In this blog post, I’ll show you how to Install Microsoft Single Sign On (SSO) Extension in Chrome on macOS via Intune. On macOS, Chrome doesn’t automatically use the device’s Microsoft sign-in state the way Safari and Microsoft Edge do. Microsoft SSO extension bridges that gap by connecting Chrome to the Enterprise/Platform SSO stack. This lets users who sign in with Microsoft Entra ID on the Mac get seamless access to Microsoft 365 and other Entra-integrated apps in Chrome without repeated prompts.
It also helps meet Conditional Access requirements by providing device compliance signals and PRT based SSO. Using Touch ID reduces how often users need to type their password to sign in and access corporate apps. Because Entra ID is the identity provider, users authenticate to the Mac and their apps with their Entra ID credentials, which simplifies administration and reduces account-related issues.
We’ll deploy the extension with a simple Intune Preference file (.plist) policy so it’s installed and enforced on every targeted Mac, keeping your browser experience consistent across the devices. Let’s get to the steps and deploy the extension to chrome on Intune-managed macOS devices.
If you haven’t deployed Chrome on macOS devices yet, this guide can help: Deploy Google Chrome on macOS using Intune.
Deploy Google Chrome on macOS
Contents
Deployment Prerequisites
- Extension ID: ppnbnpeolgkicgegkbkbjmhlideopiji (Microsoft Single Sign On).
- Update URL: https://clients2.google.com/service/update2/crx (Chrome Web Store).
Step 1: Prepare Preference file (.plist)
