In this blog post, I will demonstrate an Intune policy to enable/disable Defender SmartScreen in Edge using Intune. Microsoft Defender SmartScreen is a security feature built into Windows and Edge browser that helps protect from phishing attacks, malicious websites, and potentially harmful downloads.
Below are some benefits of Microsoft Defender SmartScreen:
- Reputation-based URL filtering.
- Download protection.
- Anti-phishing and Anti-malware support.
- Blocking URLs associated with potentially unwanted applications (PUAs).
- Management through Group Policy and Intune.
For a better understanding of how Microsoft Defender SmartScreen works, refer to the Microsoft Docs link. In this blog post, I will focus on how to manage and configure Defender SmartScreen settings in Edge on Windows 10/11 devices using Intune. You can further secure the Edge browser by enabling Enhanced Security Mode and typosquatting protection, in addition to ensuring that SmartScreen is enabled.
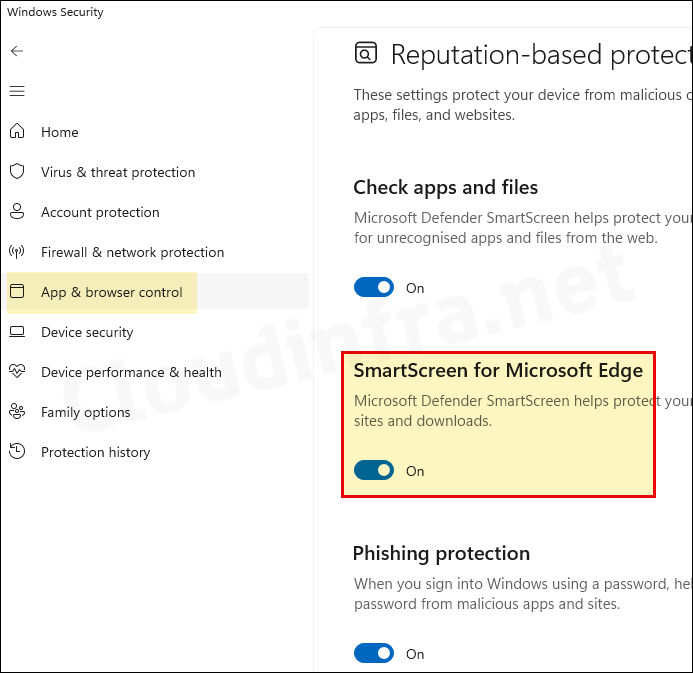
For manually enabling or disabling Defender SmartScreen for Microsoft Edge browser, Search in the Start menu for Windows Security and click on it to launch it > Go to App & browser control > Under Reputation-based protection click on Reputation-based protection settings > enable or disable SmartScreen for Microsoft Edge setting using the on/off toggle switch.
Contents
Configure Microsoft Defender SmartScreen Intune Policy
You can enable or disable Microsoft defender SmartScreen in Edge browser using an Intune Settings catalog policy Configure Microsoft Defender SmartScreen or Configure Microsoft Defender SmartScreen (User). Let’s check the steps:
- Sign in to Intune admin center > Devices > Windows > Configuration > Create > New Policy.
- Platform: Windows 10 and later
- Profile type: Settings catalog
- Click Create.
- On the Basics tab, provide a Name and Description of the policy and click Next.
- On Configuration settings tab, click on + Add settings and use the Settings picker to search using defender smartscreen keyword and select Microsoft Edge\SmartScreen settings category. Select the policy, Configure Microsoft Defender SmartScreen.
