In this blog post, I will show you the steps to deploy trusted root certificate using Intune. Trusted Root Certification Authorities certificate store on Windows devices, by default contains public root certificates from various third parties that meet the requirements of the Microsoft Root Certificate Program. Certificates imported into this store are also referred to as root certificates.
A certificate can be used for authentication, authorization, or other purposes. You can either purchase a certificate from third-party vendors or issue one from an internal on-premises certificate authority. In both cases, a root certificate must be imported into the Trusted Root Certification Authorities store on the Windows device.
For well-known third-party vendors included in the Microsoft Root Certificate Program, their root certificates are built into the Windows operating system. Therefore, when you purchase a certificate from them and import it onto the device, it automatically completes the certificate chain and trusts the publisher.
When using an internal on-premises certificate authority, the trusted root certificate of your internal root CA does not exist on the device. To establish trust and complete the certificate chain, you must first export trusted root certificate from your internal CA and import it in the Trusted Root Certification Authorities certificate store.
In this blog post, I will show you the steps to export the root certificate from an internal on-premises certificate authority and deploy it to Intune-managed devices using a Trusted Certificate profile. Deploying a trusted root certificate is also a prerequisite when using SCEP and PKCS certificate deployment methods.
Export Trusted Root Certificate from Internal CA
Below are the steps to export the root CA certificate from the internal on-premise certificate authority (Root CA server).
- Login to Root CA server.
- Open command prompt as administrator and execute below command:
certutil -ca.cert <root certificate export location>
Example:
certutil -ca.cert c:\trusted_root.cer
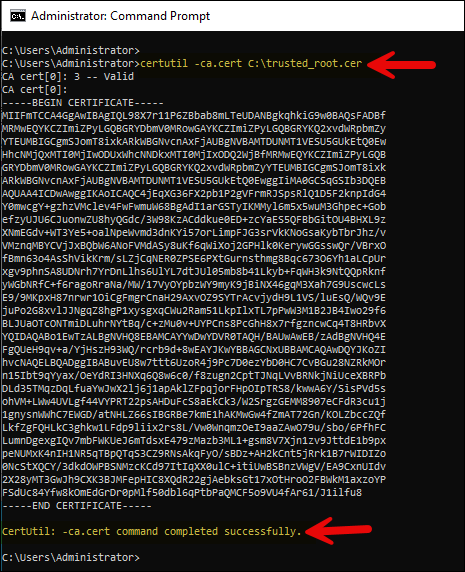
- Certificate is exported to the location c:\trusted_root.cer.
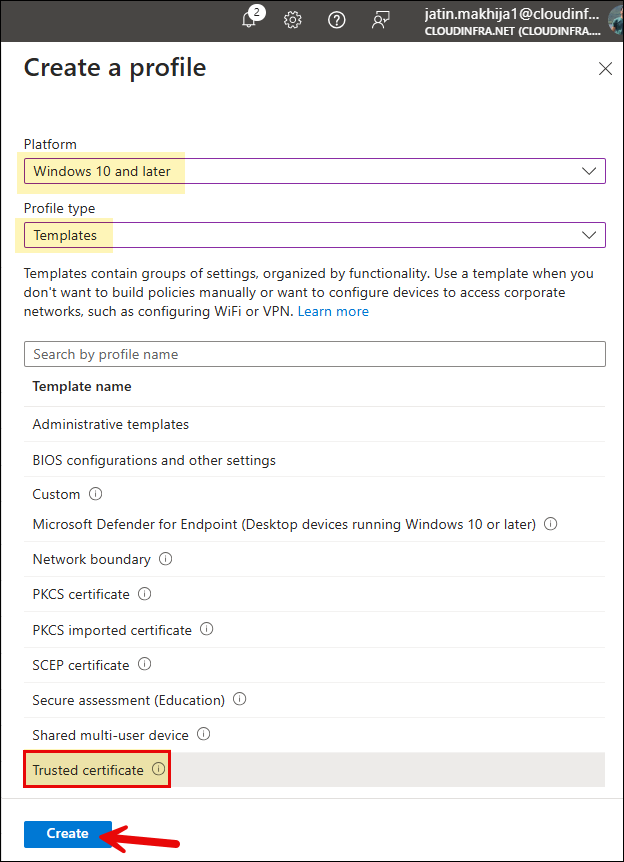
- Sign in to the Intune admin center > Devices > Windows > Configuration > Create > New Policy.
- Platform: Windows 10 and later.
- Profile type: Templates.
- Template name: Trusted certificate.
- Basics tab: Provide a name and description of the profile.
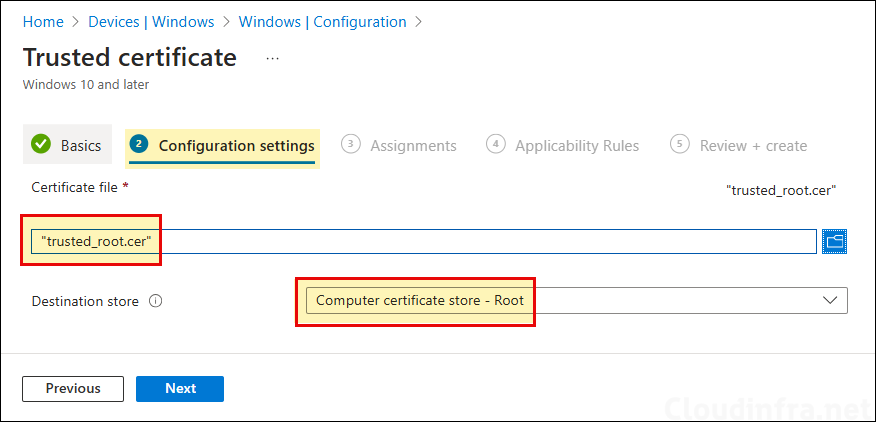
- Configuration settings: Browse to the trusted root certificate file trusted_root.cer and select the destination store as Computer certificate store – Root.
- Scope tags (optional): A scope tag in Intune is an RBAC label you add to resources (policies, apps, devices) to limit which admins can see and manage them. For more Information, read: How to use Scope tags in Intune.
- Assignments: Assign the profile to Entra security groups that contain the target users or devices. As a best practice, pilot with a small set first; once validated, roll it out more broadly. For guidance on assignment strategy, see Intune assignments: User groups vs. Device groups.
- Applicability Rules: Click Next.
- Review + create: Review the profile summary and click on Create.
Sync Intune Policies
The device check-in process might not begin immediately. If you’re testing this policy on a test device, you can manually kickstart Intune sync from the device itself or remotely through the Intune admin center.
Alternatively, you can use PowerShell to force the Intune sync on Windows devices. Restarting the device is another way to trigger the Intune device check-in process.
End User Experience
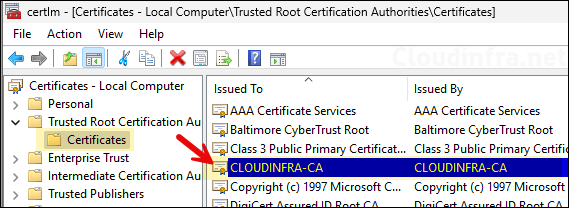
After the deployment is completed successfully, Open local certificate computer store to check if the certificate is deployed. Let’s check the steps:
- Sign in to the target Windows computer.
- Press Win + R to open the Run dialog box.
- Navigate to Trusted Root Certification Authorities certificate store > Certificates and check if the root CA certificate has been deployed. Below screenshot shows that the root certificate CLOUDINFRA-CA is successfully deployed.