In this blog post, I will demonstrate the steps to configure automatic account management in Windows LAPS. LAPS is Windows Local Administrator Password Solution (LAPS) which helps to protect local administrator account from pass-the-hash or lateral-traversal attacks by enforcing password complexity and length requirements, backup of the password to Entra ID, and rotating its password automatically.
In my previous post, I have provided the steps to Implement Windows LAPS with Intune and also meeting its prerequisite of creation of a custom local admin account. A local administrator account must exist on the target Windows devices before it can be managed by LAPS. You can also use a built-in administrator account without specifying any administrator account name while creating a LAPS policy on Intune admin center. However, you have to ensure that the account is enabled. All of these can be done using Automatic account management CSP settings.
With Intune service release 2507 (July 2025), LAPS for macOS is now available. Setup and configure macOS LAPS on Intune admin center using this step-by-step guide: Setup and Configure LAPS for macOS via Intune.
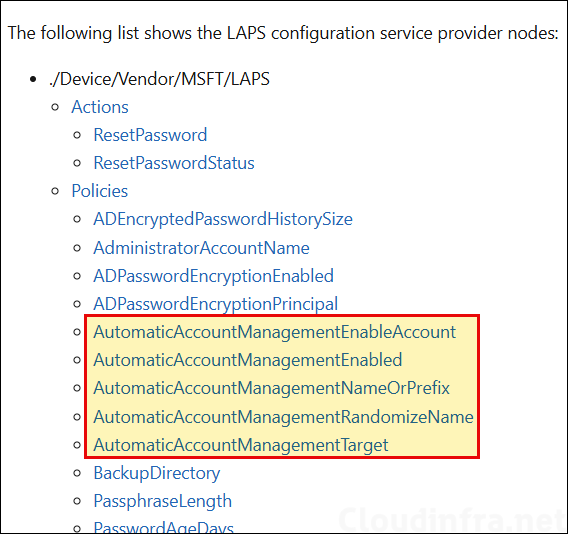
Automatic account management LAPS CSP settings makes it easier to create and manage local administrator account. Windows LAPS CSP Policies exist under ./Device/Vendor/MSFT/LAPS node. You can use these policy settings to create a custom local administrator account, enable or disable the account. Provide a prefix for the account, use a built-in administrator account instead of a custom local admin account, or even create a random unique local admin account on each target device. Below are the list of CSP Policies available for automatic account management in Windows LAPS.
Contents
Automatic Account Management CSP Settings
Now that we understand about what is Automatic account management in Windows LAPS and how it could be useful. Let’s look at each CSP setting in more detail, and after that we will proceed to create an Intune policy to demonstrate it.
| CSP Setting | Description |
|---|---|
| AutomaticAccountManagementEnableAccount | Use this setting to Enable or Disable the target account. Data type is boolean. True: target account will be enabled. False: target account will be disabled. If not specified, the default value of false will be used. |
| AutomaticAccountManagementEnabled | Use this setting to Enable or Disable Automatic account management with Windows LAPS. Data type is boolean. True: target account will be automatically managed. False: target account will not be automatically managed. If not specified, the default value of false will be used. |
| AutomaticAccountManagementNameOrPrefix | Use this setting to configure the name of the custom local admin account or provide a prefix for the managed administrator account. Data type is String. If not specified, this setting will default to WLapsAdmin. |
| AutomaticAccountManagementRandomizeName | Use this setting to configure if the name of the managed account uses a random numeric suffix each time the password is rotated. Data type is boolean. True: name of the target account will use a random numeric suffix. False: name of the target account will not use a random numeric suffix. If not specified, default value of false will be used. |
| AutomaticAccountManagementTarget | Use this setting to configure which account is automatically managed. Data Type: Integer. Set this 0 to manage built-in administrator account Set this to 1 to manage the custom local admin account created by LAPS. If not specified, default value of 1 will be used. |
Create Automatic Account Management Intune Policy
For demonstration purpose, I will create an automatic account management Intune policy which will create a local admin account called admin-cloudinfra. I will not use a randomize name for local admin account, instead provide a static account name which will be created on the target Windows devices.
If you prefer to create a randomize local account name, then you can set AutomaticAccountManagementRandomizeName to True. I will provide more detail on creating a randomize local account name at the end of the post.
- Sign in to Intune admin center > Devices > Windows > Configuration > Create > New Policy.
- Platform: Windows 10 and later
- Profile type: Templates.
- Template name: Custom
- Basics tab: Provide a Name and Description of the policy and click Next.