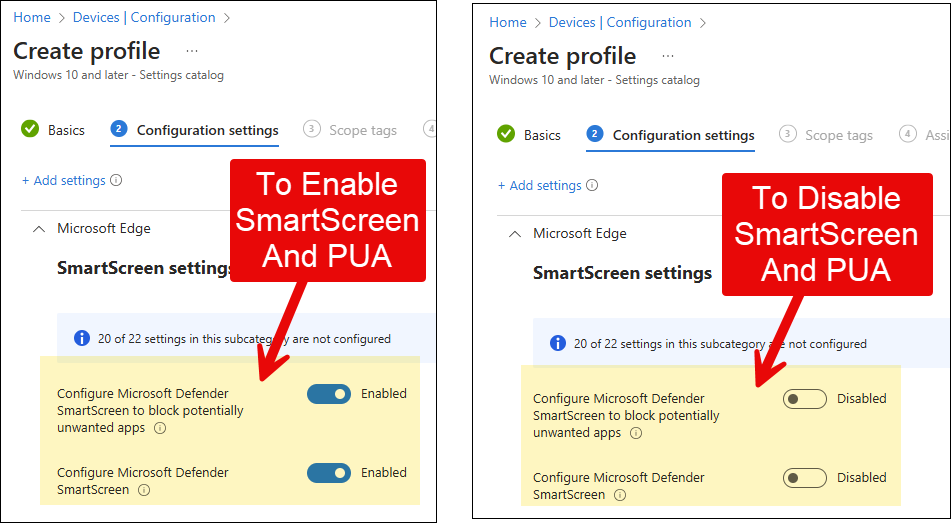
I also recommend selecting another security policy for the Edge browser, called Configure Microsoft Defender SmartScreen to block potentially unwanted apps. This policy blocks potentially unwanted apps and provides warning messages to help protect users from adware, coin miners, bundleware, and other low-reputation apps hosted by websites. SmartScreen PUA is turned off by default but can be enabled through this policy setting.
Please note that the Potentially Unwanted App (PUA) blocking setting depends on the SmartScreen for Microsoft Edge setting. If you disable or turn off SmartScreen for Microsoft Edge, PUA blocking will also be turned off.Potentially Unwanted App (PUA) blocking
- Below screenshot shows that there are two versions of each setting: one with (User) at the end and one without. The policy without (User) at the end is a device-based policy and applies in the device context. This means that once this policy is applied, it will affect all users using the particular device. I recommend assigning this policy to an Entra security group containing devices. I will be selecting and using the device-based policy for demonstration purposes.
- The policy with (User) at the end is a user-based policy and is applied in the user context. It is recommended to assign a user-based policy to an Entra security group that contains users instead of devices. This will ensure that the policy applies only to the users who are part of the group.
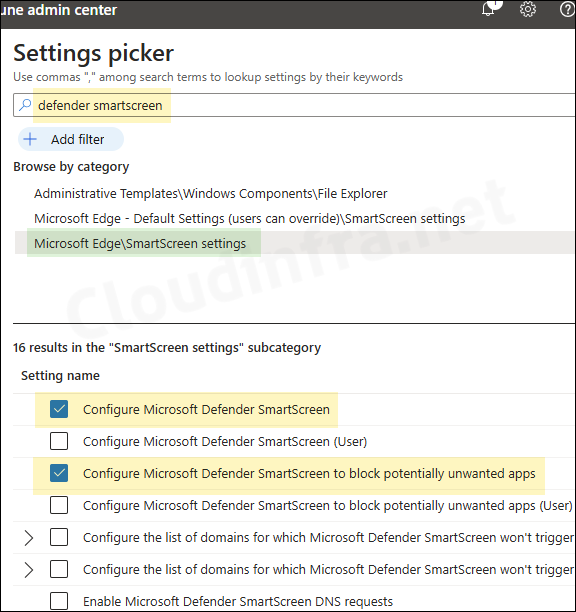
- Use the toggle switches next to Configure Microsoft Defender SmartScreen and Configure Microsoft Defender SmartScreen to block potentially unwanted apps to enable or disable these settings.
- By default, SmartScreen for Edge is enabled on Windows devices, but the Block PUA setting is not enabled by default. I recommend enabling both of these settings and deploying them to Windows devices. This will ensure that these settings are enabled and managed by Intune. Users will also not be able to modify these settings, as they will be grayed out for them.
This policy setting lets you configure whether to turn on Microsoft Defender SmartScreen. Microsoft Defender SmartScreen provides warning messages to help protect your users from potential phishing scams and malicious software. By default, Microsoft Defender SmartScreen is turned on. If you enable this setting, Microsoft Defender SmartScreen is turned on. If you disable this setting, Microsoft Defender SmartScreen is turned off. If you don’t configure this setting, users can choose whether to use Microsoft Defender SmartScreen. This policy is available only on Windows instances that are joined to a Microsoft Active Directory domain; or on Windows 10 Pro or Enterprise instances that are enrolled for device management.
