In this blog post, I will show you the steps to fix the issue when download from SharePoint, exchange online and OneDrive is getting blocked even if the device is compliant. You have created a Conditional Access (CA) Policy in which you have defined a session control for the Conditional Access App control setting to block downloads from Microsoft Online services, e.g., Sharepoint, Teams, Exchange Online, etc. In this policy, you have excluded the compliant devices using a Device State condition.
However, when users work from a compliant device, they cannot download files. If additional Defender for Cloud apps policies / Conditional Access policies are in place targeted to non-compliant devices, those policies will also not be applicable.
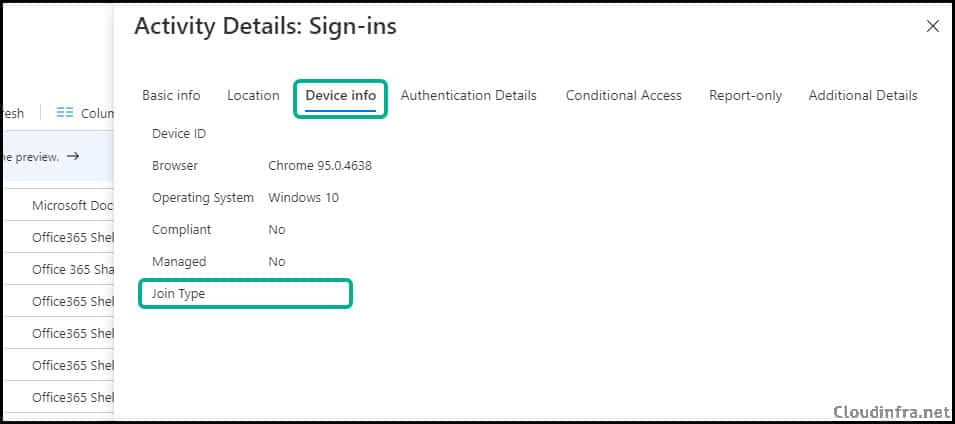
When you check the user’s sign-in logs on the Entra ID admin center, you will find that the Join type is blank, and therefore, the device-compliant calculation says Compliant: No.
Therefore, even if the device is compliant, the device compliance details are not sent to Entra ID. This occurs when you access any cloud-based application using a web browser, for example, Google Chrome or Microsoft Edge.
The device-compliant setting only works with the following supported browsers. The device check fails if the web browser is running in private mode or if cookies are disabled.
Google Chrome requires an Extension called Windows Accounts to identify whether a Device is compliant. For Microsoft Edge, you need to be logged in to the Edge browser to identify the Device’s status.
| OS | Browsers |
|---|---|
| Windows 10 | Microsoft Edge, Internet Explorer, Chrome, Firefox 91+ |
| Windows 8 / 8.1 | Internet Explorer, Chrome |
| Windows 7 | Internet Explorer, Chrome |
| macOS | Microsoft Edge, Chrome, Safari |
| iOS | Microsoft Edge, Intune Managed Browser, Safari |
| Android | Microsoft Edge, Intune Managed Browser, Chrome |
| Windows Server 2019 | Microsoft Edge, Internet Explorer, Chrome |
| Source: Microsoft |
Contents
Install Windows Accounts Extension for Google Chrome
Install the Windows Accounts Google Chrome Extension and log in using organization credentials. The description of this extension provides information that this plugin is required if your organization has implemented a conditional access policy.
Install this extension, log in using the organization’s email ID and password, then log in to SharePoint, or OneDrive. You will be able to download the files this time. Let’s check how it looks on the Entra ID User sign-in logs.

| Windows Accounts Extension Information |
|---|
| Sign in to supported websites with accounts on Windows 10/11 Use this extension to sign in to supported websites with accounts on Windows 10 and later versions. If you have a Microsoft-supported identity on Windows 10 or later, you won’t be required to enter your credentials to sign in to supported websites. You’ll need to use this extension if your organization has implemented a conditional access policy. Currently, this extension supports Azure Active Directory identities. |
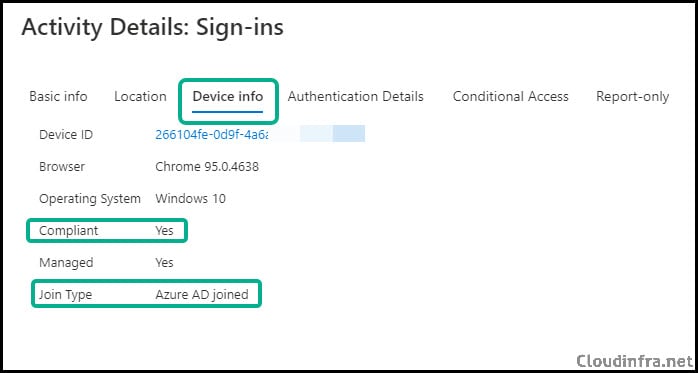
Now, we can see that the device compliance status is being sent to Entra ID if you have a conditional access policy that allows downloads from Sharepoint/OneDrive/Exchange Online from a compliant device only. Then, this device will no longer be blocked as it is in a compliant state.
Microsoft Edge Browser Support
When using the Microsoft Edge browser, sign in using your organization account by using below steps:
- Open Microsoft Edge browser application.
- Select Profile image in the browser taskbar.
- Click on Sign in.
- Select or use your organization email ID and password to sign in to the Microsoft Edge browser.
You should be able to download the documents from Sharepoint/OneDrive/MS Teams or any other Microsoft 365 application, provided you are on a compliant device, and your IT administrator has allowed downloading files on a compliant device.
Conclusion
In this blog post, we have seen how to send device compliance status to Entra ID when using the Google Chrome browser. You will require a Windows Accounts extension for this. Microsoft Edge natively supports authentication with Entra ID, therefore you will not require any extension for Microsoft Edge browser.

Hi,
I have similar case: I have used Filter for devices in Conditional Access to exclude devices with logic “device ownership equal Company” but it does not seem to work:
– devices that are non-compliant/not enrolled into Intune are applied with the session control.This is Correct!
-devices that are non-compliant and has “Company” device ownership attribute still get applied with session control, which is weird as there is an exclusion!
May I know how to fix it?