In this blog post, I will show you the steps to disable Bluetooth on Windows using Intune. Bluetooth connections can potentially be vulnerable to hacking and unauthorized access. Disabling Bluetooth when you’re not actively using it reduces the risk of someone trying to exploit vulnerabilities in Bluetooth protocols to gain access to your device or data.
Please note that bluetooth is not disabled on Windows devices by default. You can easily disable bluetooth by using a Settings catalog policy setting called Allow Bluetooth.
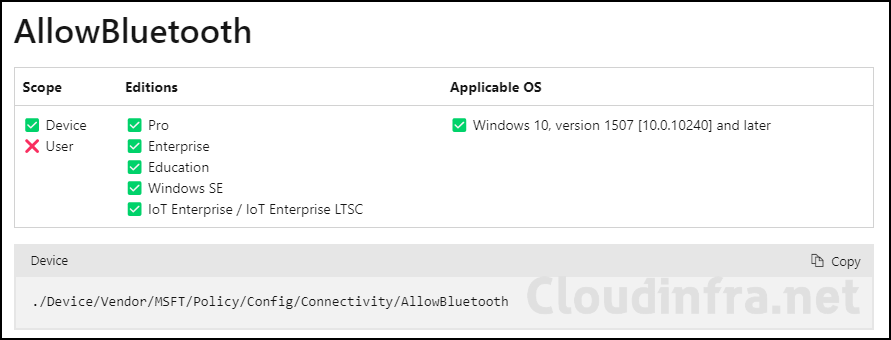
You can learn more about this setting by visiting the link Allow Bluetooth OMA-URI, which offers additional information. Below screenshot shows this policy is applicable on Windows 10 version 1507 and later including professional edition.
Contents
Disable Bluetooth Intune Policy
- Sign in to the Intune admin center > Devices > Configuration > Create > New Policy.
- Platform: Windows 10 and later.
- Profile type: Settings Catalog.
- Basics: Provide a Name and Description of the profile.
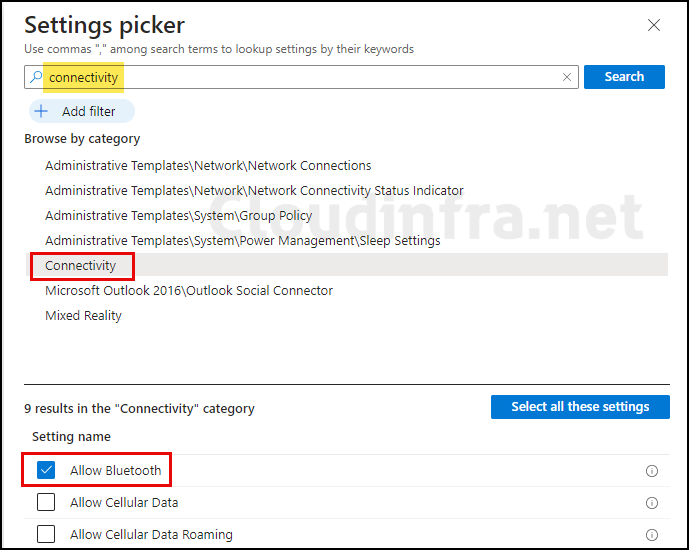
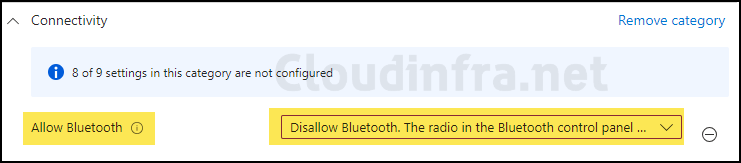
- Configuration settings: Click on + Add settings and search for connectivity under the Settings picker. Under the Connectivity category, you will find an Allow Bluetooth setting. Select it to add it to the Configuration settings page.
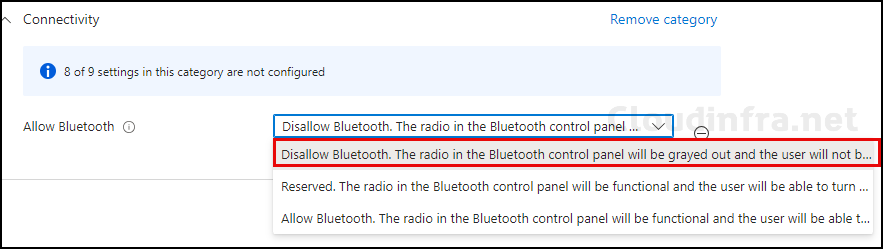
You will get the below three options for the Allow Bluetooth setting. As we have to disable Bluetooth, we will choose the first option, Disable Bluetooth.