Intune’s Preference file profile expects only the key/value XML (no <plist> or <dict> wrappers). I have prepared below XML file which will force deploy Microsoft SSO extension in chrome. Copy below XML code and save it in a file called Chrome-Microsoft-SSO-Extension.xml.
Chrome accepts two policies for force-installing extensions: ExtensionInstallForcelist (array of
id;update_urlstrings) or ExtensionSettings (per-ID config). Either works via macOS managed preferences; ExtensionSettings overrides ExtensionInstallForcelist if you apply both.
Chrome-Microsoft-SSO-Extension.xml
<key>ExtensionSettings</key>
<dict>
<key>ppnbnpeolgkicgegkbkbjmhlideopiji</key>
<dict>
<key>installation_mode</key>
<string>force_installed</string>
<key>update_url</key>
<string>https://clients2.google.com/service/update2/crx</string>
</dict>
</dict>Step 2: Create Intune Policy
Now, let’s create an Intune policy to deploy the XML file and install Microsoft SSO extension in chrome.
- Sign in to the Intune admin center > Devices > macOS > Configuration > Create > New Policy.
- Click on the Profile type drop-down and select Templates.
- Select Template name as Preference file and click Create.
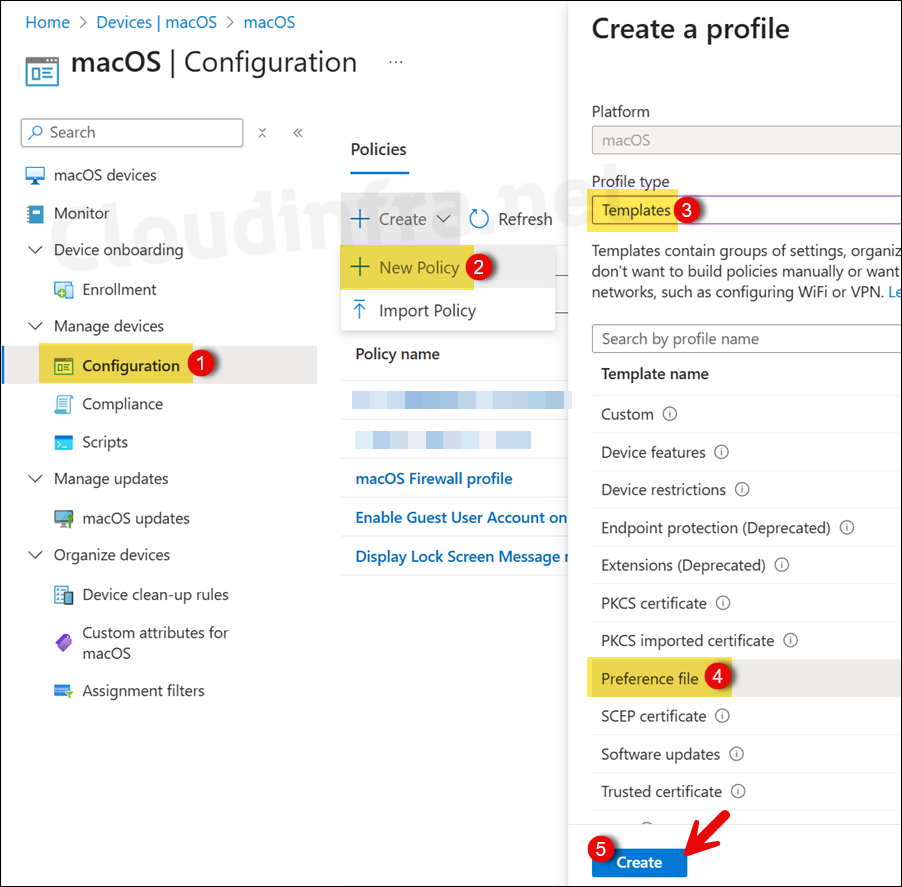
- Basics tab: Provide a Name and Description of the policy. For example: Microsoft SSO Extension install in Chrome.
- Configuration settings: Under the configuration settings tab, configure below settings:
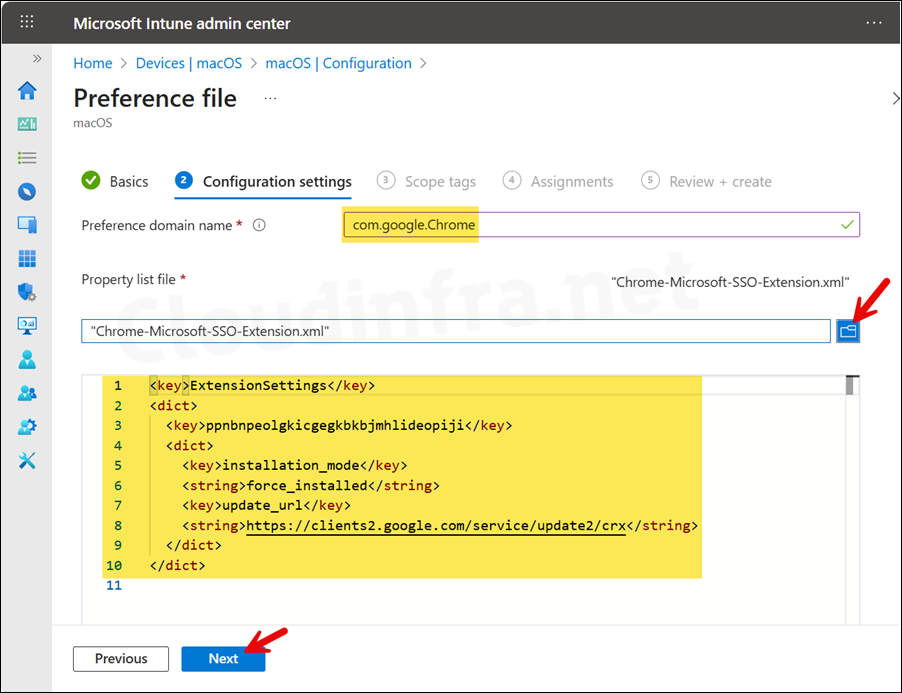
- Preference domain name: com.google.Chrome
- Property list file: Select the XML file we created (Chrome-Microsoft-SSO-Extension.xml), and click Next.
