In this blog post, I will demonstrate Intune policies to enable/disable PUA protection in Edge using Intune. PUA (Potentially Unwanted Applications) in Microsoft Edge are software programs that might not be inherently malicious but can negatively impact performance, display unwanted ads, or make unauthorized changes to your device.
These applications often come bundled with other software or might present themselves as useful tools but include features that users generally find undesirable. For more information on PUA Protection in Edge, refer to the Microsoft docs link: PUA.
Contents
Enable/Disable PUA in Edge Manually
Let’s look at the PUA settings in Edge browser. You can easily enable or disable PUA protection in Edge by following below steps:
- Launch the Microsoft Edge browser
- Click on three dots (…) on the top-right hand side corner and go to Settings.
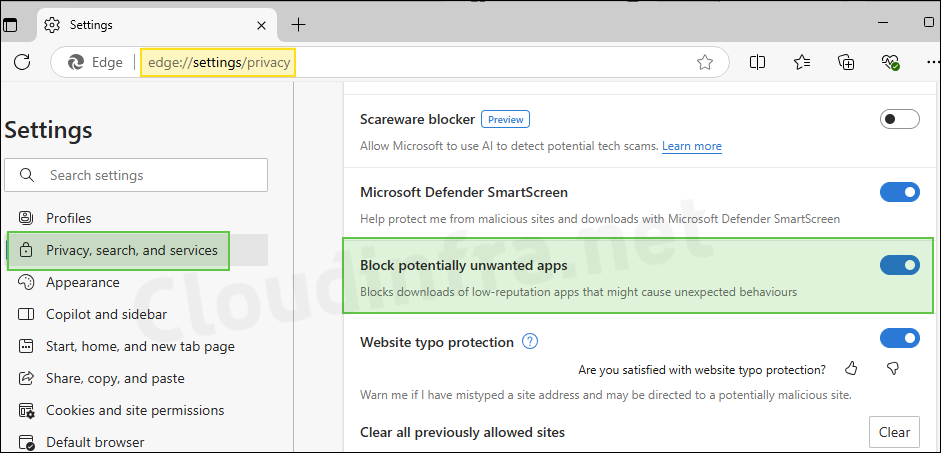
- Click on Privacy, search, and services > On the right-hand side you will find Block potentially unwanted apps setting. Use the toggle switch to enable or disable this feature.
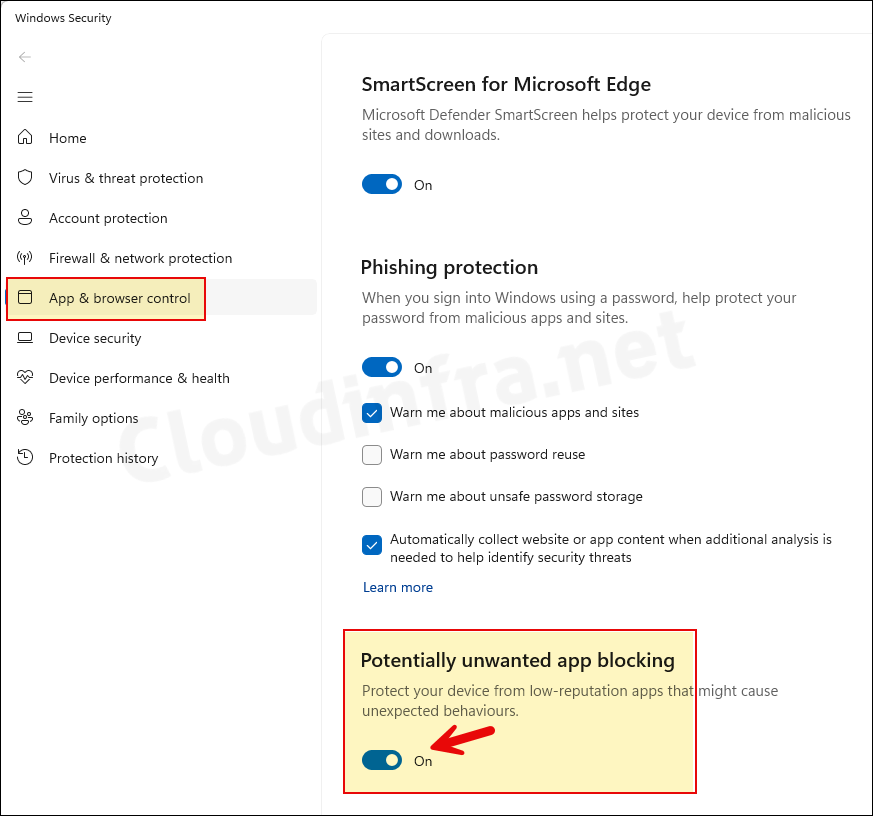
- Another option to enable or disable PUA Protection is to search in the Start menu for Windows Security and click on it to launch it. Go to App & browser control > Under Reputation-based protection, click on Reputation-based protection settings > Find Potentially unwanted app blocking setting and use the toggle switch to enable or disable it. Please note that this setting is dependent upon SmartScreen for Microsoft Edge, If you disable SmartScreen for Edge, PUA protection will also be disabled.