- Disable Bluetooth, The radio in the Bluetooth control panel will be greyed out, and the user will not be able to turn Bluetooth on.
- Reserved, The radio in the Bluetooth control panel will be functional, and the user will be able to turn Bluetooth on.
- Allow Bluetooth, The radio in the Bluetooth control panel will be functional, and the user will be able to turn Bluetooth on.
- Scope tags (optional): A scope tag in Intune is an RBAC label you add to resources (policies, apps, devices) to limit which admins can see and manage them. For more Information, read: How to use Scope tags in Intune.
- Assignments: Assign the policy to Entra security groups that contain the target users or devices. As a best practice, pilot with a small set first; once validated, roll it out more broadly. For guidance on assignment strategy, see Intune assignments: User groups vs. Device groups.
- Review + create: Review the deployment summary and click Create.
Sync Intune Policies
The device check-in process might not begin immediately. If you’re testing this policy on a test device, you can manually kickstart the Intune sync from the device itself or remotely through the Intune admin center.
Alternatively, you can use PowerShell to force the Intune sync on Windows devices. Restarting the device is another way to trigger the Intune device check-in process.
Monitoring Deployment Progress
- Sign in to the Intune admin center > Devices and then select Configuration.
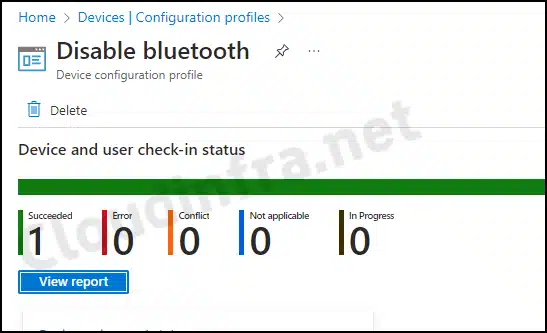
- Choose the Device Configuration profile you want to work with, and at the top of the page, you’ll see a quick view of the Success, Failure, Conflict, Not Applicable, and In Progress status.
- Click on View report to access more detailed information.
End User Experience
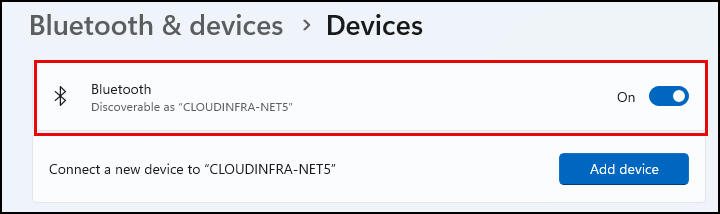
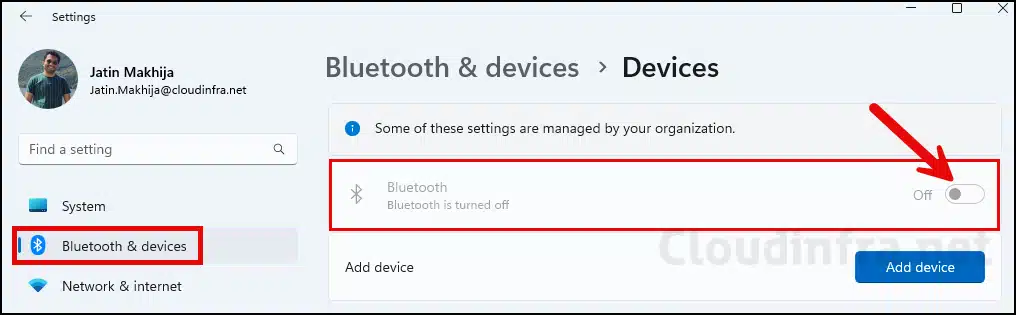
Once this policy has been successfully applied to target devices, Bluetooth will be disabled for all users. Users will also not be able to switch it on. I have captured before and after screenshots to show you the policy effect on the device:
- Before disabling Bluetooth on a Windows 11 device.
- After disabling Bluetooth on a Windows 11 device
Other Bluetooth settings available in Settings Catalog
Not only can you enable or disable Bluetooth on Windows 10/11 devices using Intune, but you can also configure additional settings related to Bluetooth. To find these other Bluetooth options, use the settings picker and search for Bluetooth. Then, click on the Bluetooth category.
