In this blog post, I will show you the steps to disable TLS 1.0 and TLS 1.1 on Nginx server. Let’s take a look:
Contents
Steps to Disable TLS 1.0 and TLS 1.1 on Nginx
The TLS protocol provides privacy and data integrity between two communicating applications. SSL and TLS are both cryptographic protocols, but because SSL protocols do not provide a sufficient level of security compared to TLS, SSL 2.0 and SSL 3.0 have been deprecated. TLS 1.0 was released in 1999, TLS 1.1 was released in 2006, TLS 1.2 was released in 2008, and TLS 1.3 was released in 2018.
You can check Protocols RFCs (Request for Comments) at these links: TLS1.0 RFC, TLS 1.1 RFC, TLS 1.2 RFC, and TLS 1.3 RFC. Use the below methods to disable TLS 1.0 and TLS 1.1 on Nginx Server.
By default, when you install Nginx on the Ubuntu server, the default configuration provides TLS 1.0 and TLS 1.1 support, and these protocols are enabled.
However, as the TLS 1.0 and TLS 1.1 protocols are deprecated, we should disable them using the Nginx configuration file. It’s recommended that a backup of nginx.conf be taken before making any changes.
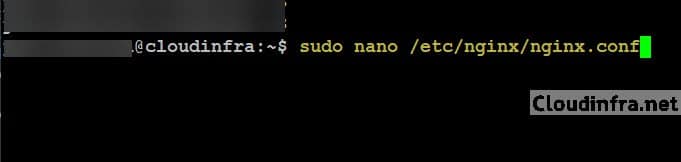
Connect to your server and run the below command to open the nginx.conf file. It may prompt you for the administrator password.
Open nginx.conf file
sudo nano /etc/nginx/nginx.conf
After you open the Nginx configuration file, search the https block to find the SSL protocol configuration, including TLSv1 and TLS1.1. It could be something like this line:
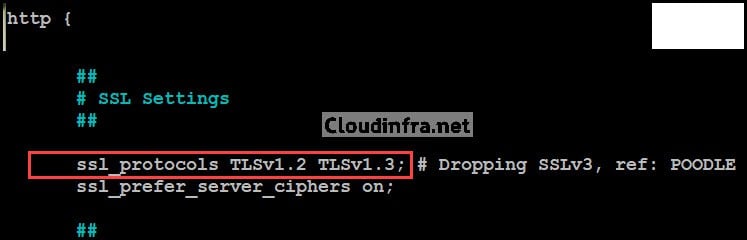
ssl_protocols TLSv1 TLSv1.1 TLSv1.2 TLS 1.3; # Dropping SSLv3, ref: POODLE
Remove TLSv1 and TLSv1.1 from the line, as shown in the screenshot. This will only allow TLS1.2 and TLS1.3 protocols.
It should look like this:
ssl_protocols TLSv1.2 TLSv1.3; # Dropping SSLv3, ref: POODLE
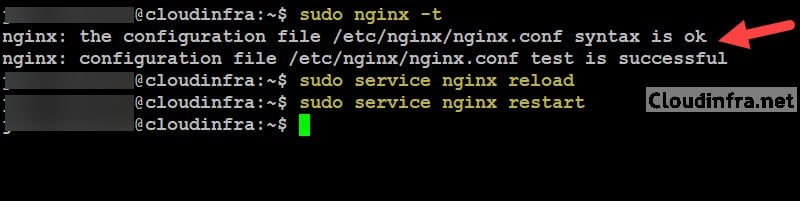
After you have made this change in nginx.conf file. We need to validate the Nginx file, reload it, and restart the Nginx service using the commands below.
