In this blog post, I will demonstrate the steps to set idle session limits for Windows 365/AVD Cloud PCs (Enterprise and Frontline Editions). Please note, the exact same policy will work on Azure virtual desktop (AVD) as well.
Windows 365 Frontline is a cost-saving option, offering a single license to provision three Cloud PCs. However, only one session can be connected at a time.
It might be more logical to apply idle session limits to Windows 365 Frontline Edition Cloud PCs because you want the session to be released for the next person to utilize. Since users may be working in different shifts, it’s ideal to end the session when it’s not actively used.
When users are using Windows 365 Enterprise Edition, they typically have personal/dedicated Cloud PCs. Therefore, it’s generally not advisable or required to set an idle session time limit for users assigned with a Windows 365 Enterprise license.
By default, no idle session limit is applied. The session will remain active until the user logs off from their Cloud PC. Therefore, a user working in the next shift with a Windows 365 Frontline license may get issues connecting to their Cloud PC.
As a best practice, users should save their work and sign out from their Cloud PCs once they no longer use them. However, there are cases when a user forgets to sign out and the session remains active. Therefore, configuring an idle session limit will work best in this scenario. It will automatically log out the user after a set period of inactivity.
Contents
Configure Idle Session Limit using Intune
- Sign in to the Intune admin center > Devices > Configuration > Create > New Policy.
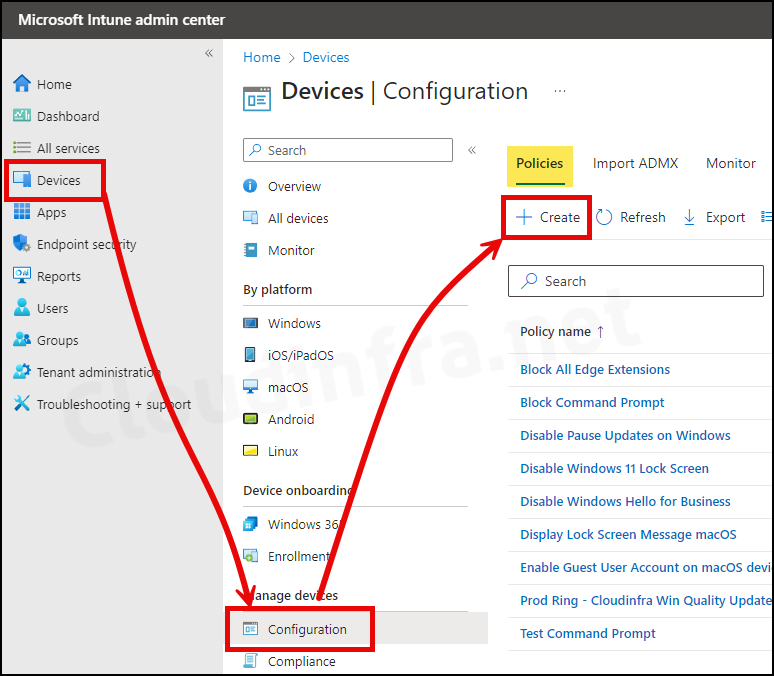
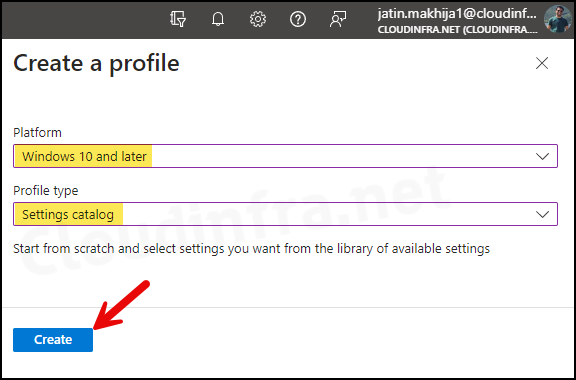
- Select Platform as Windows 10 and later
- Profile type as Settings Catalog
- Click on the Create button.