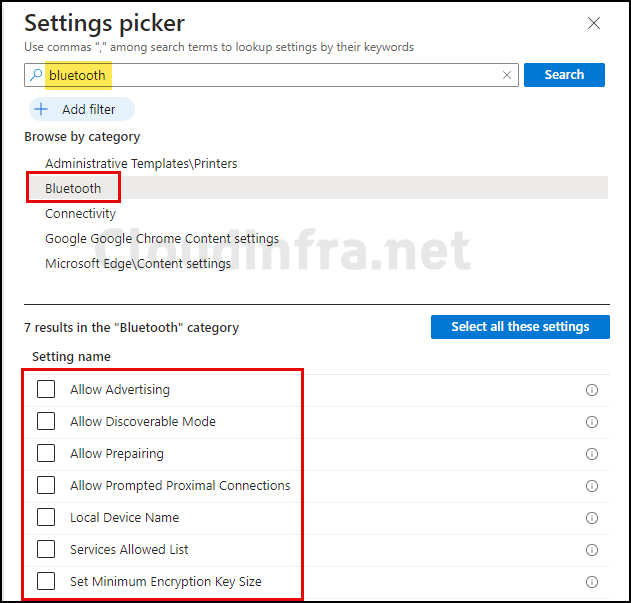
Please find more details about each setting in the table below:
| Bluetooth Setting Name | Description |
|---|---|
| Allow Advertising | Specifies whether the device can send out Bluetooth advertisements. If this is not set or it is deleted, the default value of 1 (Allow) is used. The most restricted value is 0. |
| Allow Discoverable Mode | Specifies whether other Bluetooth-enabled devices can discover the device. If this is not set or it is deleted, the default value of 1 (Allow) is used. Most restricted value is 0. |
| Allow Prepairing | This policy allows IT administrators to block users on these managed devices from using Swift Pair and other proximity-based scenarios. |
| Allow Prompted Proximal Connections | When pairing Bluetooth devices, multiple levels of encryption strength are used. This policy helps prevent weaker devices from being used cryptographically in high-security environments. |
| Local Device Name | This policy allows IT administrators to block users on these managed devices from using Swift Pair and other proximity-based scenarios. |
| Services Allowed List | Set a list of allowable services and profiles. String hex formatted array of Bluetooth service UUIDs in canonical format, delimited by semicolons. For example, {782AFCFC-7CAA-436C-8BF0-78CD0FFBD4AF}. The default value is an empty string. For more information, see ServicesAllowedList usage guide. |
| Set Minimum Encryption Key Size | Specifies whether other Bluetooth-enabled devices can discover the device. If this is not set or it is deleted, the default value of 1 (Allow) is used. The most restricted value is 0. |
FAQs
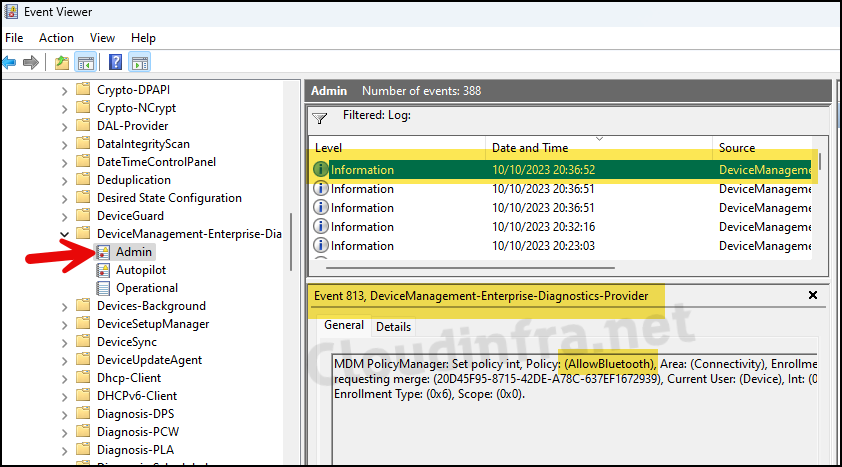
Where can I find logs related to Device Configuration Profile?
– Press the Windows key + R to open the Run dialog box
– Type eventvwr and press Enter to open Event Viewer.
– Go to Application and Services logs > Microsoft > Windows > Devicemanagement-Enterprise-Diagnostics-Provider > Admin folder.
– Search for Event ID 813 or 814 and go through the logs to find the one related to this deployment. [Please refer to the below screenshot showing Event ID 813 Information]