- Scope tags (optional): This is an optional configuration, skip it by clicking on Next. A scope tag in Intune is an RBAC label you add to resources (policies, apps, devices) to limit which admins can see and manage them.
- Assignments: Create or use an entra security group containing macOS devices. Click on Add groups and select the group to assign this policy.
- Review + create: Review the deployment summary and Click on Create.
Sync Intune Policies
The device check-in process might not begin immediately. If you’re testing this policy on a test device, you can manually kickstart Intune sync from the device itself or remotely through the Intune admin center.
Alternatively, you can use PowerShell to force the Intune sync on Windows devices. Restarting the device is another way to trigger the Intune device check-in process.
Monitor Microsoft SSO Extension Installation Progress
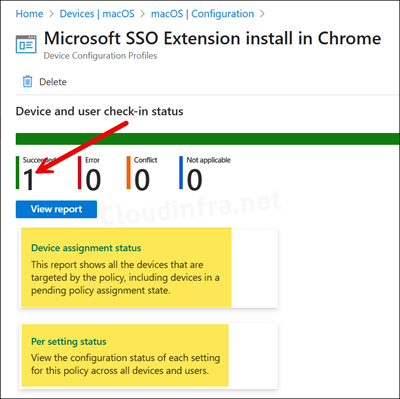
- Go to Devices > macOS > Configuration. Select the profile you want to monitor.
- Check under Device and user check-in status to confirm the success of the profile deployment.
- For additional details, click Device Assignment Status and Per Setting Status.
End User Experience
After the Intune device check-in process is completed, Microsoft SSO extension will be installed in the Chrome browser. To check and confirm, follow below steps:
- Sign in to one of the target macOS device and launch Google Chrome application.
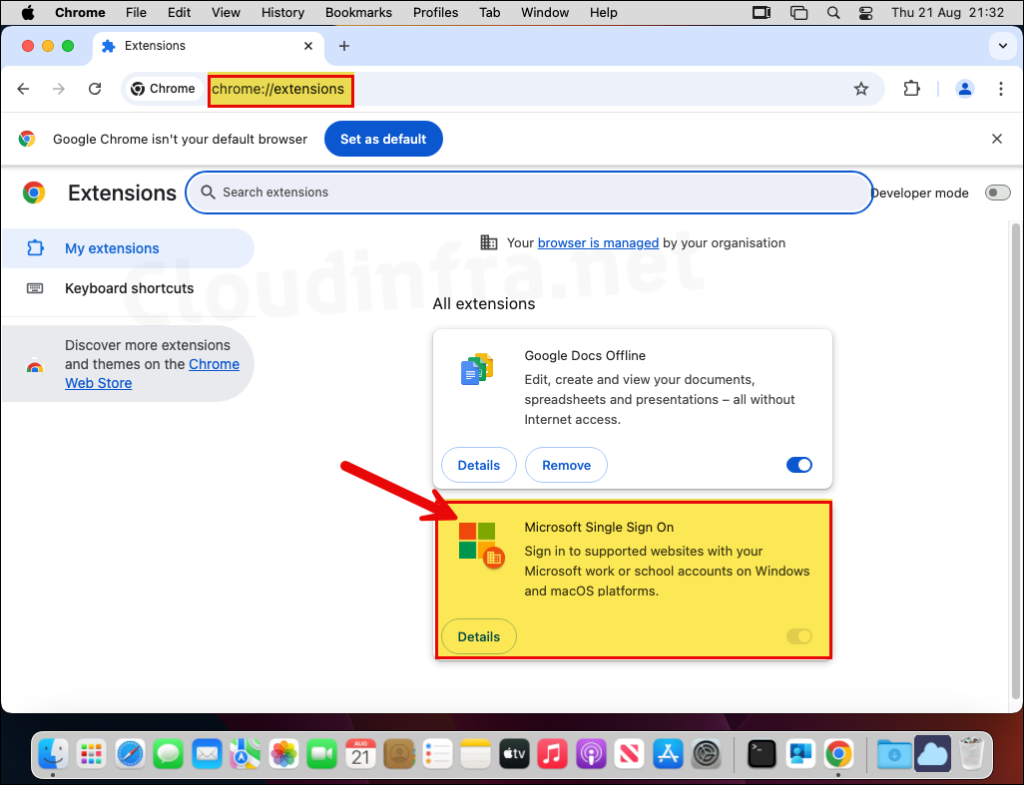
- In the Address bar, type chrome://extensions and press Enter.