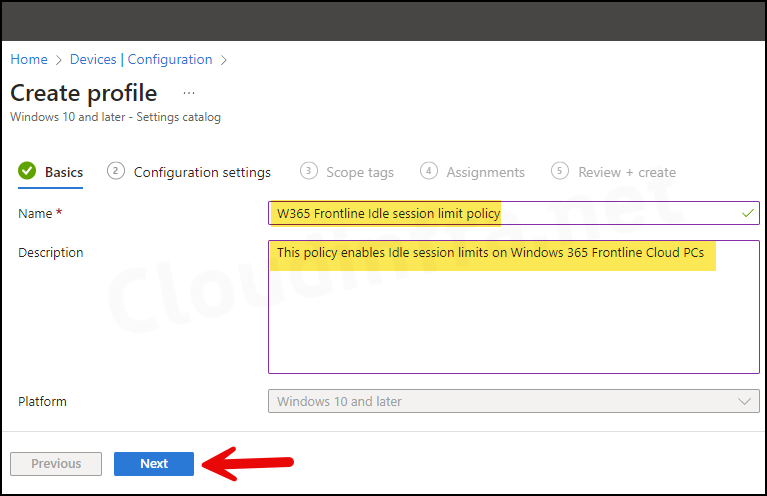
- Basics Tab: Enter the Name and Description of the profile.
- Configuration Settings:
- Click on + Add settings.
- In the Settings picker, search for idle session.
- Click on Administrative Templates\Windows Components\Remote Desktop Services\Remote Desktop Session Host\Session Time Limits category.
- Check the box for Idle session limits: (Device) and exit the settings picker.
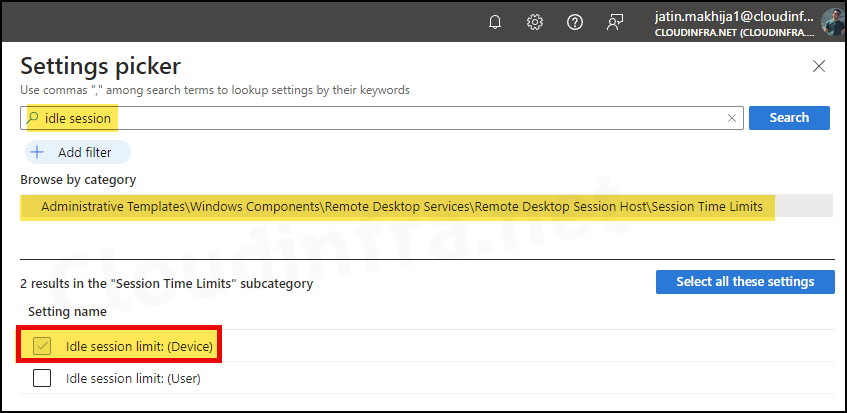
- Set time limit for active but idle Remote Desktop Services sessions: Use the toggle switch to Enable this setting.
- Idle session limit: (Device): You can select the timeout value for idle sessions, anywhere from 1 minute to 5 days. For demonstration and testing purposes, I have set it to 1 minute. However, you can choose the value that meets your organization’s session limit requirements. Click on Next to proceed.