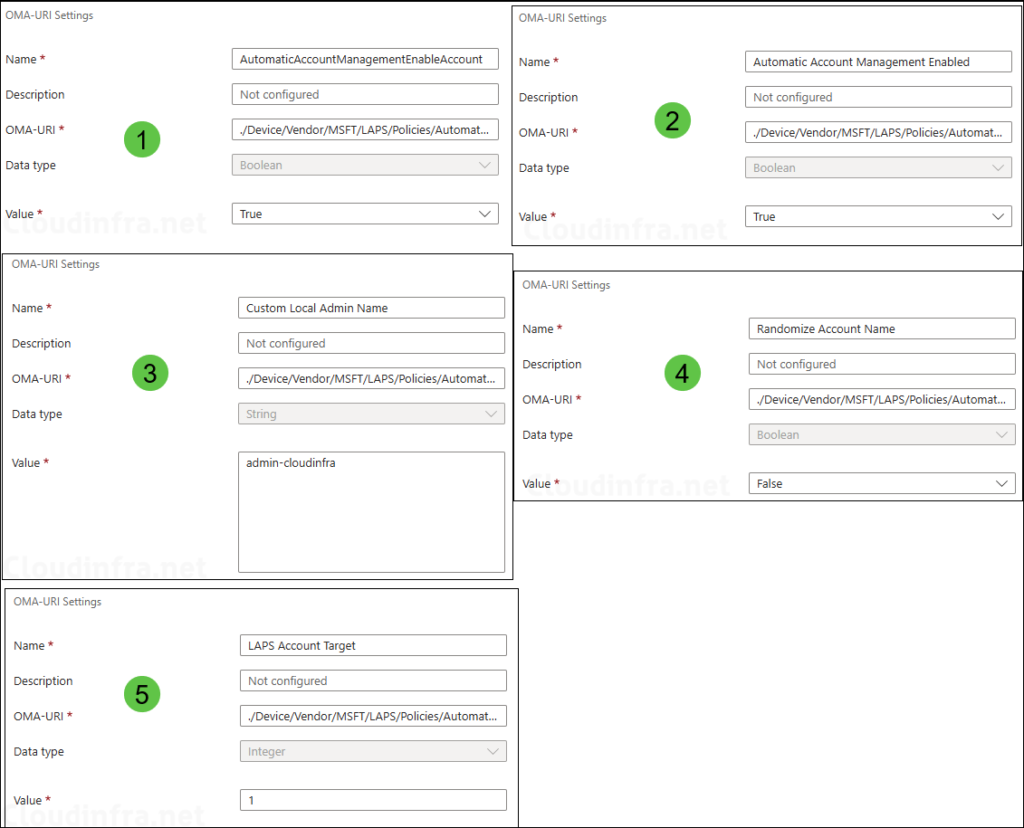
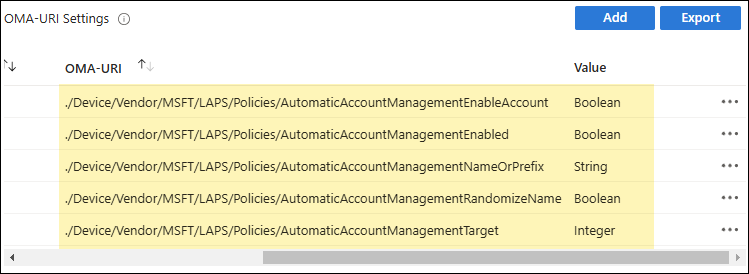
- Configuration settings: Click on Add button to add below OMA-URI Settings:
- OMA-URI Setting:
- Name: AutomaticAccountManagementEnableAccount
- Description: Enable local admin account
- OMA-URI: ./Device/Vendor/MSFT/LAPS/Policies/AutomaticAccountManagementEnableAccount
- Data type: Boolean
- Value: True
- OMA-URI Setting:
- Name: Automatic Account Management Enabled
- Description: Enable account management
- OMA-URI: ./Device/Vendor/MSFT/LAPS/Policies/AutomaticAccountManagementEnabled
- Data type: Boolean
- Value: True
- OMA-URI Setting:
- Name: Custom Local Admin Name
- Description: Provide local admin account name to create or provide a prefix.
- OMA-URI: ./Device/Vendor/MSFT/LAPS/Policies/AutomaticAccountManagementNameOrPrefix
- Data type: String
- Value: admin-cloudinfra
- OMA-URI Setting:
- Name: Randomize Account Name
- Description: For randomizing local account name.