Enable/Disable PUA Protection in Edge Intune Policy
Now that we know how to enable or disable PUA protection in Edge browser manually. Let’s create an Intune policy to manage it centrally from Intune admin center.
- Sign in to Intune admin center > Devices > Windows > Configuration > Create > New Policy.
- Platform: Windows 10 and later
- Profile type: Settings catalog
- Click Create.
- On the Basics tab, provide a Name and Description of the policy and click Next.
- On Configuration settings tab, click on + Add settings and use the Settings picker to search using pua keyword and select Microsoft Edge\SmartScreen settings category. Select the policy, Configure Microsoft Defender SmartScreen to block potentially unwanted apps.
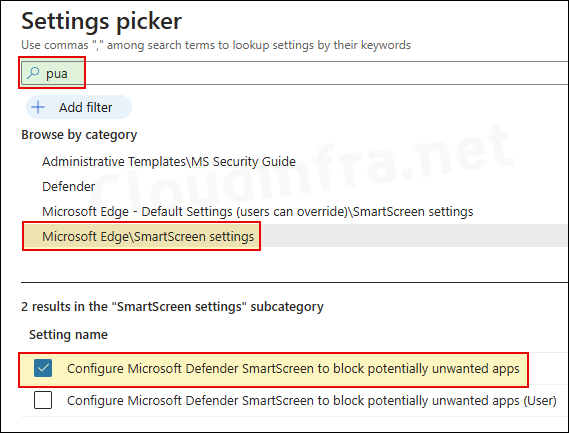
- Use the toggle switch to enable Configure Microsoft Defender SmartScreen to block potentially unwanted apps setting.
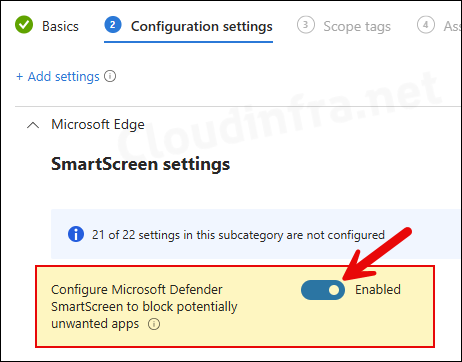
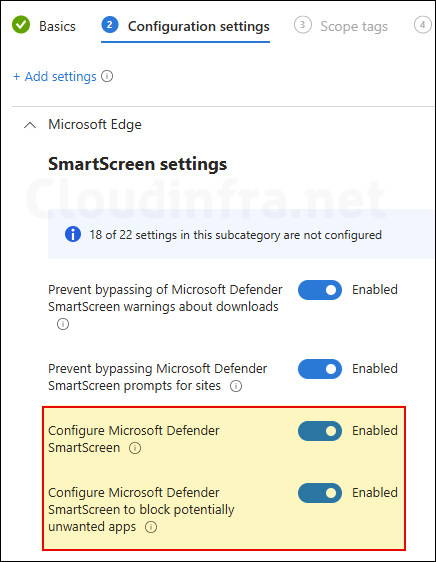
- Please note that PUA protection works with Edge SmartScreen. Ensure that Edge SmartScreen is enabled for PUA protection to work successfully. For Enabling SmartScreen in Edge, add another setting called Configure Microsoft Defender SmartScreen and set it to Enabled.