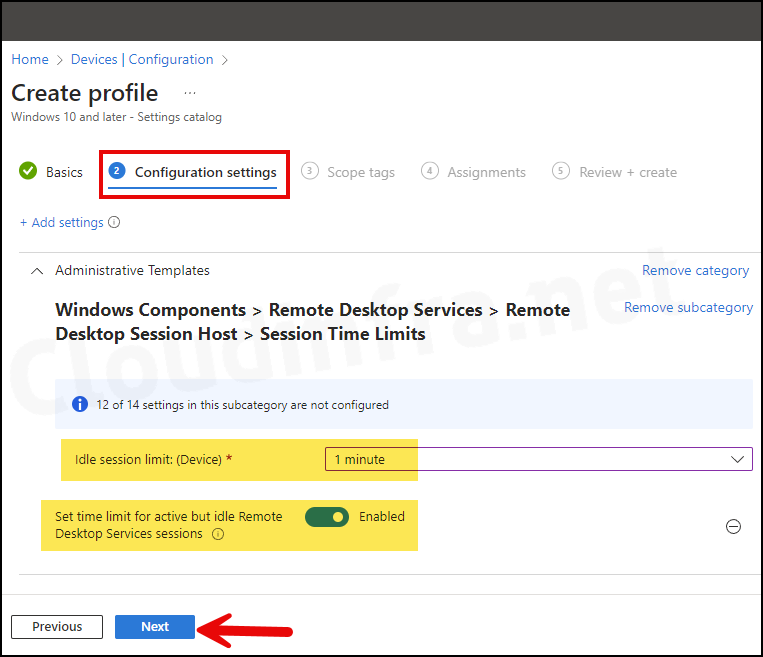
- Scope tags: Click on Next.
- Assignments tab: Click Add groups and select an Entra security group containing Cloud PCs.
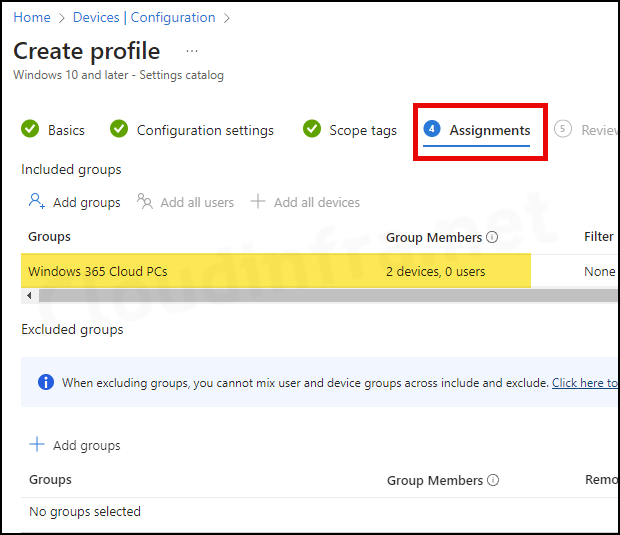
- Review + create: Review the policy summary and click Create.
Sync Intune Policies
The device check-in process might not begin immediately. If you’re testing this policy on a test device, you can manually kickstart Intune sync from the device itself or remotely through the Intune admin center.
Alternatively, you can use PowerShell to force the Intune sync on Windows devices. Restarting the device is another way to trigger the Intune device check-in process.
Monitoring Deployment Progress
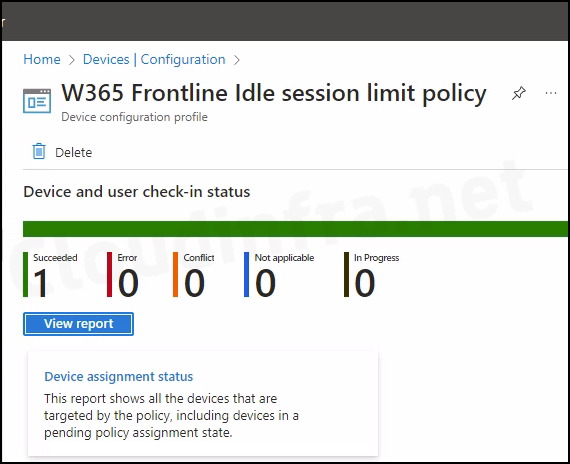
- Sign in to the Intune admin center > Devices > Configuration.
- Select the Device Configuration profile you want to work with, and at the top of the page, you’ll see a quick view of the Success, Failure, Conflict, Not Applicable, and In Progress status.
- Click on View report to access more detailed information.
