In this guide, I will cover the steps to create defender antivirus exclusions using Intune. You can exclude certain files, folders, or Processes from scanning via Microsoft Defender Anti-virus. Exclusions will be applied to Scheduled Scans, On-demand scans, and always-on real-time protection and monitoring.
Microsoft Defender Antivirus includes many built-in automatic exclusions based on known operating system behaviors. If you exclude a specific file or folder path from scanning and real-time monitoring in Microsoft Defender, you must ensure that you trust that file or content in the folder path and its contents are not malicious.
If you have decided to whitelist/exclude a File or Folder Path from the scan in Microsoft Defender, there are different ways to achieve this.
For example, you can create a Group Policy Object if the On-premise Active Directory manages all your devices. If your organization is fully cloud-based and all devices are Microsoft Entra Joined and managed by Intune, then you can create a Device restriction profile.
Other methods include using PowerShell to configure Microsoft Defender Exclusions, or manually logging on to each PC as an administrator and configuring the exclusions.
In this blog post, we will see how to configure File or Folder Exclusions in Microsoft Defender using Intune and manual methods on the device.
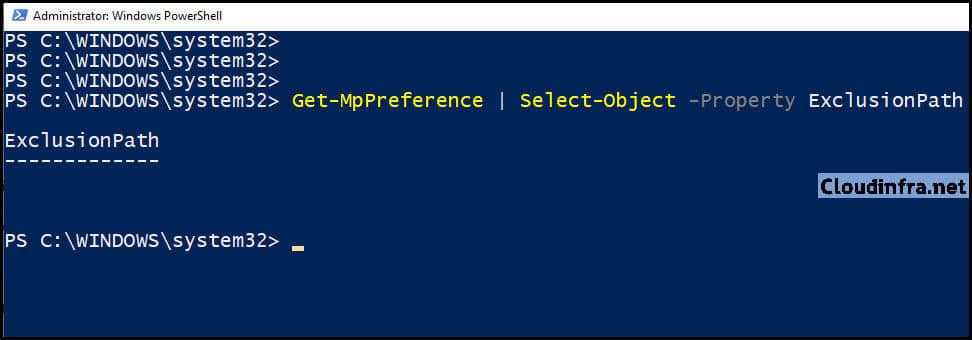
You can check the list of exclusions currently applied in Defender using the PowerShell command below. I have checked my system, and no exclusions are currently applied. Once we apply the Exclusions, we will re-run this command on the device to check if it has been added to the list.
Check Defender Exclusions on your device
Get-MpPreference | Select-Object -Property ExclusionPath
Create Microsoft Defender Antivirus Exclusions using Intune
You can create Microsoft Defender exclusions through the Intune admin center by following these steps:
- Sign in to the Intune admin center.
- Click on Devices > Configuration > Create > New Policy.
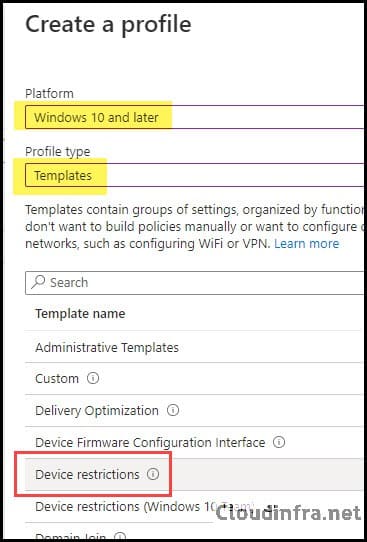
- Select Platform as Windows 10 and later and Profile Type as Templates.
- Select Device restrictions from the list of Templates and click Create.
- Basics Tab: Provide the Name and Description of the Policy and click on Next.
Configuration Settings
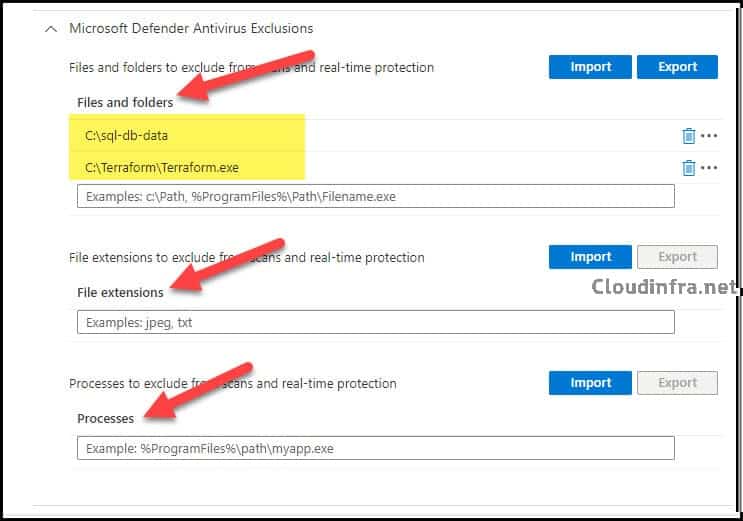
Scroll down on the page to find Microsoft Defender Antivirus category and expand it. Scroll down further to find Microsoft Defender Antivirus Exclusions. You can provide the file name or folder path that you want to exclude from AV scanning under Files and folders.
I would be excluding C:\sql-db-data and a file named Terraform.exe from scanning and monitoring by defender. You also have the option to exclude certain file extensions or processes from scanning and real-time protection.