The other two settings that I have added under the Configuration settings are totally optional. You don’t have to use them for configuring PUA Protection. Let’s check out more details about these optional settings.
- Prevent bypassing of Microsoft Defender SmartScreen warnings about downloads: If you enable this setting, users will not be able to bypass or ignore the SmartScreen warnings and will be prevented from unverified downloads. For more information, refer to below official definition of the setting.
- Prevent bypassing Microsoft Defender SmartScreen prompts for sites: If you enable this setting, users will not be able to bypass or ignore SmarScreen warning about a site and will be blocked from accessing the site. For more information, refer to below official definition of the setting.
This policy lets you determine whether users can override Microsoft Defender SmartScreen warnings about unverified downloads. If you enable this policy, users in your organization can’t ignore Microsoft Defender SmartScreen warnings, and they’re prevented from completing the unverified downloads. If you disable or don’t configure this policy, users can ignore Microsoft Defender SmartScreen warnings and complete unverified downloads. This policy is available only on Windows instances that are joined to a Microsoft Active Directory domain; or on Windows 10 Pro or Enterprise instances that are enrolled for device management.
Official definition of Prevent bypassing of Microsoft Defender SmartScreen warnings about downloads setting
This policy setting lets you decide whether users can override the Microsoft Defender SmartScreen warnings about potentially malicious websites. If you enable this setting, users can’t ignore Microsoft Defender SmartScreen warnings and they are blocked from continuing to the site. If you disable or don’t configure this setting, users can ignore Microsoft Defender SmartScreen warnings and continue to the site. This policy is available only on Windows instances that are joined to a Microsoft Active Directory domain; or on Windows 10 Pro or Enterprise instances that are enrolled for device management.
Official definition of Prevent bypassing Microsoft Defender SmartScreen prompts for sites setting
Enable/Disable SmartScreen in Edge using Intune.
Blog Post
- Scope tags (optional): A scope tag in Intune is an RBAC label you add to resources (policies, apps, devices) to limit which admins can see and manage them. For more Information, read: How to use Scope tags in Intune.
- Assignments: Assign the policy to Entra security groups that contain the target users or devices. As a best practice, pilot with a small set first; once validated, roll it out more broadly. For guidance on assignment strategy, see Intune assignments: User groups vs. Device groups.
- Review + create: Review the deployment summary and click Create.
Monitoring PUA Protection Intune Policy
- Sign in to the Intune admin center > Devices > Configuration.
- Select the Device Configuration profile you want to work with, and at the top of the page, you’ll see a quick view of the Success, Failure, Conflict, Not Applicable, and In Progress status.
- Click on View report to access more detailed information.
Sync Intune Policies
The device check-in process might not begin immediately. If you’re testing this policy on a test device, you can manually kickstart Intune sync from the device itself or remotely through the Intune admin center.
Alternatively, you can use PowerShell to force the Intune sync on Windows devices. Restarting the device is another way to trigger the Intune device check-in process.
End User Experience
After the deployment is successfully completed, follow below steps to check and confirm if the Intune policy is applied successfully.