- OMA-URI: ./Device/Vendor/MSFT/LAPS/Policies/AutomaticAccountManagementRandomizeName
- Data type: Boolean
- Value: False
- OMA-URI Setting:
- Name: LAPS Account Target
- Description: Provide which administrator account to manage, Custom or built-in.
- OMA-URI: ./Device/Vendor/MSFT/LAPS/Policies/AutomaticAccountManagementTarget
- Data type: Integer
- Value: 1
- Scope tags (optional): A scope tag in Intune is an RBAC label you add to resources (policies, apps, devices) to limit which admins can see and manage them. For more Information, read: How to use Scope tags in Intune.
- Assignments: Assign the policy to Entra security groups that contain the target users or devices. As a best practice, pilot with a small set first; once validated, roll it out more broadly. For guidance on assignment strategy, see Intune assignments: User groups vs. Device groups.
- Applicability Rules: Specify how to apply this profile within an assigned group. Intune will only apply the profile to devices that meet the combined criteria of these rules.
- Review + create: Review the policy summary and click Create.
Monitoring Automatic Account Management Intune Policy
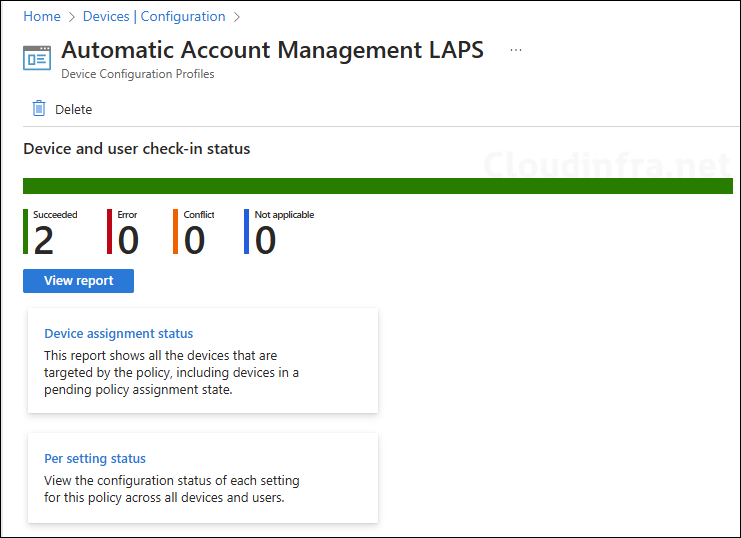
- Sign in to the Microsoft Intune admin center > Click on Devices > Windows > Configuration
- Choose the Device Configuration profile you want to work with, and at the top of the page, you’ll see a quick view of the Success, Failure, Conflict, Not Applicable, and In Progress status.
- Click on View report to access more detailed information.
Sync Intune Policies
The device check-in process might not begin immediately. If you’re testing this policy on a test device, you can manually kickstart Intune sync from the device itself or remotely through the Intune admin center.
Alternatively, you can use PowerShell to force the Intune sync on Windows devices. Another way to trigger the Intune device check-in process is by restarting the device.
End User Experience
After the device configuration profile has been applied successfully, check and confirm if the specified local administrator account has been created successfully.
- Press Win + R to open the Run dialog box.
- Type compmgmt.msc and press Enter to open the Computer management.
- Navigate to Local users and Groups > Users and check if the account has been created.