Validate nginx file and reload
sudo nginx -t sudo service nginx reload sudo service nginx restart OR sudo systemctl restart nginx
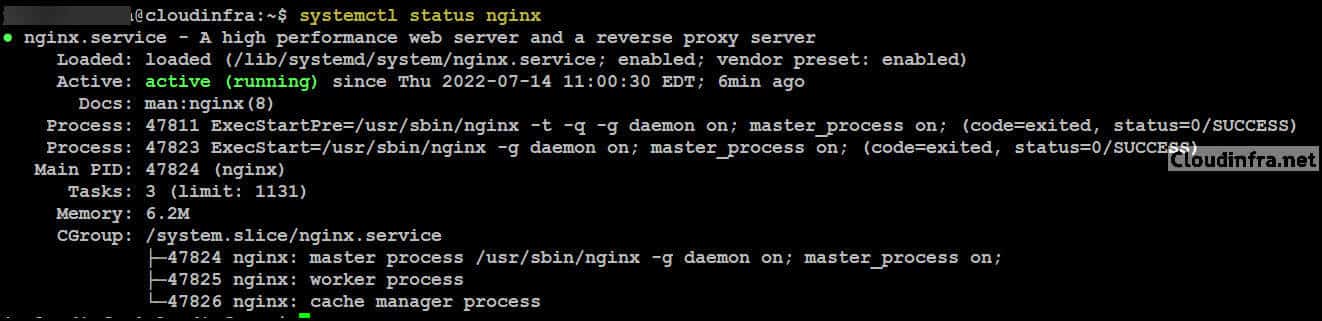
Check the Nginx service’s status to ensure it is showing as Active. You can run the below command to find the status of the Nginx service.
Verify nginx service status
systemctl status nginx
Once you have made the change in the nginx.conf file, you can also check this file sudo nano /etc/nginx/sites-available/xyz.com (replace xyz.com with your domain name) and make sure TLS1.0 and TLS1.1 are not showing under ssl_protocols.
Test and Confirm if TLS 1.0 and TLS 1.1 are disabled on Nginx Server
There are several ways to test it. However, I will be using an open-source utility called OpenSSL. First, you need to install OpenSSL on your system.
To learn more, visit https://www.openssl.org/source/. If you have Git installed on your system, you can find the openssl.exe file under C:\Program Files\Git\usr\bin.
To download Git, use the link https://git-scm.com/downloads. I will use the openssl.exe file, available under C:\Program Files\Git\usr\bin.
- Browse to the C:\Program Files\Git\usr\bin path using the change directory command cd C:\Program Files\Git\usr\bin and then use below OpenSSL commands to test TLS for the domain.
