In this blog post, we will explore the settings to disable/block Microsoft store app using Intune on Windows. To disable the store app, we can use a setting available in the Settings catalog called Turn off the Store application. Enabling this setting will prevent users access to the Store app.
Please note that Turn off the Store application setting is only applicable to Enterprise licensing.
When you enable Turn off the Store application to disable Microsoft Store app. Access to the store apps via company portal app and also the deployment of store apps using Microsoft Store apps (new) will still work.
- Turn off the Store application:
- Prevents users from directly accessing the store using the
wingetAPIs.
- Prevents users from directly accessing the store using the
- Require Private Store Only
- This setting is also available in the Settings catalog. It also only works for Enterprise licensing customers only. However, it will not block Winget APIs to install apps via Winget. For more information, refer to the link: Block MS Store except Winget.
After blocking Microsoft store app, It’s recommended to also remove/unpin the Store app icon from the taskbar of your Windows device. This will avoid users clicking on it and getting any error message that the store is blocked. To remove/unpin Store app from taskbar, refer to the blog post: Remove/Unpin Microsoft Store from Taskbar using Intune. It will also not allow users to pin the Store app to the taskbar.
Remove/unpin the Store app from taskbar
Contents
Disable/Block Microsoft Store App Using Intune
- Sign in to the Intune admin center > Devices > Configuration > Create > New Policy.
- Select Platform as Windows 10 and later.
- Profile type: Settings Catalog.
- Basics: Provide a Name and Description of the policy.
- Configuration settings: Click on + Add settings and search for Turn off store application. Select the setting for configuration.
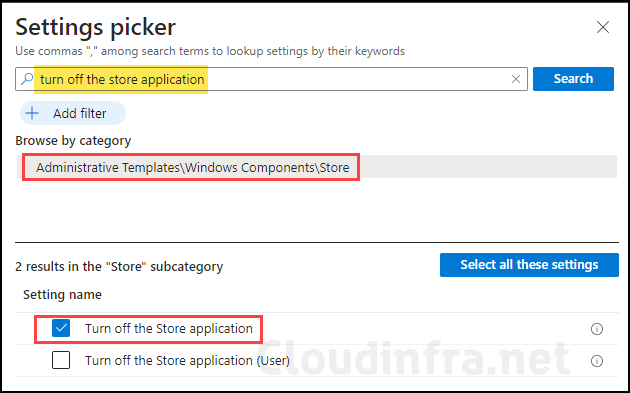
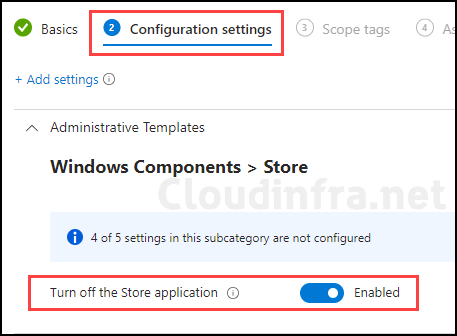
- Enable Turn off the Store application setting.
Denies or allows access to the Store application. If you enable this setting, access to the Store application is denied. Access to the Store is required for installing app updates. If you disable or don’t configure this setting, access to the Store application is allowed.
About Turn off the Store application
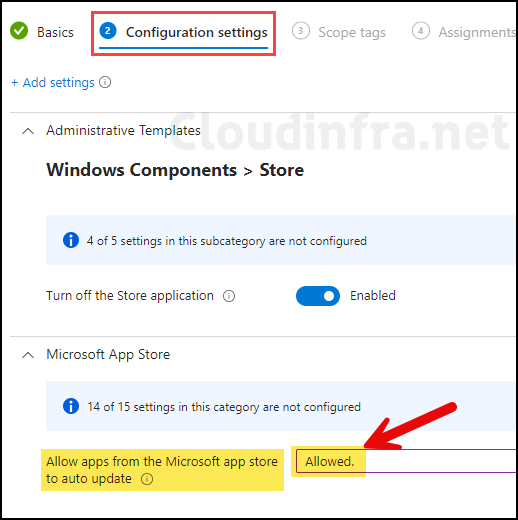
- I would recommend configuring an additional setting to allow auto-update apps from the Microsoft app store. Click on + Add settings again and search Microsoft app store. Select Allow apps from the Microsoft app store to auto update.
