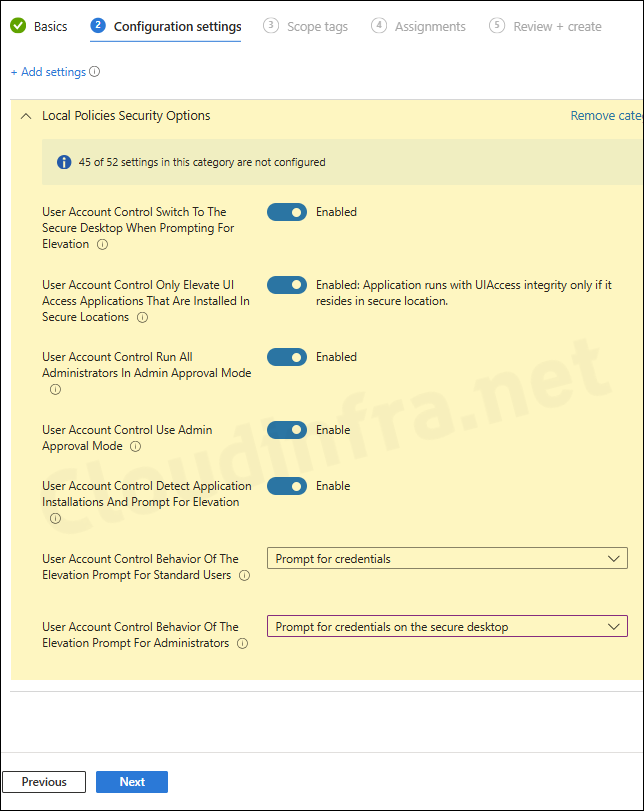
I have configured and deployed below UAC settings using Intune. You can go through other UAC settings information and add it to the configuration settings tab as per your requirements.
- Scope tags (optional): A scope tag in Intune is an RBAC label you add to resources (policies, apps, devices) to limit which admins can see and manage them. For more Information, read: How to use Scope tags in Intune.
- Assignments: Assign the policy to Entra security groups that contain the target users or devices. As a best practice, pilot with a small set first; once validated, roll it out more broadly. For guidance on assignment strategy, see Intune assignments: User groups vs. Device groups.
- Review + create: Review the deployment summary and click Create.
Monitoring UAC Policy
- Sign in to the Intune admin center > Devices > Configuration.
- Select the Device Configuration profile you want to work with, and at the top of the page, you’ll see a quick view of the Success, Failure, Conflict, Not Applicable, and In Progress status.
- Click on View report to access more detailed information.
Sync Intune Policies
The device check-in process might not begin immediately. If you’re testing this policy on a test device, you can manually kickstart Intune sync from the device itself or remotely through the Intune admin center.
Alternatively, you can use PowerShell to force the Intune sync on Windows devices. Restarting the device is another way to trigger the Intune device check-in process.
End User Experience
After the deployment is completed successfully, UAC settings configured in the Intune policy will be applied to the target device. To verify and confirm, sign in as a standard user and attempt to make changes to any settings which requires administrator rights.
Since I will not be able to test every policy setting, for demonstration purposes, I will test the User Account Control behavior for the elevation prompt for standard users setting and show you the behavior and experience on the device. You can test other UAC settings as configured in your Intune policy and confirm whether they are working as intended.
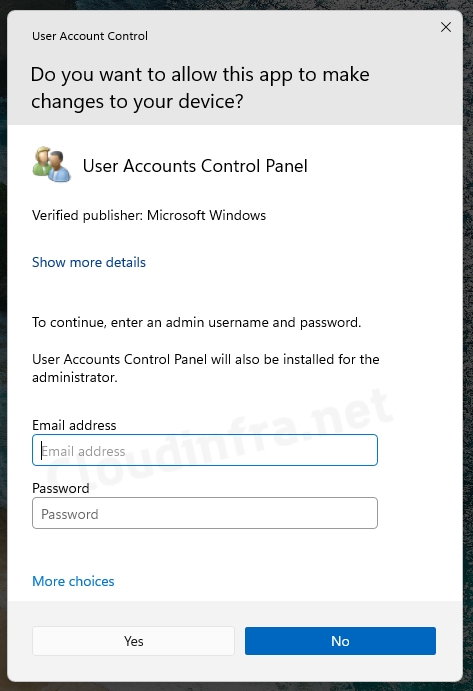
As we have configured the User Account Control behavior for the elevation prompt for standard users to Prompt for credentials, users will receive below pop-up message: Do you want to allow this app to make changes to your device ? If you want to proceed, you need to enter the administrator credentials, Else click on No to exit. This policy is working as expected.