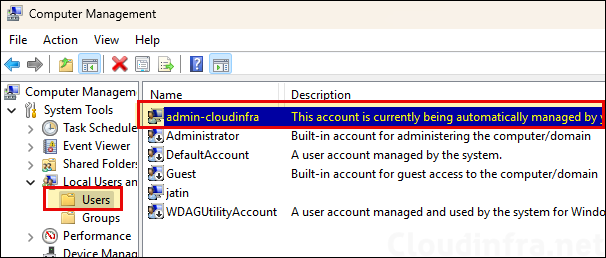
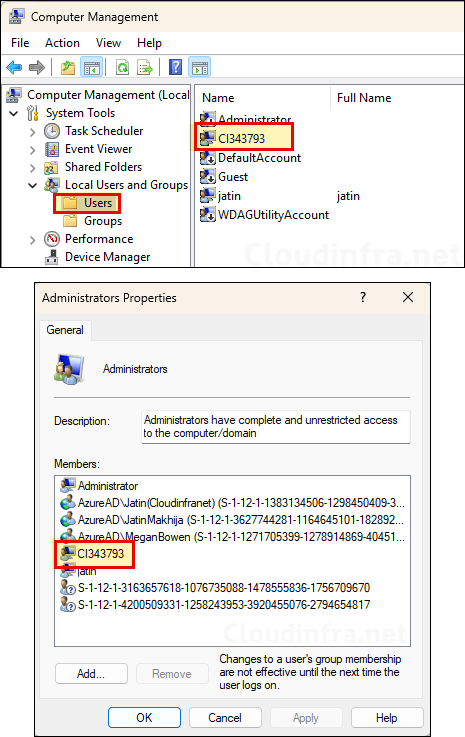
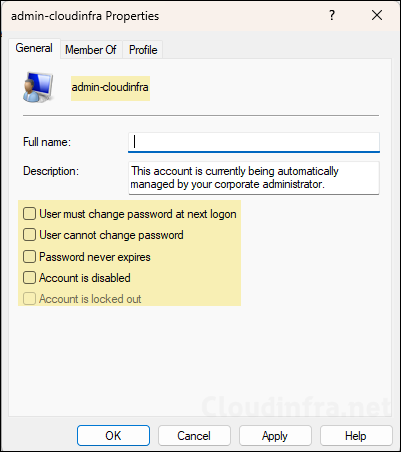
- If you read the description of the account, it clearly states that it’s being automatically managed by your corporate administrator. This also confirms that it’s a Windows LAPS managed account. Let’s look at the properties of admin-cloudinfra account created by Intune. All the default settings are unchecked like User must change password at next logon, User cannot change password etc.
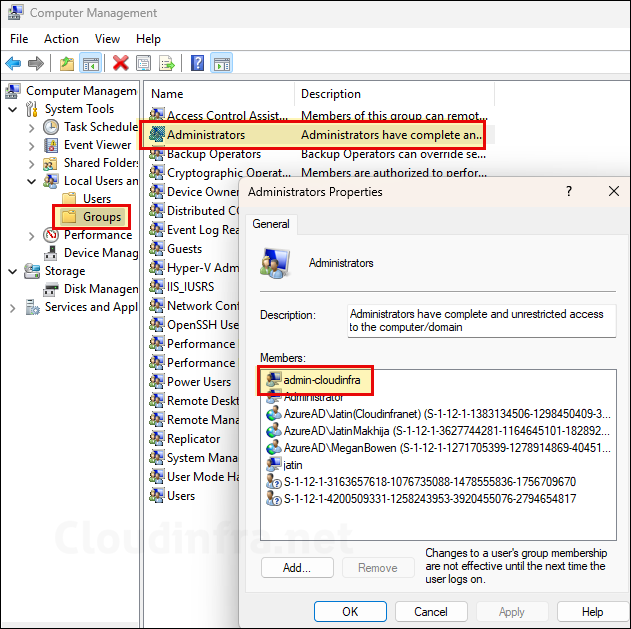
- Go to the Groups folder and check if this account is a member of Administrators group. admin-cloudinfra account is in the Administrator’s group, which confirms that the Intune policy has been applied successfully.
Configure Windows LAPS Policy
Now that the Automatic account management is all set and configured. We have also confirmed that the local admin account is created on the device. We can proceed to create and configure Windows LAPS Policy. I will not go into the details of the policy as I have already written a detailed blog on Windows LAPS setup which you can refer to. However, I will provide how it works in relation to Automatic account management.
To create a Windows LAPS Policy: Sign in to the Intune admin center > Endpoint Security > Account Protection > Click on + Create Policy >Select Platform as Windows 10 and Later > Select Profile as the Local admin password solution (Windows LAPS) > Click on Create.
Ensure that the Administrator Account Name is set to Not Configured, as we have already created and managing it using Automatic account management. When you create Automatic account management policies, Windows LAPS policy will pick up the settings and work with Automatic account management to manage the account created using Automatic account management policies.