Microsoft Official definition of Policy setting Configure Microsoft Defender SmartScreen
This policy setting lets you configure whether to turn on blocking for potentially unwanted apps with Microsoft Defender SmartScreen. Potentially unwanted app blocking with Microsoft Defender SmartScreen provides warning messages to help protect users from adware, coin miners, bundleware, and other low-reputation apps that are hosted by websites. Potentially unwanted app blocking with Microsoft Defender SmartScreen is turned off by default. If you enable this setting, potentially unwanted app blocking with Microsoft Defender SmartScreen is turned on.
If you disable this setting, potentially unwanted app blocking with Microsoft Defender SmartScreen is turned off. If you don’t configure this setting, users can choose whether to use potentially unwanted app blocking with Microsoft Defender SmartScreen. This policy is available only on Windows instances that are joined to a Microsoft Active Directory domain; or on Windows 10 Pro or Enterprise instances that are enrolled for device management.
Microsoft Official definition of Policy setting Configure Microsoft Defender SmartScreen to block potentially unwanted apps
- Scope tags (optional): A scope tag in Intune is an RBAC label you add to resources (policies, apps, devices) to limit which admins can see and manage them. For more Information, read: How to use Scope tags in Intune.
- Assignments: Assign the policy to Entra security groups that contain the target users or devices. As a best practice, pilot with a small set first; once validated, roll it out more broadly. For guidance on assignment strategy, see Intune assignments: User groups vs. Device groups.
- Review + create: Review the deployment summary and click Create.
Monitoring Defender SmartScreen Intune Policy
- Sign in to the Intune admin center > Devices > Configuration.
- Select the Device Configuration profile you want to work with, and at the top of the page, you’ll see a quick view of the Success, Failure, Conflict, Not Applicable, and In Progress status.
- Click on View report to access more detailed information.