The corresponding registry key and value for User Account Control behavior for the elevation prompt for standard users is HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Policies\System, under this a DWORD reg entry called ConsentPromptBehaviorUser with a value of 3.
ConsentPromptBehaviorUser value of 3 means it will prompt for credentials when a user will try to access or change a setting which requires administrator rights. Let’s modify this behavior using Intune Policy and instead of prompting user for credentials, we will deny the access. For this, update the setting User Account Control behavior for the elevation prompt for standard users to Automatically deny elevation requests and wait for the policy to sync.
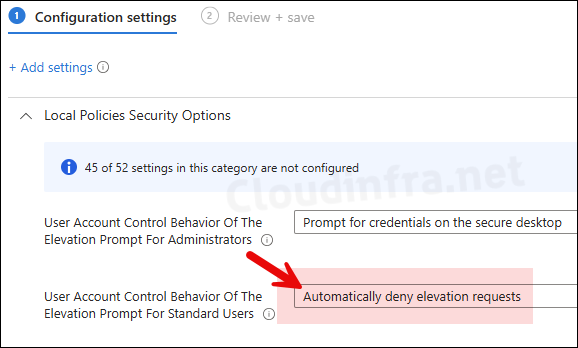
After Intune sync has been completed on the target device, you will find the registry entry ConsentPromptBehaviorUser value is now changed to 0. It means, user will be automatically denied from accessing or changing any setting and will not get any prompt to enter username and password for elevation of rights.
Instead, an error pop-up will be shown. In the next section, I will show you different error messages a standard user may get when they try to access or change any setting on the device.
You can go through registry entries under HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Policies\System which may correspond to the other UAC settings configured in the Intune policy.
Note
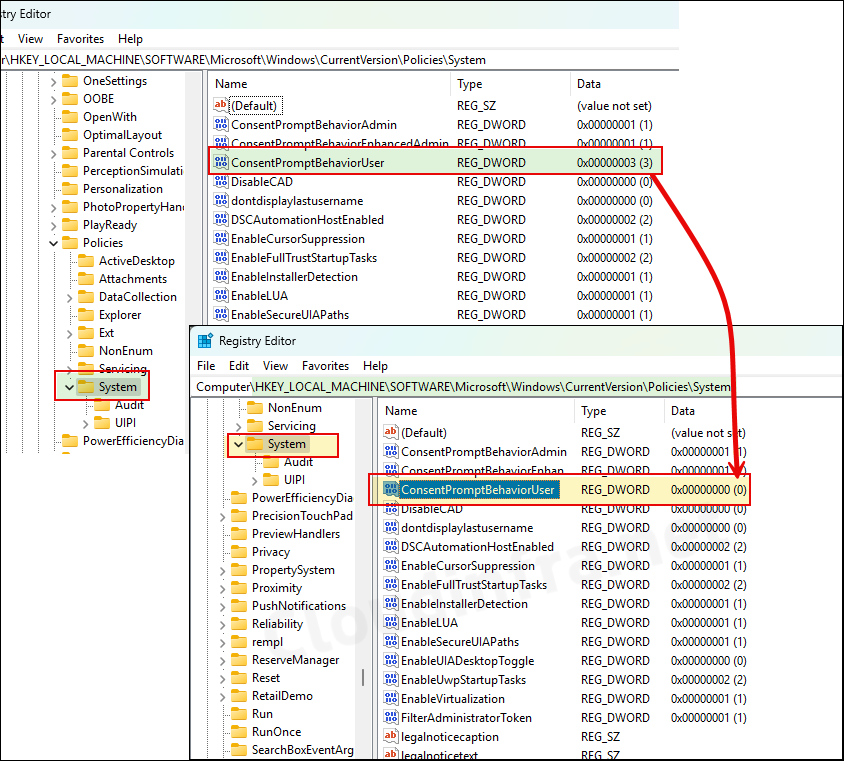
Now that we have configured a policy to automatically deny elevation requests for standard users, I will attempt to access or change settings on the target computer where this policy has been applied and observe the behavior.
- Open Control Panel and Click on Change account type under User accounts. I have received an error message: This program is blocked by group policy. For more information, contact your system administrator.
