In this blog post, I will show you the steps to disable TLS 1.0 and TLS 1.1 for IE/EdgeHTML using Intune. TLS protocol provides privacy and data integrity between two communicating applications. SSL and TLS are both cryptographic protocols, but because SSL protocols do not provide a sufficient level of security compared to TLS, SSL 2.0 and SSL 3.0 have been deprecated. TLS 1.0 was released in 1999, TLS 1.1 was released in 2006, TLS 1.2 was released in 2008, and TLS 1.3 was released in 2018.
If you are interested in learning more about these protocols, their differences, and security improvements, you can check Protocols RFCs (Request for Comments) at these links: TLS1.0 RFC, TLS 1.1 RFC, TLS 1.2 RFC, and TLS 1.3 RFC.
This blog post is for legacy version of Internet Explorer and Microsoft Edge which was based on MSEdgeHTML. It’s recommended to use the latest Microsoft Edge browser which is based on Chromium like Google Chrome.
If you are using Microsoft Edge browser version 84 or later, TLS 1.0 and TLS 1.1 protocols are already disabled by default.
Contents
Create a Device Configuration Profile
To disable TLS 1.0 and TLS 1.1 using the Intune admin center for legacy web browsers such as Internet Explorer and Microsoft Edge (EdgeHTML), please follow these steps:
- Sign in to the Intune Admin Center > Devices > Configuration > Create > New Policy.
- Select Platform as Windows 10 and later.
- Select Profile Type as Settings catalog.
- Basics: Provide a Name and description of the Device configuration profile.
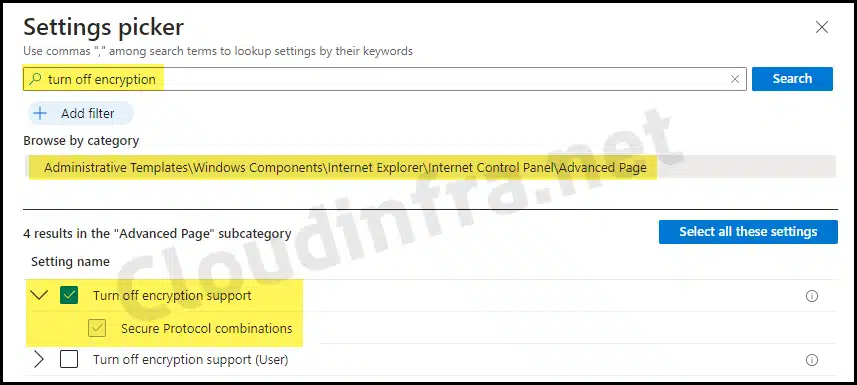
- Configuration Settings: Click on the + Add settings link and search for turn off encryption support.
- You can find the Turn off encryption support setting under the Category: Administrative Templates\Windows Components\Internet Explorer\Internet Control Panel\Advanced Page.
- Select Turn off encryption support.
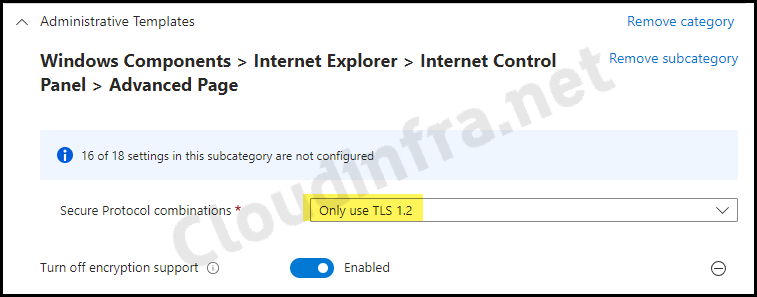
- Toggle the switch to Enabled to Turn off encryption support. From the drop-down menu of Secure Protocol combinations, Select Only use TLS 1.2. Click on Next to proceed.