Sync Intune Policies
The device check-in process might not begin immediately. If you’re testing this policy on a test device, you can manually kickstart Intune sync from the device itself or remotely through the Intune admin center.
Alternatively, you can use PowerShell to force the Intune sync on Windows devices. Restarting the device is another way to trigger the Intune device check-in process.
End User Experience
After the deployment is successfully completed, you can check if the policy has been applied in two ways. The first method is by using the Windows Security, and the second is by using Microsoft Edge browser. Let’s go through both methods to verify if the Intune policy we configured has been applied to the target devices.
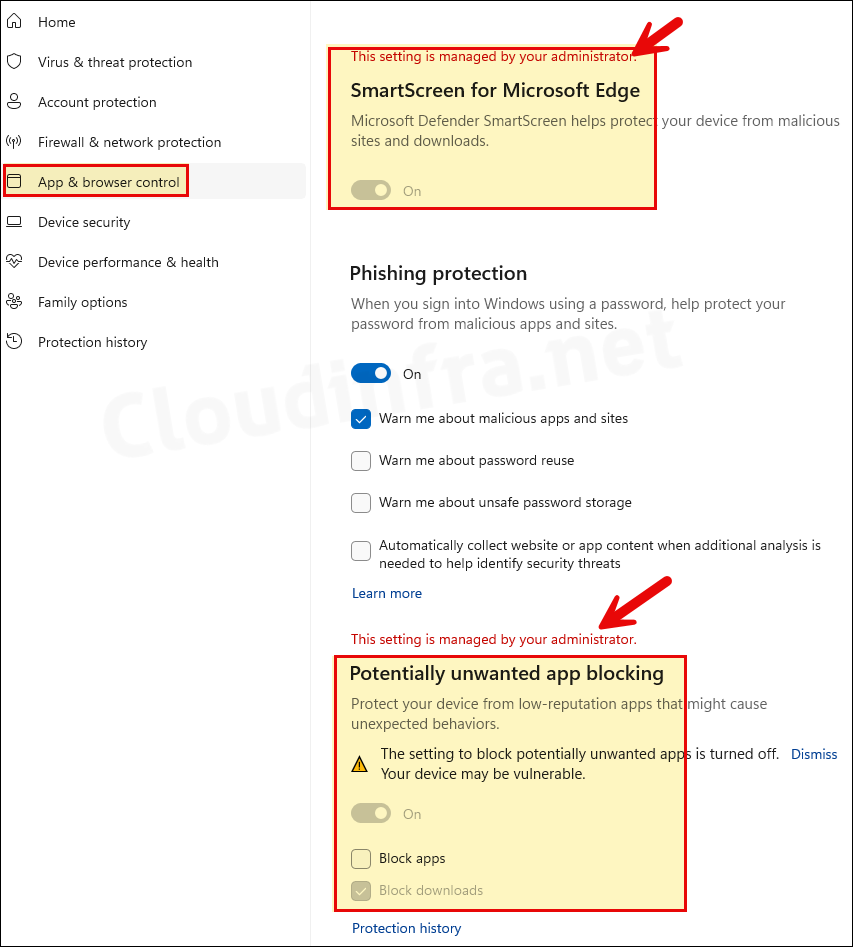
- Search in the Start menu for Windows Security and click on it to launch it > Go to App & browser control > Under Reputation-based protection click on Reputation-based protection settings > SmartScreen for Microsoft Edge setting is enabled and greyed out. You will also find that Potentially unwanted app blocking setting is also enabled and greyed out.
- Second method to check and confirm if the Microsoft Defender SmartScreen and Block Potentially unwanted apps policy is applied successfuly is by using Microsoft Edge browser. Let’s check the steps:
- Launch Microsoft Edge browser.
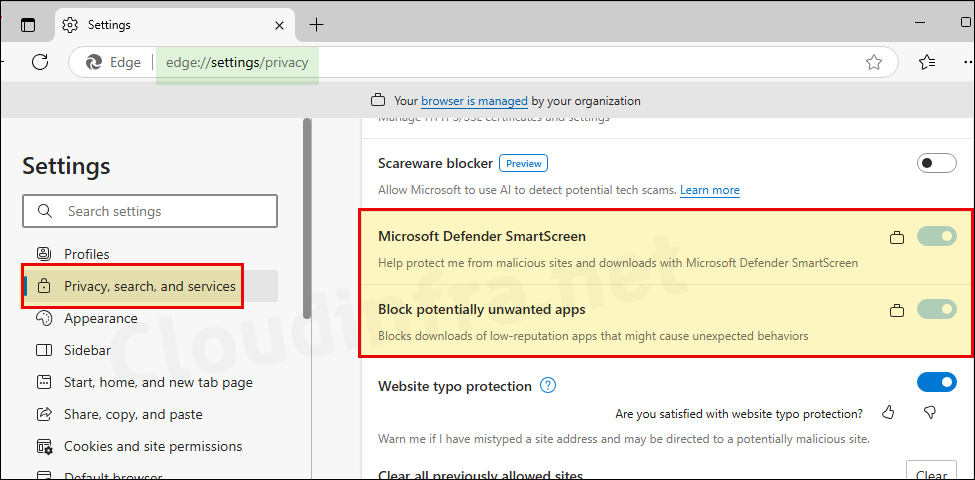
- In the Address bar, type edge://settings/privacy > Under Security, you will find that Microsoft Defender SmartScreen and Block Potentially unwanted apps are enabled and greyed out. This confirms that our Intune policy has been applied successfully.
OMA-URI Setting for Managing SmartScreen
Managing Defender SmartScreen setting using settings catalog is easy and straightforward. Its the recommended method for managing SmartScreen settings. However, you can also use an OMA-URI setting to enable or disable it by creating a custom device configuation intune policy. Refer to the post: Create a local admin using Intune which uses OMA-URI setting and will help you creating a custom profile.