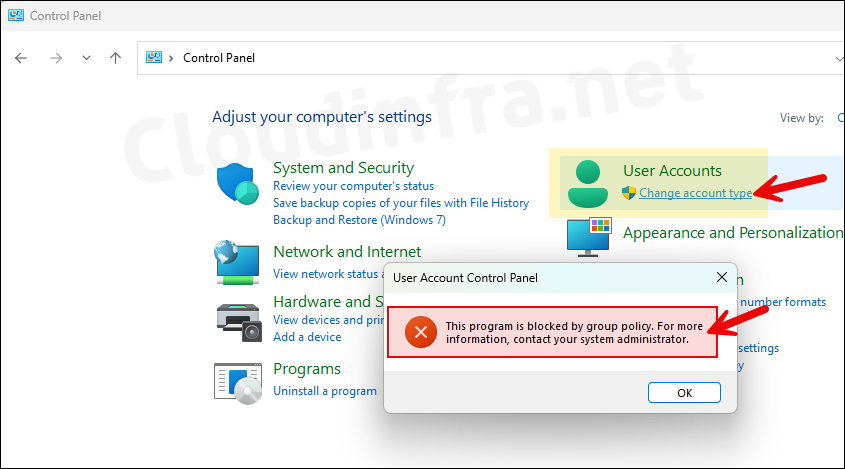
- Let’s perform another test, Go to Control Panel > Hardware and Sound > Click on Device Manager. You will get a warning message: You are logged on as a standard user. You can view device settings in Device Manager, but you must be logged on as an administrator to make changes.
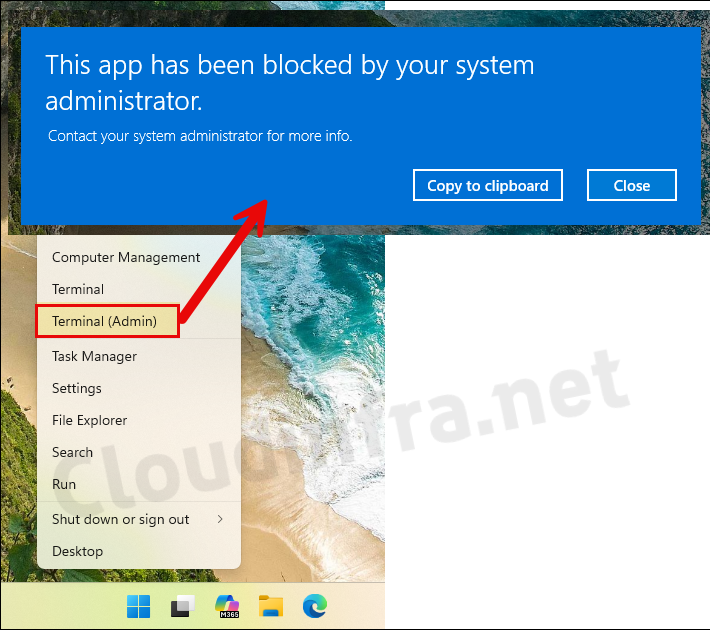
- Let perform third test and try to launch Terminal app as administrator. Right-click on Windows Icon > Select Terminal (admin), You will get a pop-up message: The app has been blocked by your system administrator. The app access is denied straight away.
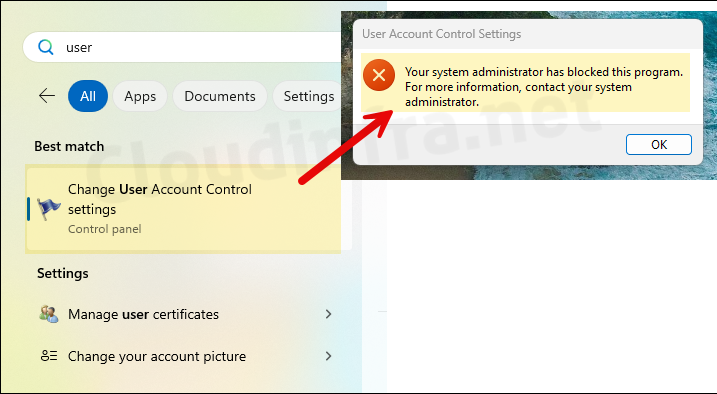
- As a standard user, I tried to access Change User Account control settings to test if it opens. I got an error: Your system administrator has blocked this program. For more information, contact your system administrator.
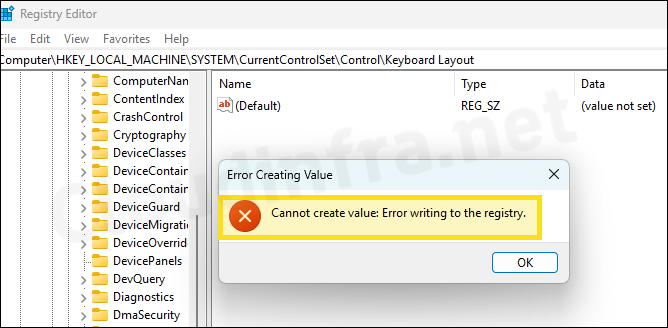
- When a standard user will try to create a registry key or value, there will be an error pop-up: Cannot create value: Error writing to the registry.