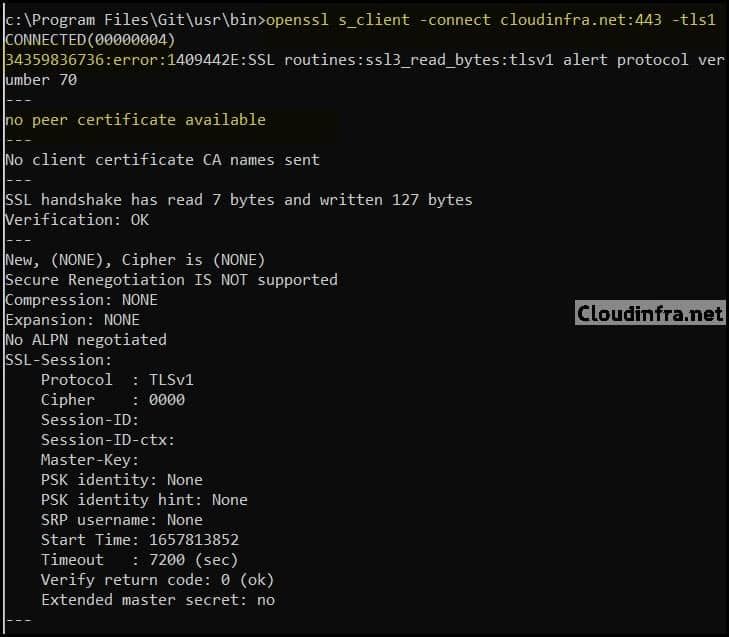
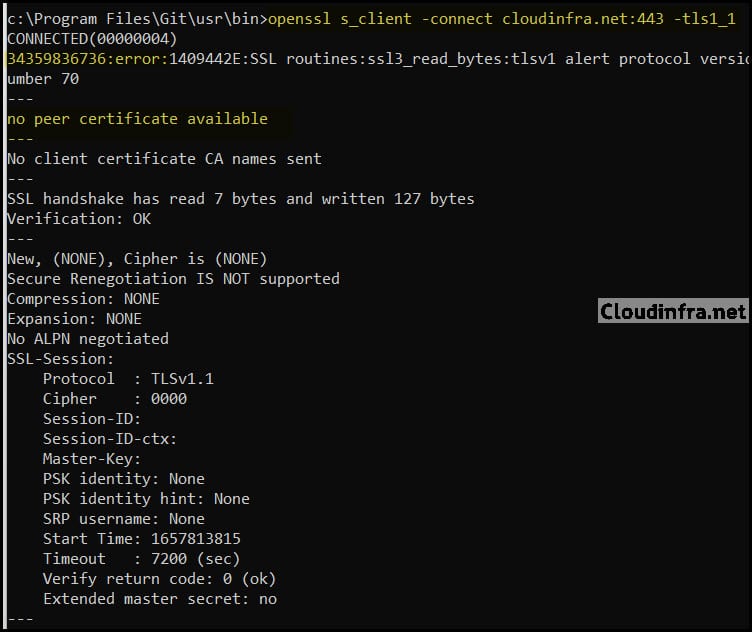
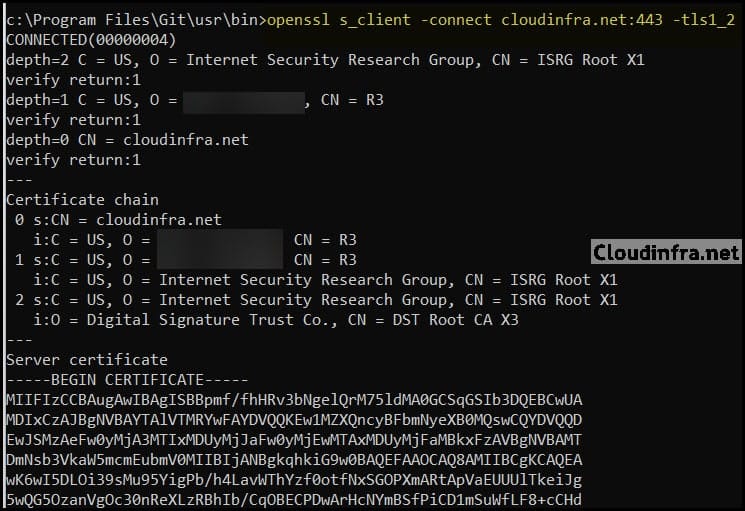
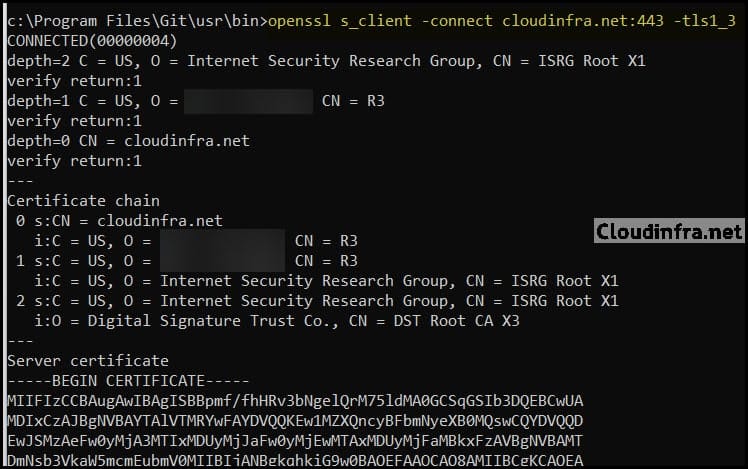
- I have run the tests on my site and got the below results, which show that TLS1.0 and TLS1.1 are disabled, and TLS1.2 and TLS1.3 are connected and enabled.
Test TLS using OpenSSL
openssl s_client -connect cloudinfra.net:443 -tls1 openssl s_client -connect cloudinfra.net:443 -tls1_1 openssl s_client -connect cloudinfra.net:443 -tls1_2 openssl s_client -connect cloudinfra.net:443 -tls1_3
Test and confirm TLS 1.0 status using OpenSSL on Nginx
Test and confirm TLS 1.1 status using OpenSSL on Nginx
Test and confirm TLS 1.2 status using OpenSSL on Nginx
Test and confirm TLS 1.3 status using OpenSSL on Nginx
Conclusion
To make your server or website more secure, you should disable TLS1.0 and TLS1.1 protocols. You can enable TLS 1.2 and TLS1.3 in the nginx.conf file and then restart the nginx service. If you want to disable TLS1.0 and TLS1.1 protocols on Windows 10/11 devices, you can follow this article: Disable TLS 1.0 and TLS 1.1 on Windows 10/11 machines through GPO.