OMA-URI Setting for SmartScreen: EnableSmartScreenInShell
Other Microsoft Edge SmartScreen Settings Available on Intune admin center
Below are all the policies currently available for configuring Microsoft Defender SmartScreen in Edge on Intune admin center. I have not demonstrated or tested all of these policies, but you can use them as per your requirements. For more information about each policy, you can select the policy in Intune and hover your mouse over the (i) icon to get more details.
| Policy Name |
|---|
| Configure Microsoft Defender SmartScreen |
| Configure Microsoft Defender SmartScreen (User) |
| Configure Microsoft Defender SmartScreen to block potentially unwanted apps |
| Configure Microsoft Defender SmartScreen to block potentially unwanted apps (User) |
| Configure the list of domains for which Microsoft Defender SmartScreen won’t trigger warnings |
| Configure the list of domains for which Microsoft Defender SmartScreen won’t trigger warnings (User) |
| Disable SmartScreen AppRep based warnings for specified file types on specified domains |
| Disable SmartScreen AppRep based warnings for specified file types on specified domains (User) |
| Enable Microsoft Defender SmartScreen DNS requests |
| Enable Microsoft Defender SmartScreen DNS requests (User) |
| Enable new SmartScreen library (obsolete) |
| Enable new SmartScreen library (obsolete) (User) |
| Force Microsoft Defender SmartScreen checks on downloads from trusted sources |
| Force Microsoft Defender SmartScreen checks on downloads from trusted sources (User) |
| Prevent bypassing Microsoft Defender SmartScreen prompts for sites |
| Prevent bypassing Microsoft Defender SmartScreen prompts for sites (User) |
| Prevent bypassing of Microsoft Defender SmartScreen warnings about downloads |
| Prevent bypassing of Microsoft Defender SmartScreen warnings about downloads (User) |
Testing Microsoft Defender SmartScreen in Edge
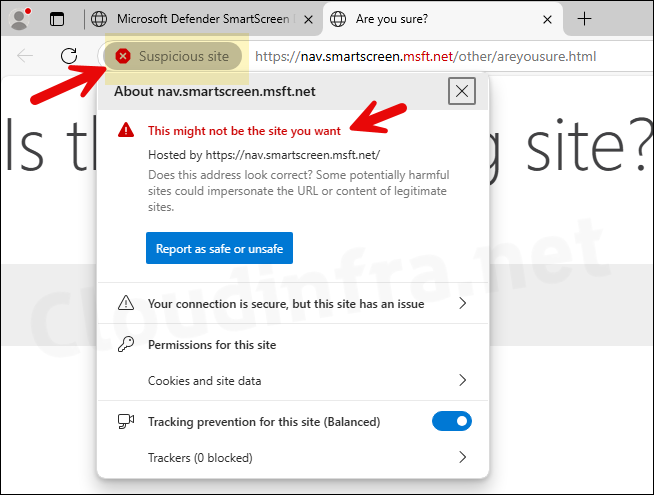
You can test and confirm if Microsoft defender SmartScreen is working in Edge browser by trying to access a website which could be suspicious. Defender SmartScreen will automatically activate to check to see if the website could be harmful. Edge will also put a tag in the address bar which highlights that the website is a Suspicious site.
If the website is known and you know that the website is a safe website, you can click on the button on the pop-up to Report the website as Safe and same goes to report an Unsafe website.
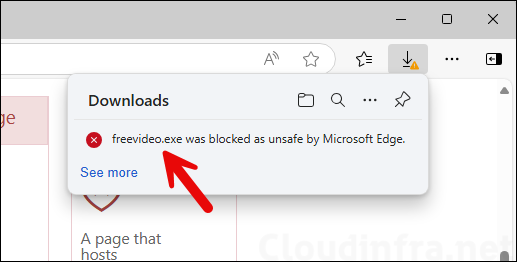
- Below screenshot shows an attempt to download a file which is blocked by Microsoft Edge as its found as unsafe.
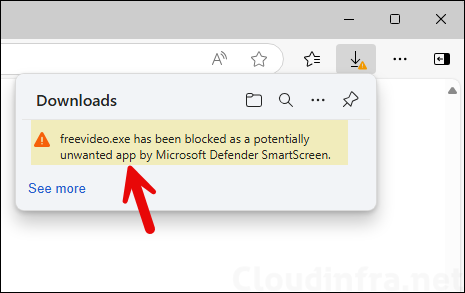
- Below screenshot shows an attempt to download a Potentially unwanted app (PUA). Its blocked by Microsoft Edge browser with a message “<app name> has been blocked as a potentially unwanted app by Microsoft Defender SmartScreen.“

Very informative and easy to read instructions.