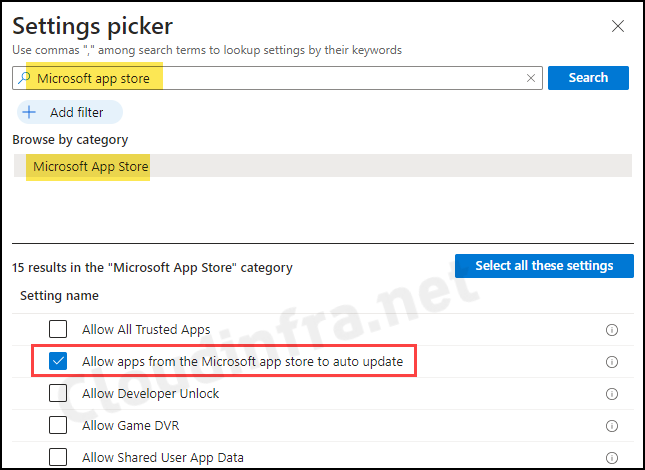
- Set Allow apps from the Microsoft app store to auto update to Allowed.
Specifies whether automatic update of apps from Microsoft Store are allowed. Most restricted value is 0.
Allow apps from the Microsoft app store to auto update
- Scope tags (optional): A scope tag in Intune is an RBAC label you add to resources (policies, apps, devices) to limit which admins can see and manage them. For more Information, read: How to use Scope tags in Intune.
- Assignments: Assign the policy to Entra security groups that contain the target users or devices. As a best practice, pilot with a small set first; once validated, roll it out more broadly. For guidance on assignment strategy, see Intune assignments: User groups vs. Device groups.
- Review + create: Review the deployment summary and click Create.
Sync Intune Policies
The device check-in process might not begin immediately. If you’re testing this policy on a test device, you can manually kickstart the Intune sync from the device itself or remotely through the Intune admin center.
Alternatively, you can use PowerShell to force the Intune sync on Windows devices. Restarting the device is another way to trigger the Intune device check-in process.
End User Experience
Once this policy has been successfully applied to the end-user’s devices, any user attempting to launch the Microsoft Store application will encounter an error message stating that the Microsoft Store is blocked. The error code 0x800704EC will also be displayed at the bottom of the window.
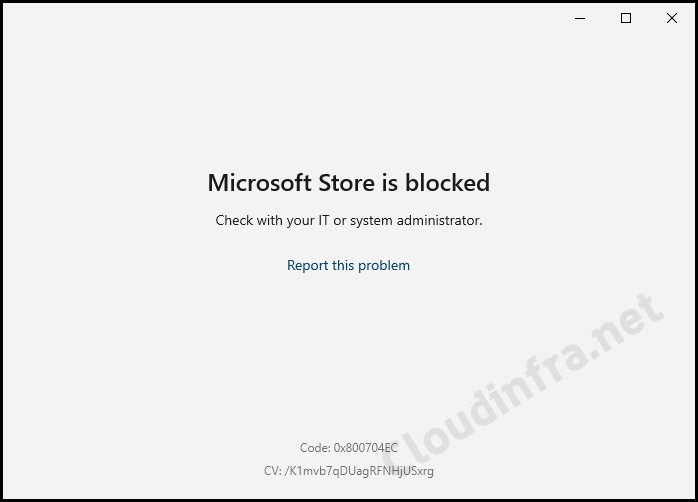
Failed to Install or Upgrade Microsoft Store package
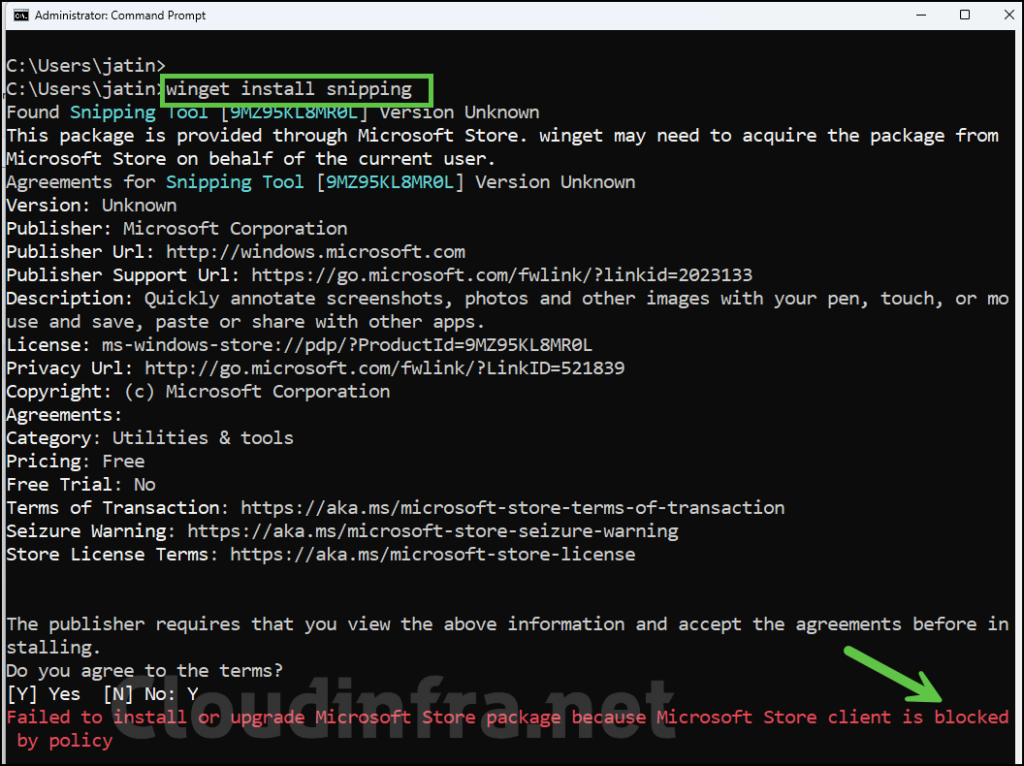
After applying the Turn off the Store application policy to the target devices, Winget will also be blocked. If you attempt to install any application using winget, you will receive the following error message:
Failed to install or upgrade Microsoft Store package because Microsoft Store client is blocked by policy
Disable/Block Microsoft Store App for Windows 10/11 Pro Edition
