In this blog post, I will show you the steps to block Microsoft store using Intune except winget. In my previous blog post, we have explored the steps to disable Microsoft Store app, which also disables Winget. If you want to disable Microsoft Store on Windows devices without affect Winget APIs for downloading and Installing apps, then please follow the steps in this blog post.
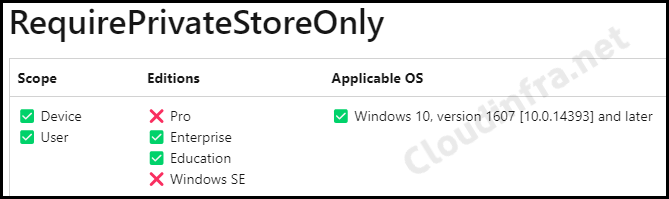
We will test a policy setting called Require Private Store Only, which restricts access to Microsoft Store. Link for Require Private Store only policy CSP. Please note that this policy only works for Windows Enterprise and Education Editions. If you want to block Microsoft store on Windows Professional (Pro) Edition, then refer to this post: #disable-block-microsoft-store-for-windows-pro-edition.
Contents
Steps to disable Microsoft Store using Intune Except Winget
- Sign in to the Intune admin center > Devices > Configuration > Create > New Policy.
- Select Platform as Windows 10 and later.
- Profile type: Settings Catalog.
- Basics: The basics tab will provide information about the device configuration profile, such as name and description.
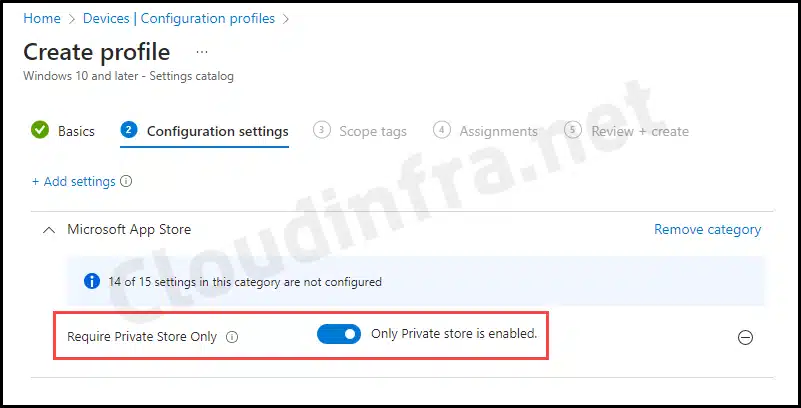
- Configuration settings: Click on + Add settings and then search for Microsoft App Store. This should list all settings related to the Microsoft App Store. Select Require Private Store Only and toggle the setting to Enable.
- Assignments: Click Add groups and select the Entra security group containing Windows 10/11 devices.
- Review + create: Review the deployment and click on Create.
Sync Intune Policies
The device check-in process might not begin immediately. If you’re testing this policy on a test device, you can manually kickstart the Intune sync from the device itself or remotely through the Intune admin center.
Alternatively, you can use PowerShell to force the Intune sync on Windows devices. Restarting the device is another way to trigger the Intune device check-in process.
End User Experience
Let’s see what happens from the end user’s perspective when the policy is successfully applied. Follow these steps:
- Click on the Start button and search for Microsoft Store and try to open it.
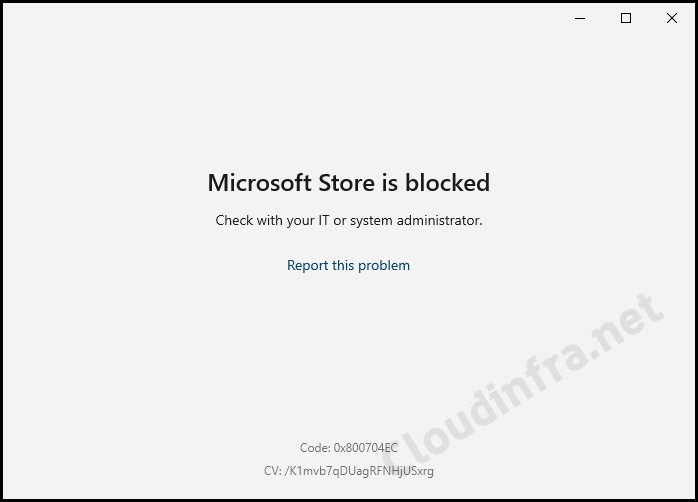
- When you open the Microsoft Store, you may encounter one of the following error messages:
- Microsoft Store is blocked. Please check with your IT or system administrator. Code: 0x800704EC.
- Try that again. The page could not be loaded. Please try again and refresh the page. The code is 0x80131500.
- This place is off-limits, Not sure how you got here, but there’s nothing for you here. Report this problem. Refresh this Page.
FAQs
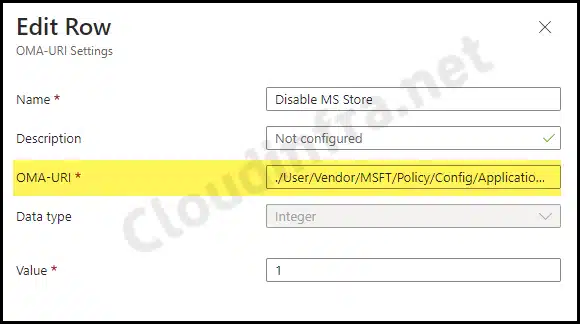
OMA-URI setting to block Microsoft Private Store
Name: Disable MS Store
OMA-URI: ./User/Vendor/MSFT/Policy/Config/ApplicationManagement/RequirePrivateStoreOnly
Data Type: Integer
Value: 1
Locate RequirePrivateStoreOnly Registry entry
To locate RequirePrivateStoreOnly registry entry, please follow below steps:
> Go to Start > Search for Registry Editor. Click on it to open.
