This blog post will show how to Block/Whitelist Chrome extensions using Intune. This will give you greater control over which extensions can be used on your organization’s devices, helping to keep your data secure and your employees productive.
Allowing users to install extensions in browsers can pose a security risk. Users may unknowingly Install a malicious extension, which could cause issues.
A best practice is to block all extension installations and allow only specific extensions approved by the administrator. We’ll use the Settings catalog to Block or Whitelist extensions in chrome. For whitelisting an extension, we will require its app extension ID. Let’s check the steps to first get the extension ID and then move to the settings catalog policy.
Contents
Step 1: Find the Extension ID that you want to Whitelist
Let’s check the steps to get the Extension’s ID from Chrome browser.
- Launch Google Chrome browser.
- Go to Google Webstore.
- Search for the extension that you want to whitelist, and then from the address bar of the browser, you can copy its Extension ID.
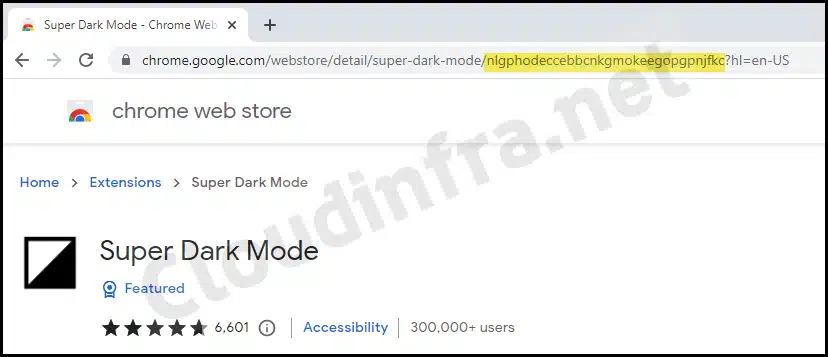
- Repeat this process for any other extensions you wish to whitelist or block, copying their respective Extension IDs into a notepad for later use in the Intune device configuration policy.
Step 2: Block All Extensions in Chrome and Whitelist Only Approved Ones
You can either Block All Extensions in Chrome and Whitelist only the ones you want to allow. Secondly, you also have the option to block specific Extensions while allowing the rest of the Extensions.
The first approach is more controlled as it allows only the approved extensions to be accessible to users while remaining ones remain blocked. Let’s configure it via Intune admin center.
- Sign in to the Intune admin center > Devices > Configuration > Create > New Policy.
- Select Platform as Windows 10 and later.
- Profile type as Settings catalog.
- Click on Create.
- Basics Tab: Provide a Name and Description of the Policy and click Next.
- Configuration Settings: Click on Add Settings and use the Settings picker to search using the keyword chrome. Click on the category Google Google Chrome Extensions and select Configure extension installation blocklist and Configure extension installation allow list.
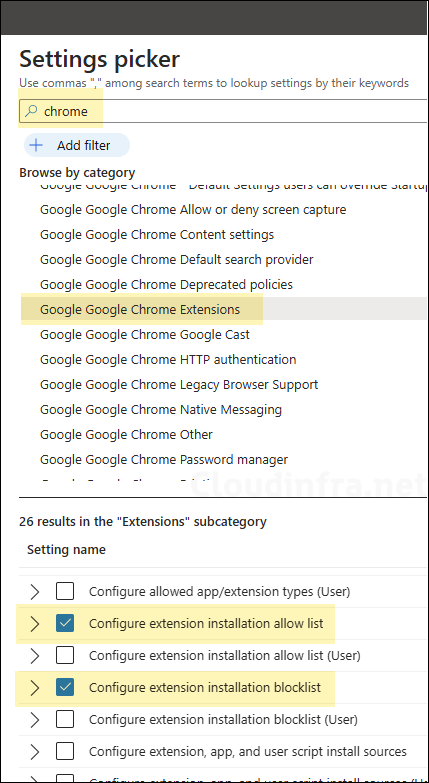
- Configure extension installation blocklist: Enable this setting and add * in the text box, and click OK to save. This will block all Extensions in chrome.
Instead of blocking all extensions using a wild card character *. You can also provide the extension IDs to block only specific extensions in Chrome.
In this scenario, we are Blocking All Chrome Extensions and using Configure extension installation allow list setting to whitelist specific Extensions.