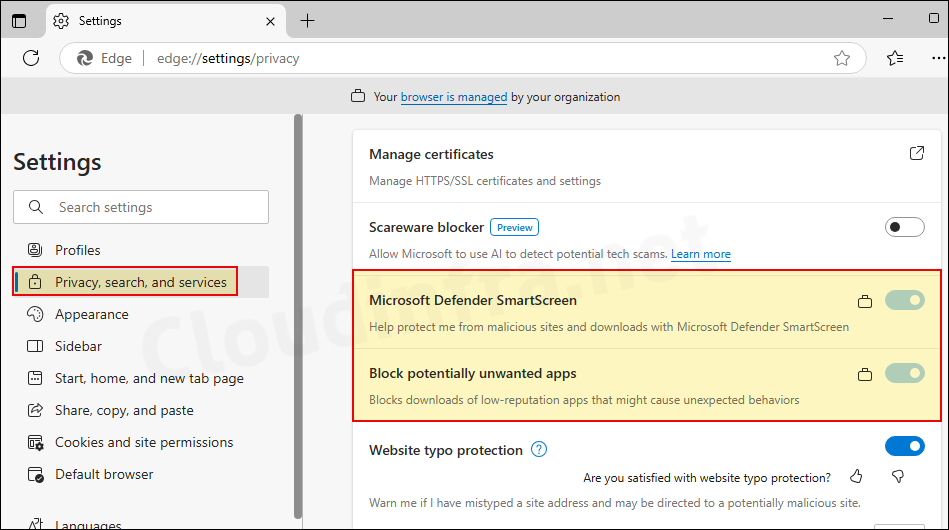
- Launch Microsoft Edge browser.
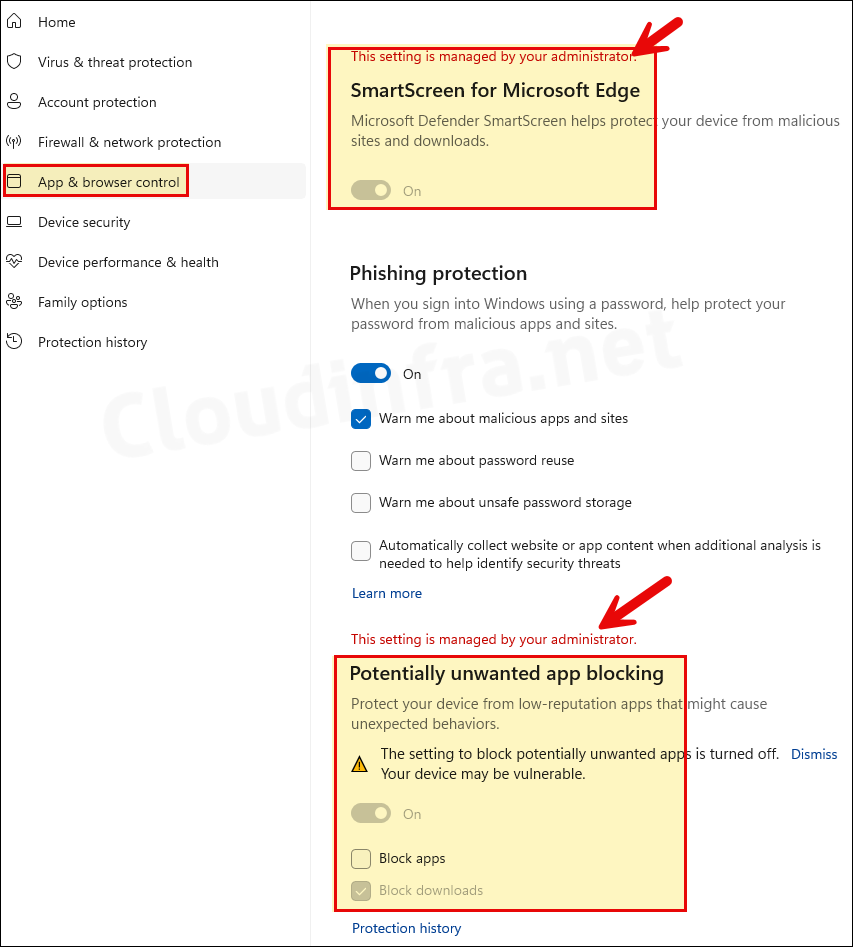
- In the Address bar, type edge://settings/privacy > Under Security, you will find that Microsoft Defender SmartScreen and Block Potentially unwanted apps are enabled and greyed out. This confirms that our Intune policy has been applied successfully.
- Search in the Start menu for Windows Security and click on it to launch it > Go to App & browser control > Under Reputation-based protection click on Reputation-based protection settings > SmartScreen for Microsoft Edge setting is enabled and greyed out. You will also find that Potentially unwanted app blocking setting is also enabled and greyed out.