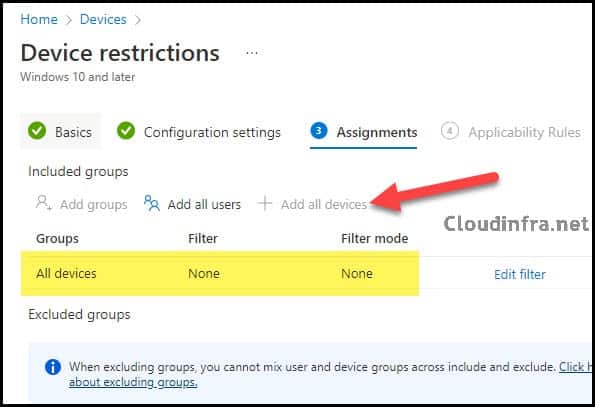
- Assignments: You can either add an Entra security group containing Windows devices or apply these exclusions to All Intune-managed devices. For the purpose of the demo, I have applied this policy to All devices.
- Review + create: Review the configuration and click on Create.
Sync Intune Policies
The device check-in process might not begin immediately. If you’re testing this policy on a test device, you can manually kickstart Intune sync from the device itself or remotely through the Intune admin center.
Alternatively, you can use PowerShell to force the Intune sync on Windows devices. Restarting the device is another way to trigger the Intune device check-in process.
End User Experience
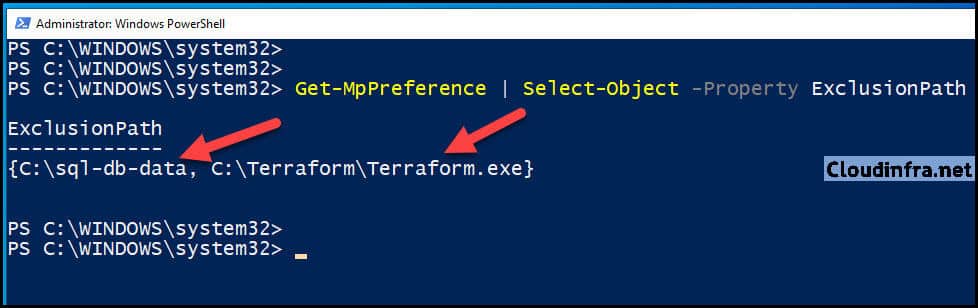
After the policy is applied on the target devices, you can check and confirm using below PowerShell command if the Exclusions are applied in Microsoft Defender AV.
Confirm Defender AV Exclusions using PowerShell
Check and Confirm Defender Exclusions using PowerShell
Get-MpPreference | Select-Object -Property ExclusionPath
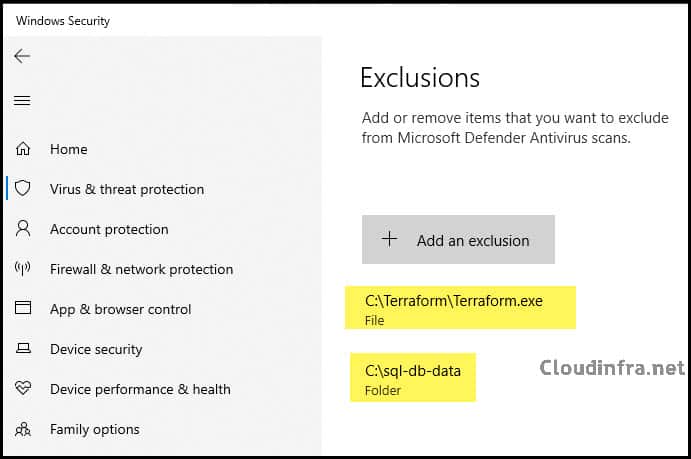
Confirm Defender AV Exclusions using GUI
Open Settings > Update & Security > Windows Security > Virus & Threat Protection > Virus & Threat Protection Settings > Click on Manage Settings > Scroll down to find Exclusions > Click on Add or remove exclusions.
You will see the two exclusions we implemented: one for the SQL-db-data folder and another for the Terraform.exe file.
| Shortcut to Open Windows Security |
|---|
You can also go to Start > Run and then type windowsdefender: to open the Windows Security window directly. Then click on Virus & Threat Protection > Virus & Threat Protection settings > Click on Manage Settings > Scroll down to find Exclusions > Click on Add or remove exclusions to manage the Exclusion List. |
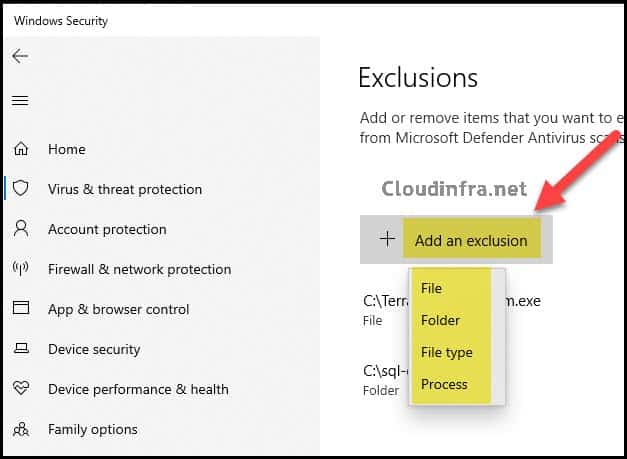
Add Microsoft Defender Antivirus Exclusions Manually
You can also manually click + Add an exclusion to add an exclusion on your PC. You will notice the same options we configured through the Intune Device Restriction Configuration Profile, including file, folder, file type, or process-based exclusions.
Conclusion
Microsoft Defender Antivirus will skip scanning and real-time monitoring for excluded files, folders, or processes. For instance, if you exclude a folder by specifying its path, like C:\sql-db-data, Defender AV will exempt all its files from scanning and monitoring.
Awareness of the potential risks of not scanning certain files or folders is essential. Ensure you only add folder locations you trust and are confident they don’t contain malware or unknown files.