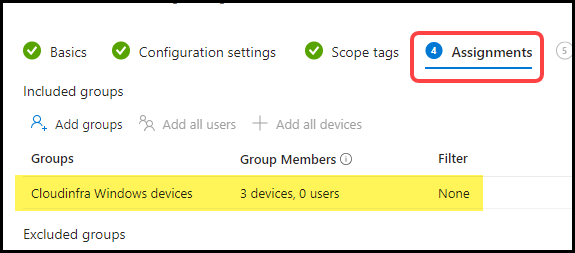
- Assignments: Click on Add group to add an Entra security group containing windows devices.
- Review + create: Review the deployment and click on Create.
Sync Intune Policies
The device check-in process might not begin immediately. If you’re testing this policy on a test device, you can manually kickstart Intune sync from the device itself or remotely through the Intune admin center.
Alternatively, you can use PowerShell to force the Intune sync on Windows devices. Restarting the device is another way to trigger the Intune device check-in process.
End User Experience
To verify that TLS 1.0 and TLS 1.1 protocols have been successfully disabled for legacy browsers on the end user’s machine as per the device configuration profile, please follow these steps:
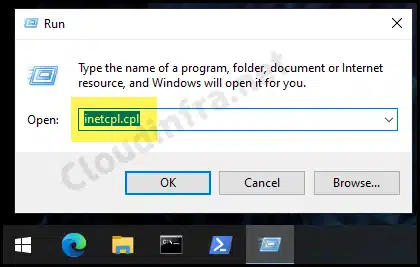
- Press the Win + R keys to open the Run dialog box
- Type inetcpl.cpl and press Enter.
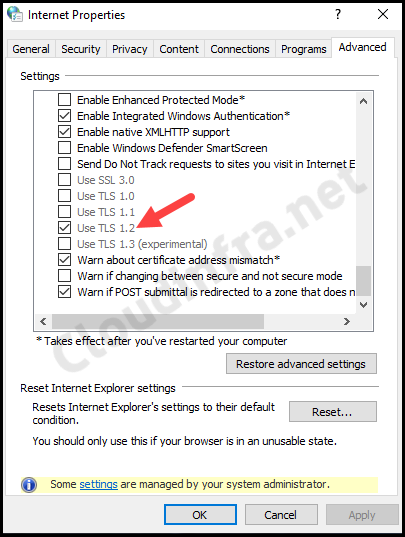
- Click on Internet Options and go to the Advanced tab.
- Scroll down in the settings to locate the TLS options.
- The screenshot below shows that Use TLS 1.2 is the only enabled option.
Re-enable TLS 1.0 and TLS 1.1
There are two options to rollback the Device Configuration profile for disabling TLS 1.0 and TLS 1.1.
- If you encounter problems after disabling TLS 1.0 and TLS 1.1, you can quickly reverse the change by unassigning the Disable TLS 1.0 and TLS 1.1 Device Configuration profile from the device.
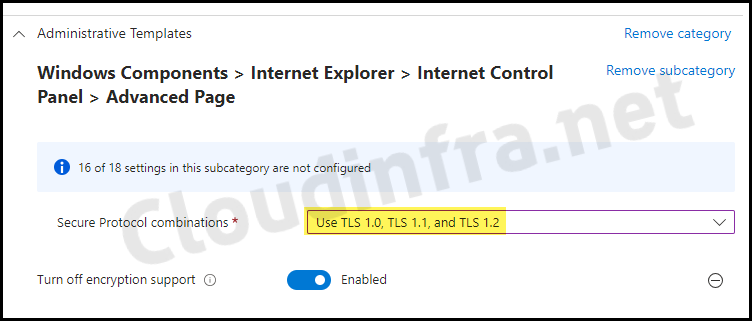
- Another option is to modify the Device Configuration profile created earlier and change the setting for Turn off encryption support > Secure Protocol combinations to Use TLS 1.0, TLS 1.1, and TLS 1.2.
Conclusion
In this blog post, we’ve learned how to disable TLS 1.0 and TLS 1.1 for legacy web browsers such as Internet Explorer and Microsoft Edge based on MSEdgeHTML. It’s essential to disable TLS 1.0 and TLS 1.1, as these are considered weak protocols that should be deactivated at the browser and operating systems levels.