Note
- Configure extension installation allow list: Enable this setting and provide the Extension IDs to Whitelist. As an example, we want to Whitelist the Super Dark Mode extension, therefore we have provided its extension ID. [Skip this step if you do not want to whitelist any Extensions in Google Chrome]
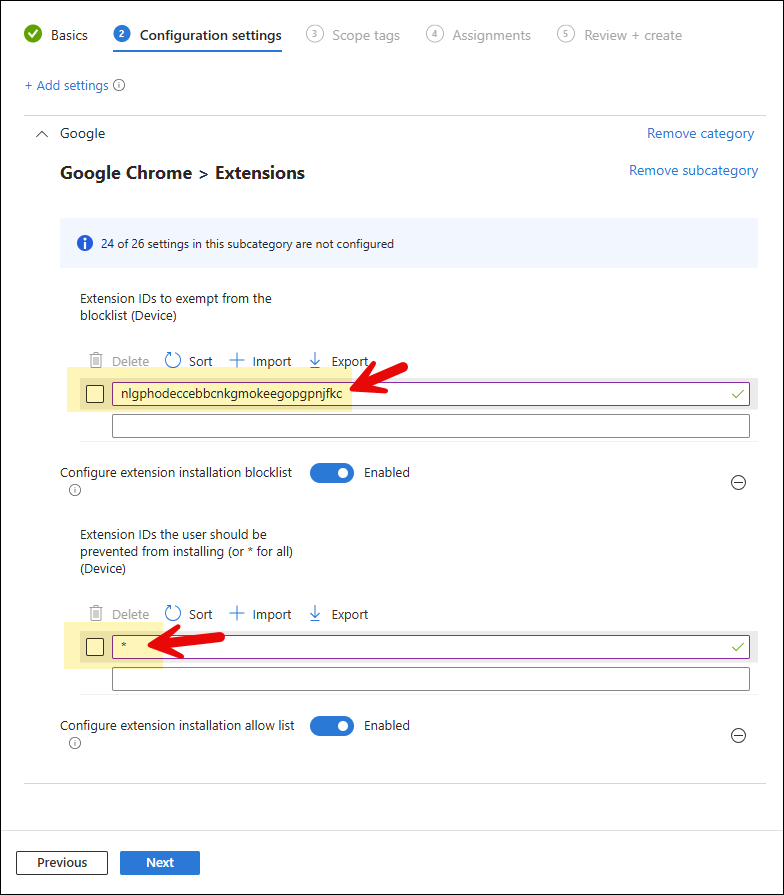
- Assignments: Click Add groups and select Entra security group containing Windows 10/11 devices or Entra ID users.
- Review + Create: Review the device configuration profile on the Review + Create tab and click Create.
Sync Intune Policies
The device check-in process might not begin immediately. If you’re testing this policy on a test device, you can manually kickstart the Intune sync from the device itself or remotely through the Intune admin center.
Alternatively, you can use PowerShell to force the Intune sync on Windows devices. Restarting the device is another way to trigger the Intune device check-in process.
End User Experience
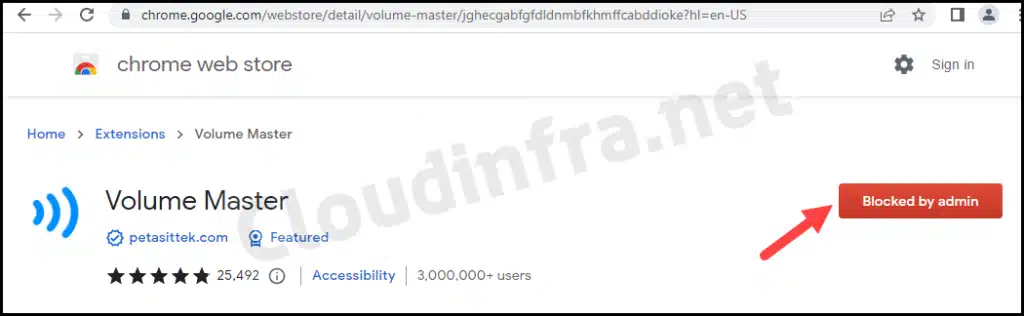
Let’s see how this policy affects the end user’s device. After successfully deploying this policy, open the Chrome browser to test whether the installation of all extensions is blocked and whether only the specific extension (in this case, Super Dark Mode) is allowed according to the whitelist.
If any existing extensions were installed when this policy was applied, they will also be blocked. Only the extensions that you whitelist from Intune will be allowed. An error may show up on Chrome: Blocked by admin. When you click this button, you will receive a pop-up message: Your admin has blocked <extension name> – App ID <app ID>.
Conclusion
In this blog post, we’ve explored a simple method for creating block lists and whitelists of extensions using Intune for the Chrome browser. You don’t need to utilize OMA-URI settings; instead, you can use Settings catalog to create block lists and whitelists for Chrome extensions and apply the policy to end-user devices.

Chrome becomes total crap browser. Google has on New Chrome Web Store began to block all extensions install on chrome based browser (update to the last browser doesn’t help). Naked Chrome browser is USELESS (try to browse without any extensions installed).
Hi,
First thanks for all your posts ! Very usefull !
About browser extensions it can be interesting to first get from devices the list of current extensions that are installed… Do you know how to pull these informations from devices managed by intune ?
All the best
T.