In this post, I will show you the steps to block access to Windows registry using Intune. I will test an Intune Settings catalog policy prevent access to registry editing tools (User). Enabling this setting and deploying it to Intune-managed Windows devices will disable/block/prevent access to Windows registry editor (regedit) for the current user.
You will need to configure an additional setting with this, called Disable regedit from running silently. Setting this to Yes, will further restrict access to Windows registry by other methods, like command prompts or by using .reg files.
Contents
Block Access to Windows Registry Intune Policy
- Sign in to the Intune admin center >Devices > Configuration > Create > New Policy.
- Platform: Windows 10 and later.
- Profile type: Settings Catalog.
- Basics: Provide a Name and Description of the profile.
- Configuration settings: Click on + Add settings and search for Registry in the settings picker. Select Prevent access to registry editing tools (User) under the Administrative Templates\System category.
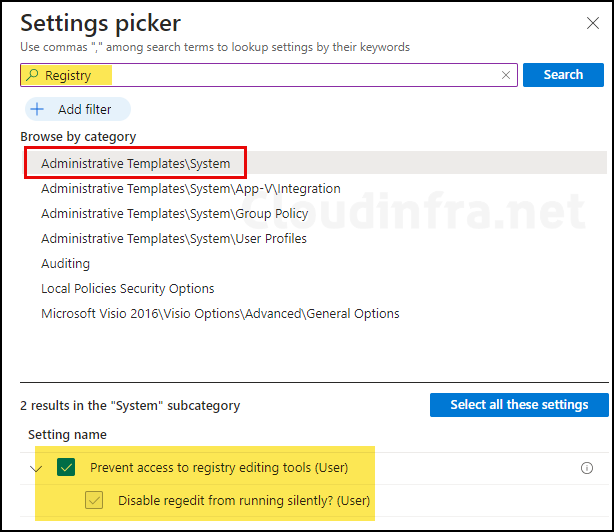
- Toggle the switch prevent access to registry editing tools (User) setting to Enabled. This will block access to Windows registry.
- Select Yes for disable regedit from running silently setting to further prevent registry access using alternative methods, such as a .reg file or a command prompt.
- Assignments: Assign this profile to an Entra security group containing users/devices.
- Review + create: Review the profile settings and click on Create.
Sync Intune Policies
The device check-in process might not begin immediately. If you’re testing this policy on a test device, you can manually kickstart the Intune sync from the device itself or remotely through the Intune admin center.
Alternatively, you can use PowerShell to force the Intune sync on Windows devices. Restarting the device is another way to trigger the Intune device check-in process.
Monitoring Deployment Progress
- Sign in to the Intune admin center >Devices > Configuration.
- Choose the Device Configuration profile you want to work with, and at the top of the page, you’ll see a quick view of the Success, Failure, Conflict, Not Applicable, and In Progress status.
- Click on View report to access more detailed information.
End User Experience
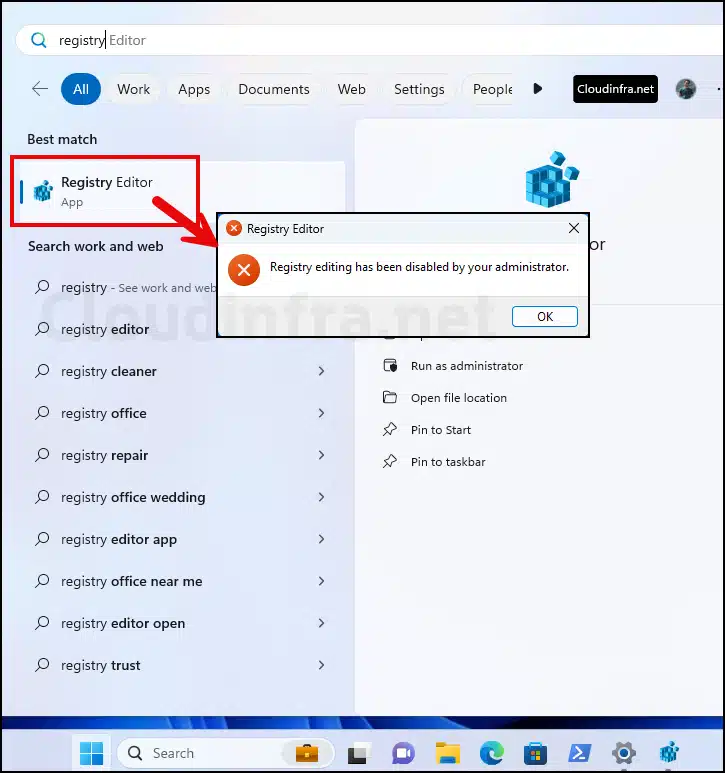
After the policy has been applied successfully, Launch Registry Editor either by searching in Start menu or by using regedit command on the Run dialog box. You will get an error message, Registry editing has been disabled by your administrator.
FAQs
What is the OMA-URI setting for blocking registry access?
./User/Vendor/MSFT/Policy/Config/ADMX_ShellCommandPromptRegEditTools/DisableRegedit
Data Type: String
Value: <enabled/> <data id=”DisableRegeditMode” value=”2″/>
What is the Group Policy setting for blocking registry access?
– Open Group Policy Management console > User Configuration > Administrative Templates > System
– On the right-hand side you will find a setting called Prevent access to registry editing tools. Double-click on it and set it to Enabled.
Can I block registry access using Registry Editor itself?
Yes, you can block registry access by creating the registry key and value:
– Navigate to HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Policies
– Right-click Policies > New > Key
– Name the new Key as System, and Under this key, create a DWORD registry entry called DisableRegistryTools and set its value to 2.
DisableRegistryTools = 0 (Registry editor will open as usual)
DisableRegistryTools = 1 (Registry Editor will not open in Interactive mode but can be started with Silent switch /s or executed through .reg files).
DisableRegistryTools = 2 (Registry editor will not open normally or by using Silent switches)
I want to read more about DisableRegedit.
You can read more about this policy at: ADMX_ShellCommandPromptRegEditTools Policy CSP – Windows Client Management | Microsoft Learn