End User Experience
After this policy is successfully applied, if a Cloud PC has been idle for the specified duration configured in the policy, the session will be automatically disconnected. Users will receive a pop-up notice stating, Your session timed out due to inactivity. Try connecting again.
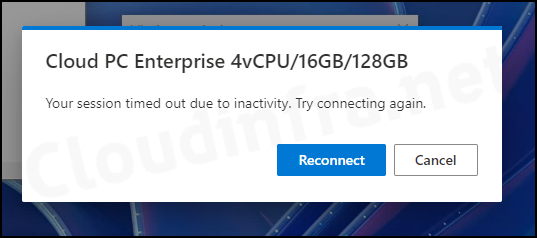
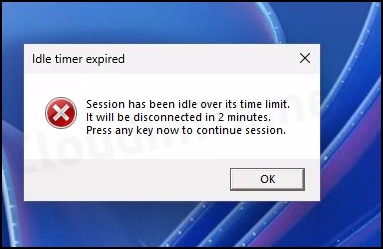
After clicking on the Reconnect button, session will be reconnected. After reconnecting to the Cloud PC, I got the following pop-up message: The session has been idle over its time limit and will be disconnected in 2 minutes. Press any key now to continue the session. Click on OK to continue using your Cloud PC.
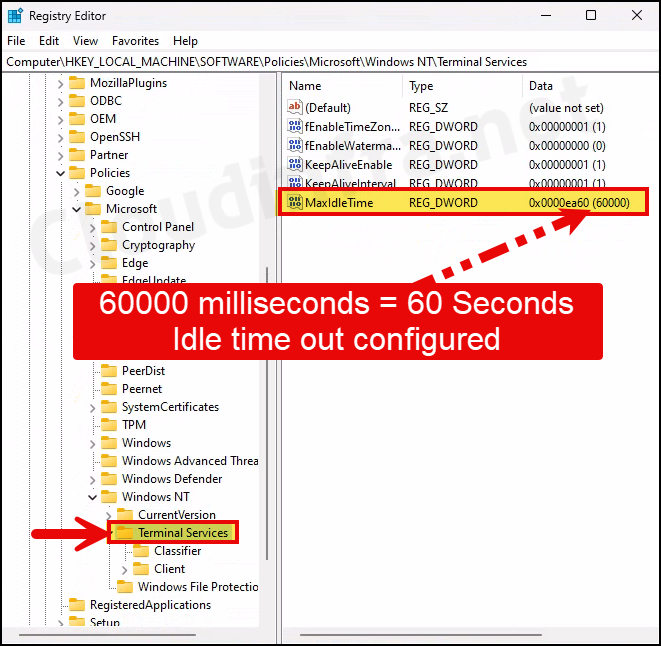
Registry Key for Idle Session Time limit
The registry location is HKEY_LOCAL_MACHINE\SOFTWARE\Policies\Microsoft\Windows NT\Terminal Services. You will find a registry entry called MaxIdleTime on the right side, a DWORD value. The value of this registry entry is in milliseconds.
For example, if you have configured an idle session timeout value of 1 minute in the policy, the registry entry MaxIdleTime would reflect the same. It would show 60000 milliseconds, equal to a 60 second timeout value. This confirms that Intune has configured this Cloud PC’s idle session timeout value correctly.