- Check and confirm if Microsoft Single Sign On extension has been installed. (Notice that the option to disable this extension (toggle switch) is greyed out, as it’s managed by Intune).
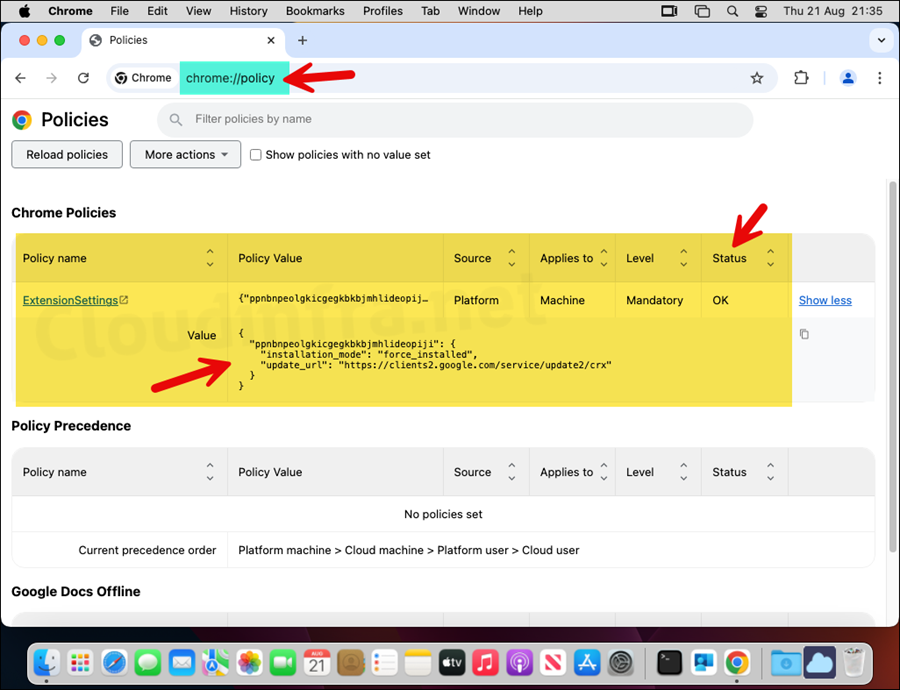
You can also verify the extension policy by typing chrome://policy in the Google Chrome address bar and check if the ExtensionSettings policy is listed and its Status is showing as OK.
Troubleshooting
The process to install an extension in Google Chrome browser is smooth, and I have not experienced any issues with this Intune policy deployment. However, there could be a case when the extension is not getting installed and taking longer than expected. This could be due to a number of issues.
Refer to IntuneMDMDaemon*.log and IntuneMDMAgent*.log files, which could provide useful information for troubleshooting and finding out the root cause of the issue. For more information about how to locate these files on a macOS device, see my other blog post, How To Collect Intune Logs From macOS Device.
- If you provide the wrong Preference domain name or if it’s a typing mistake, the policy will not apply and therefore the required extension will not be installed.
- Do not provide <plist> or <dict> wrappers for the XML file, as this may lead to an error.
- You may get an error Profile not applying or Intune error -2016341103, this could be due to .plist file structure. Review the .plist file again and check if the structure and schema of the file is ok.
- If the Extension does not install still, verify if the Extension ID and update URL values are correct.
