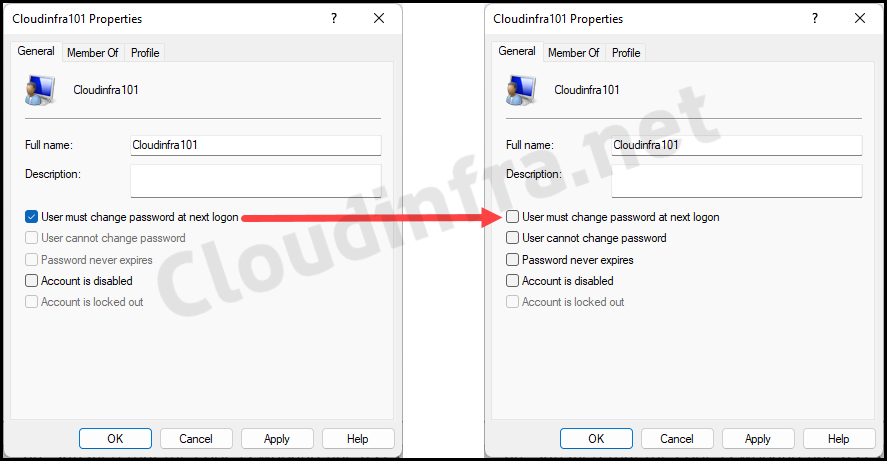
In this blog post, we will see how to enable/disable User must change password at next logon using Intune. We will utilize PowerShell scripts to configure this setting.
If you enable this setting, it will force the user to change the password at the next logon. If you disable or uncheck this setting, user is not required to change the password at next logon.
There are many ways to deploy a PowerShell script using Intune. You can use Intune device remediations or deploy a PowerShell script using Device > Scripts and remediations > Platform scripts from the Intune admin center. We are going to use the PowerShell script deployment method.
I’ll be using scripts from a blog post that explains how to manage User must change password at next logon setting using PowerShell. It offers two scripts for this purpose, one to disable and the other to enable this setting for local user accounts on Windows 10/11 devices.
Note
Contents
Prepare a PowerShell Script
Let’s prepare the PowerShell script which will disable or enable User must change password at next logon flag for a local user account on Windows devices. As an example user, I will be using cloudinfra101 local user account already existing on the target device.
- Copy below PowerShell code and replace the name of the local user account cloudinfra101 with the user account you want to configure. Save the PowerShell script as DisableChangePassword.ps1.
- Test the script on a test device first before proceeding to the next step for creating an Intune deployment.
Below script will remove the flag or uncheck the checkbox for User must change password at next logon setting for user account cloudinfra101. If you want to tick or enable this flag, then you simply have to change the line:
$usr.PasswordExpired = 1. I have provided the code for enabling this setting at the end of this blog post.Note
DisableChangePassword.ps1
<#
.DESCRIPTION
This script disables "User must Change password at next logon" flag
for a specified local user account
Author: Jatin Makhija
Website: cloudinfra.net
Version: 1.0.0
#>
# Bind to the local user account
$usr = [ADSI]"WinNT://$env:ComputerName/cloudinfra101,user"
# Set the 'PasswordExpired' property to 0 disable "User must Change password at next logon"
$usr.PasswordExpired = 0
# Save the changes
$usr.SetInfo()
# Optionally, display a message indicating the change was made
Write-Host "The password expiration status for user 'cloudinfra101' has been updated."
Deploy the PowerShell Script
After you’ve tested the PowerShell script, and it’s ready for deployment, the next step is to create a deployment using the Intune admin center. Let’s check the steps:
- Sign in to the Intune admin center > Device > Scripts and remediations > Platform scripts.
- Click on + Add and then Select Windows 10 and later.
- Basics: On the basics tab, provide a Name and Description.
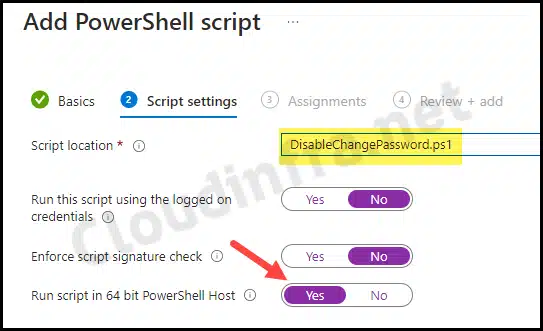
- Script settings:
- Script location – Browse to the PowerShell script DisableChangePassword.ps1
- Run this script using the logged on credentials – Change it to No
- Enforce script signature check – Change it to No
- Run script in 64 bit PowerShell Host – Change it to Yes
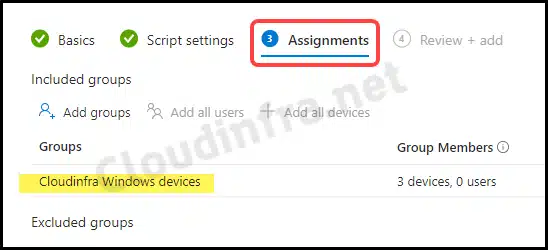
- Assignments: Click on Add groups and select an Entra security group containing Windows devices.