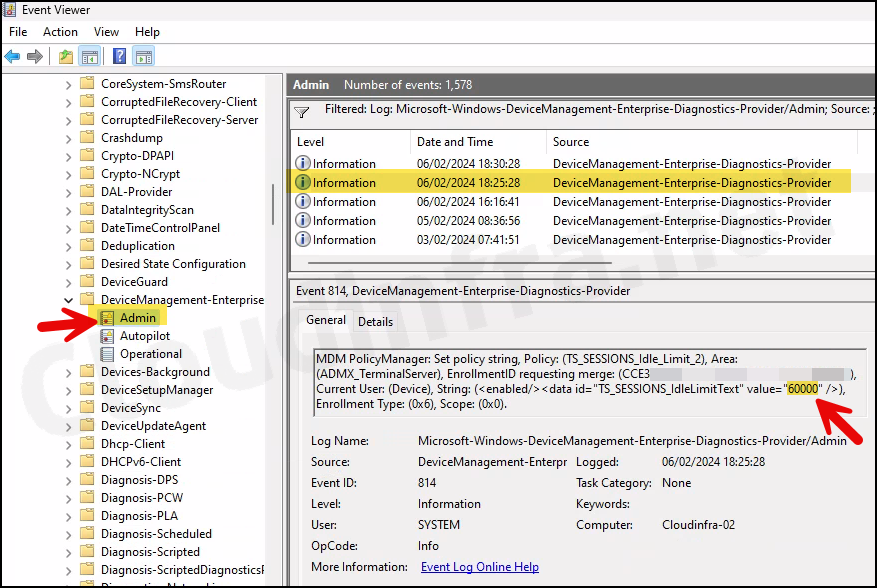
Confirm Idle Session Time Limit Value Using Event Viewer
We checked and confirmed idle session limit using Registry editor. This can also be confirmed using the Windows Event Viewer. Let’s check the steps:
- Press the Windows key + R to open the Run dialog box.
- Type
eventvwrPress Enter to open the Event viewer. - Navigate to Application and Services Logs > Microsoft > Windows > DeviceManagement-Enterprise-Diagnostics-Provider/Admin.
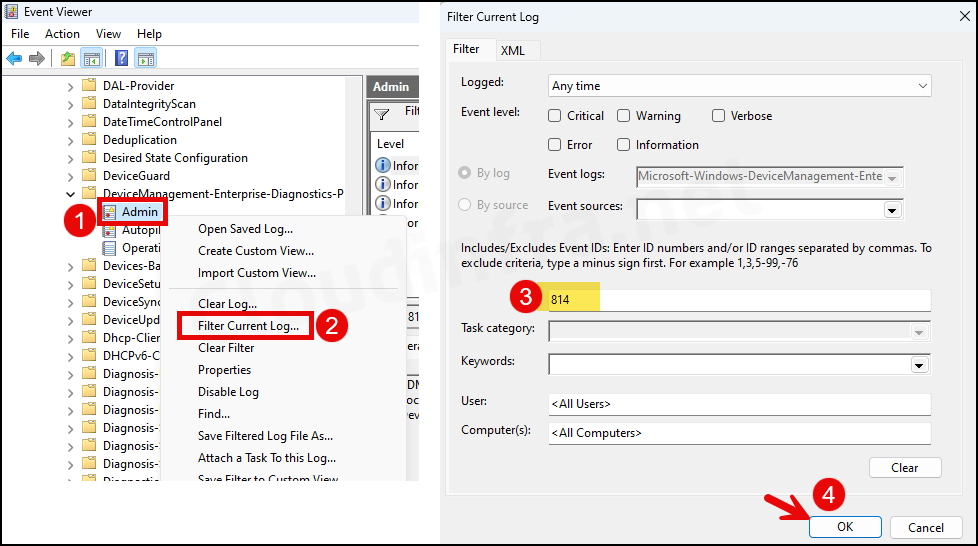
- Right-click on the Admin folder and click on Filter Current Log…
- Enter 814 in the Event ID box and click on OK.
- You can now locate all logs related to Event ID 814. Check them one by one until you identify the deployed configuration policy. Below screenshot shows the log that shows the TS_Sessions_IdlLimitText value as 60000, which is as we configured via Intune.
MDM PolicyManager: Set policy string, Policy: (TS_SESSIONS_Idle_Limit_2), Area: (ADMX_TerminalServer), EnrollmentID requesting merge: (CCE3B-8IYH-0BBB-0009-903BEHBE90B), Current User: (Device), String: (), Enrollment Type: (0x6), Scope: (0x0).
Event Log 814 corresponding to Idle session limit policy deployment