>Navigate to HKEY_LOCAL_MACHINE\SOFTWARE\Policies\Microsoft\WindowsStore registry key.
>On the right-hand side, you will find a DWORD registry entry called
RequirePrivateStoreOnly
The value of RequirePrivateStoreOnly will be either 0 or 1, depending on whether it’s disabled or enabled. If it’s set to 0, then it’s not enabled, and if it’s set to 1, that means the setting is enabled.
Logs related to Intune Policy deployment
To find the logs related to your Intune deployment, Open Event Viewer > Application and Services logs > Microsoft > Windows > Devicemanagement-Enterprise-Diagnostics-Provider > Admin folder.
Search for Event ID 813 or 814 and go through the logs to find the one related to this deployment.
Block the Microsoft Store using Group Policy
You can also easily block Microsoft Store using Group policy using below steps:
1. Press Windows + R to open Run dialog box.
2. Type gpmc.msc and press Enter to open the Group policy management console.
3. Go to User Configuration or Computer Configuration > Administrative templates > Windows Components > Store
4. Select Only display the private store within the Microsoft Store app and edit this setting.
5. Select Enabled to enable this setting and press OK.
Other Microsoft App Store Settings available on the Intune admin center
| Setting Name | Detailed Information about the Policy setting |
|---|---|
| Allow All Trusted Apps | Detailed Information about the Policy-setting |
| Allow apps from the Microsoft app store to auto update | If you enable this setting and the “Allow all trusted apps to install” Policy, you can develop Microsoft Store apps and install them directly from an IDE. |
| Allow Developer Unlock | If you enable this policy, a Windows app can share app data with other instances of that app. Data is shared through the SharedLocal folder. This folder is available through the Windows—storage API. |
| Allow Game DVR | This setting enables or disables the Windows Game Recording and Broadcasting features. If you disable this setting, Windows Game Recording won’t be allowed. |
| Allow Shared User App Data | Disable turns off the launch of all apps from the Microsoft Store that came pre-installed or were downloaded. Apps won’t be updated. Your Store will also be disabled. Enable turns all of it back on. This setting applies only to Windows Enterprise and Education editions. |
| Block Non Admin User Install | If you enable this policy, non-Administrators cannot initiate installation of Windows app packages. Administrators who wish to install an app must do so from an Administrator context (for example, an Administrator PowerShell window). All users can still install Windows app packages via the Microsoft Store if permitted by other policies. |
| Disable Store Originated Apps | If you enable this policy, a Windows app can share data with other instances of that app. Data is shared through the SharedLocal folder, which is available through the Windows storage API. |
| Launch App After Log On | If you enable this policy setting, some of Windows Installer’s security features are bypassed. It permits installations to be completed that would be halted due to a security violation. |
| MSI Allow User Control Over Install | If you enable this policy setting, some of Windows Installer’s security features are bypassed. It permits installations to be completed that otherwise would be halted due to a security violation. |
| MSI Always Install With Elevated Privileges | If you enable this policy setting, privileges are extended to all programs. These privileges are usually reserved for programs assigned to the user (offered on the desktop), assigned to the computer (installed automatically), or made available in Add or Remove Programs in the Control Panel. This profile setting lets users install programs that require access to directories that the user might not have permission to view or change, including directories on highly restricted computers. |
| MSI Always Install With Elevated Privileges (User) | This policy setting appears both in the Computer Configuration and User Configuration folders. To make this policy setting effective, you must enable it in both folders. |
| Require Private Store Only | If you enable this setting, users won’t be able to view the retail catalog in the Microsoft Store but can view apps in the private store. |
Conclusion
Consider blocking access to the Microsoft Store in your company because it offers a wide range of non-productive apps. Additionally, using the Microsoft Store can complicate app management for your IT administrators.
Instead, it’s advisable to centralize app management through a platform like Microsoft Intune, which provides greater control. Furthermore, Microsoft has introduced a new app type in Microsoft Intune for improved app management: the Microsoft Store app (new).
You can select a Microsoft Store app (new) that connects with the Microsoft Store to search for apps and publish them directly via Intune. As Microsoft Store for Business is retiring, it is recommended that this app deployment method be switched to, which is much easier and faster than other app deployment methods in Intune.

One of my bloatware script removes Microsoft.Store from the appx with the other bloatware. This removes the actual app from the device.
I did start pushing Microsoft stock apps (Photos, Paint3d) via Intune. Will these apps auto update? Or do I need to remove the store app from the bloatware removal script and make sure its installed on the device?
Thanks for the help!
Hello CE,
The Microsoft Store is the primary source for installing and updating important system apps and drivers. If you remove the Microsoft Store, you’ll lose the ability update existing apps.
Some apps might rely on the Microsoft Store framework for updates and licensing. If you remove the Microsoft Store, these apps might not work properly or might not update correctly.
Windows updates can sometimes be distributed through the Microsoft Store. Removing it might complicate the update process or prevent you from accessing certain updates.