- Review + add: The final step is to review the information and click Add to start the deployment process.
Sync Intune Policies
The device check-in process might not begin immediately. If you’re testing this policy on a test device, you can manually kickstart the Intune sync from the device itself or remotely through the Intune admin center.
Alternatively, you can use PowerShell to force the Intune sync on Windows devices. Restarting the device is another way to trigger the Intune device check-in process.
End User Experience
On the target device, PowerShell script will be downloaded on the device at the following location: C:\Program Files (x86)\Microsoft Intune Management Extension\Policies\Scripts.
After the download, the script is executed. It’s important to note that the scripts downloaded on the device will be automatically deleted after execution, so you may find this folder empty once the script has been run.
The script will be executed in the system context, since we’ve selected Run this script using the logged-on credentials as No. while creating the deployment.
To verify whether the PowerShell script we deployed has been executed on the target devices, we can check the flag User must change password at next logon is disabled for cloudinfra101 user account.

Enable User must change password at next logon flag for a local user account
You can enable the User must change password at next logon flag with the following PowerShell script. This script sets or checks the flag for a local user account ($usr.PasswordExpired = 1).
DisableChangePassword.ps1
<#
.DESCRIPTION
This script enables "User must Change password at next logon" flag
for a specified local user account
Author: Jatin Makhija
Website: cloudinfra.net
Version: 1.0.0
#>
# Bind to the local user account
$usr = [ADSI]"WinNT://$env:ComputerName/cloudinfra101,user"
# Set the 'PasswordExpired' property to 1 to enable "User must Change password at next logon"
$usr.PasswordExpired = 1
# Save the changes
$usr.SetInfo()
# Optionally, display a message indicating the change was made
Write-Host "The password expiration status for user 'cloudinfra101' has been updated."
Intune Logs for PowerShell script deployment
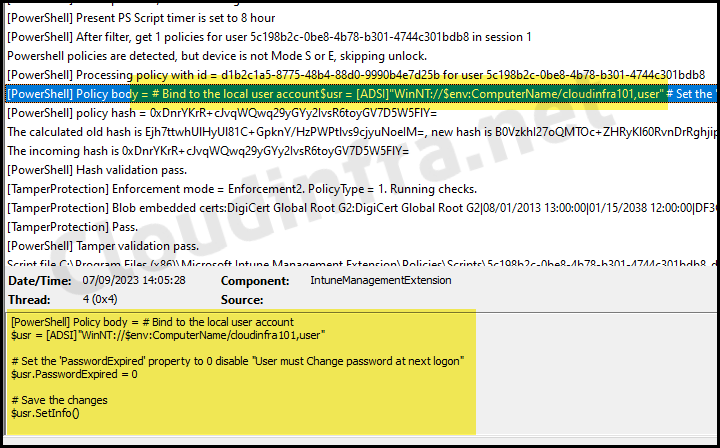
You can verify the PowerShell script execution status by checking the Intune Management Extension logs. This is one of the way to confirm script execution. For other ways to check and confirm the script status, please refer to my other blog post: Deploy a PowerShell Script using Intune.
- Navigate to C:\ProgramData\Microsoft\IntuneManagementExtension\Logs.
- Please find the most recent IntuneManagementExtension.log file and open it
- The best way to open .log files is by using a CMTrace tool.
- Search for Policy ID and check Policy result. As you can see, Policy result is showing as Success for this deployment.
Conclusion
In this blog post, we’ve learned how to enable or disable the User must change password at next logon flag for a local user account on Windows 10 or Windows 11 devices. To prevent script failure, ensure the specified local user account exists on the target devices.

This doesn’t seem to work anymore. I am getting below error when I tried to run the script in Powershell
Exception calling “setInfo” with “0” argument(s): “Logon Failure: EAS policy requires that the user change their password before
this operation can be performed.
“