Turn off the Store application and RequirePrivateStoreOnly policy settings configured via Intune are not applicable to Windows 10 and Windows 11 professional editions.
To block Microsoft Store App on Windows 10 and Windows 11 professional edition, you can create a DWORD registry entry RequirePrivateStoreOnly under HKLM:\SOFTWARE\Policies\Microsoft\WindowsStore and set its value to 1.
You could also use a DWORD registry entry RemoveWindowsStore under HKEY_LOCAL_MACHINE\SOFTWARE\Policies\Microsoft\WindowsStore. Set its value to 1 to block Microsoft store and reboot the device.
Please note that I tested blocking MS Store App using RemoveWindowsStore on a Windows 11 Enterprise device and rebooted my device a couple of times. However, Store App was still accessible. If you use this registry key and if it does not work, then you can use RequirePrivateStoreOnly registry entry.
If WindowsStore registry key does not exist, then create it first and then create DWORD reg entry RequirePrivateStoreOnly.
There are few ways to deploy the registry keys and values using Intune. You can deploy it via a simple one off PowerShell script, or you can use Intune device remediations. Please note that device remediations will again require enterprise licensing (#remediations-prerequisites).
PowerShell script deployment method will be more suitable for Pro Editions. I have prepared a script which you can use to create RequirePrivateStoreOnly registry entry to block the Store app on Windows 10/11 Pro editions. You can download the script from my GitHub repo link: Remediate-MSStore.ps1. Use the steps on the post: #step-2-deploy-powershell-script to deploy the script. That’s it!
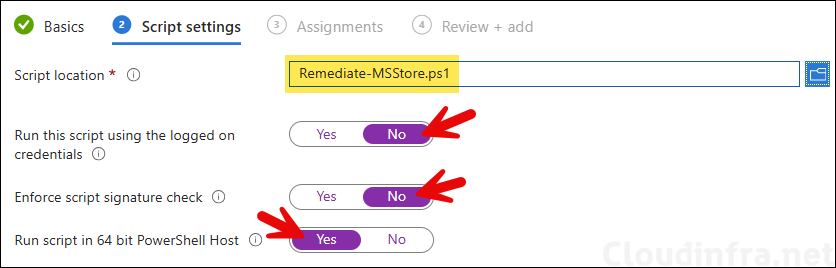
If you want to use Intune device remediations, I have prepared Detection and remediations scripts for this, you can download the script from the GitHub link: Disable Microsoft Store and use the steps on the post: #step-2-create-a-script-package to create a script package deployment and block MS Store App.
FAQs
What’s the OMA-URI setting to block the Microsoft Store?
Two OMA-URI settings can be used to block the Microsoft Store. One targets User Configuration, and the second one targets Computer configuration. Please find the settings below:
🔶 RemoveWindowsStore_1 [User-based configuration]
./User/Vendor/MSFT/Policy/Config/ADMX_WindowsStore/RemoveWindowsStore_1
🔶 RemoveWindowsStore_2 [Machine-based configuration]
./Device/Vendor/MSFT/Policy/Config/ADMX_WindowsStore/RemoveWindowsStore_2
How to Disable Microsoft Store App using Registry?
Go to HKEY_LOCAL_MACHINE\SOFTWARE\Policies\Microsoft\WindowsStore and create a DWORD registry entry called RemoveWindowsStore and set its value to 1 to disable it.
To enable it again, set the DWORD registry entry RemoveWindowsStore value to 0. Please note if RemoveWindowsStore reg entry does not work, Use RequirePrivateStoreOnly as mentioned above.
Find logs related to this deployment
To find the logs related to your Intune deployment, Open Event Viewer > Application and Services logs > Microsoft > Windows > Devicemanagement-Enterprise-Diagnostics-Provider > Admin folder.
Search for Event ID 813 or 814 and go through the logs to find the one related to this deployment.
How to block Microsoft Store App using Group Policy?
1. Press Windows + R to open the Run dialog box.
2. Type gpmc.msc and press Enter to open the Group policy management console.
3. Go to Computer Configuration > Administrative templates > Windows Components > Store.
4. Select Turn off the Store application and edit this setting.
5. Select Enabled to enable this setting and press OK.
When you Enable Turn off the store application, it also disables app updates from Microsoft Store. Ensure you disable the policy setting Turn off automatic download and install as well. This allows store apps to update, keeping access to Microsoft Store blocked.
Conclusion
Consider blocking access to the Microsoft Store in your company because it offers a wide range of non-productive apps. Additionally, using the Microsoft Store can complicate app management for your IT administrators.
Instead, it’s advisable to centralize app management through Intune, which provides greater control. Furthermore, Microsoft has introduced a new app type in Intune for improved app management: Microsoft Store app (new).

Thanks to creating this article.
One question: When Windows default apps like calculator, camera, Photos app not deployed via Intune; will they still be able to pull their updates from MS Store?
Hi,
I’m asking myself exactly the same question. Do you have the answer?
Thanks
lso have the same query… will this kill updates to calculator camera notepat etc…
Hi,
I’ve applyed this procedure, which seems to work because I can see :
– the register entry is OK (RemoveWindowsStore = 1)
– and the event viewer is showing me the good event :
PolicyManager MDM : définir chaîne de stratégie. Stratégie : (RemoveWindowsStore_1). Zone : (ADMX_WindowsStore). EnrollmentID demandant la fusion : (72E0ECC1-EFE8-4087-9178-D51D4DBAD273). Utilisateur actuel : (S-1-5-21-1046232930-3145662814-1742998727-88664). Chaîne : (). Type d’inscription : (0x6). Étendue : (0x1).
But I can still access the store and the winget installation is still working.
What can I do to troubleshoot this issue ?
Thanks in advance
Best regards
Hello Jatin,
Thanks for this article. I’ve followed your steps and created configuration policy via Intune.
I too have the same problem reported above. Registry value showing “RemoveWindowsStore=1”.
But still Microsoft Store is opening as normal and able to install apps. Would you like to share further troubleshooting steps?
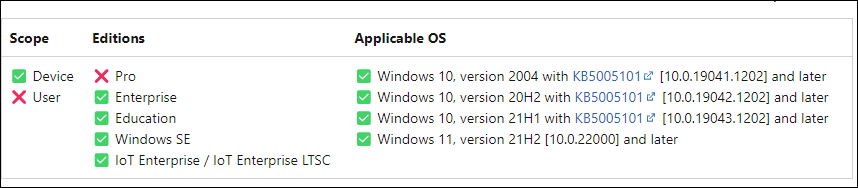
To which OS version is this applicable (Windows Business, Pro, Enterprise)?
Hi Pawel, It’s applicable to the below OS versions (Not for Pro)
✅ Enterprise
✅ Education
✅ Windows SE
✅ IoT Enterprise / IoT Enterprise LTSC
Please refer to below link for more Information:
https://learn.microsoft.com/en-gb/windows/client-management/mdm/policy-csp-admx-windowsstore?WT.mc_id=Portal-fx#removewindowsstore_1
I configured the policy. However If i go to apps.microsoft.com, i still can download and install store apps via this way
I have performed above steps and able to block the app store however now company portal is not installing too. Can you please suggest if this is expected behavior as CP is mandatory on the devices.