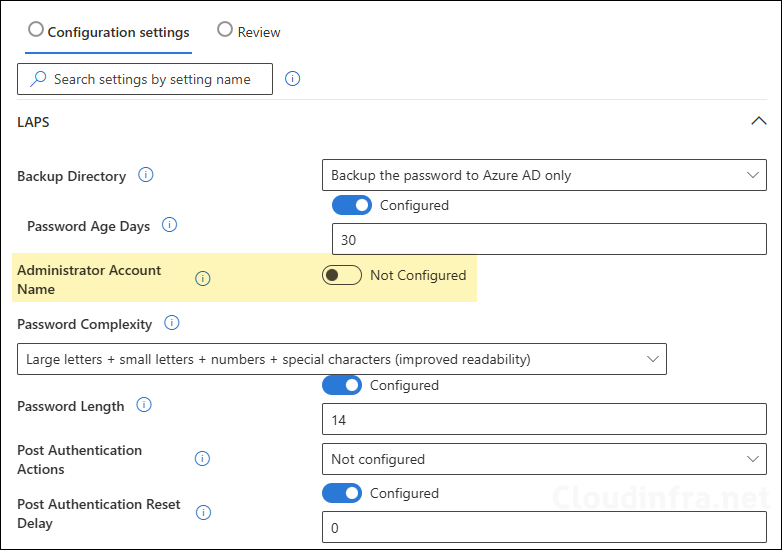
As we have selected the Backup Directory in the LAPS policy to back up the password to Azure AD only. The password would be stored with the Device object in Entra ID. Let’s check the steps to retrieve local admin password.
- Sign in to the Intune admin center > Devices > All devices.
- Click on the device that is targeted by the Windows LAPS policy.
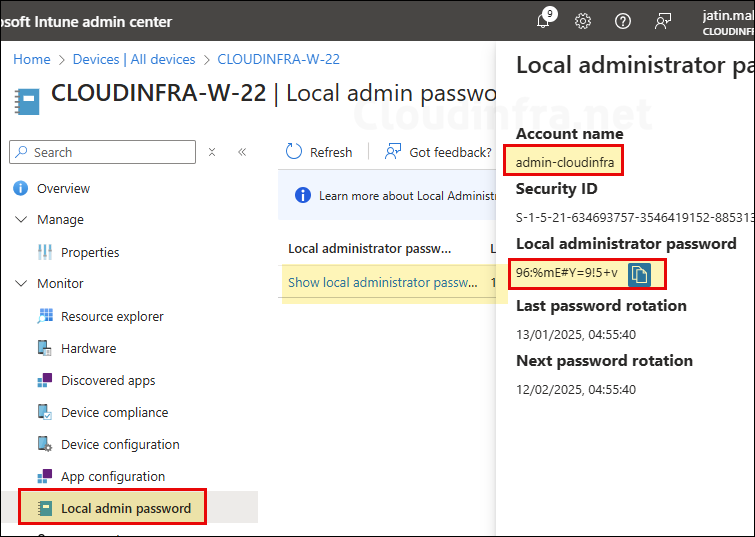
- On the left-hand side, under Monitor, find the Local admin password option.
- Then click on Show local administrator password.
When I Set AutomaticAccountManagementRandomizeName to True
I believe it would be more secure if we randomize local admin account name instead of keeping the same name of the local admin account on all Intune-managed Windows devices. Therefore, I want to show you what will happen when I set AutomaticAccountManagementRandomizeName to True.
I have made below two changes in my existing Automatic account management Windows LAPS policy:
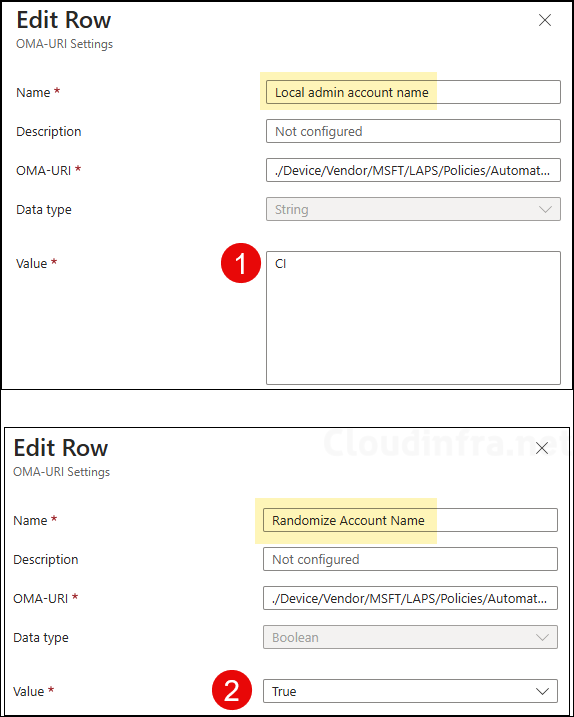
- Set OMA-URI setting ./Device/Vendor/MSFT/LAPS/Policies/AutomaticAccountManagementRandomizeName to true.
- Set OMA-URI setting ./Device/Vendor/MSFT/LAPS/Policies/AutomaticAccountManagementNameOrPrefix and provide the prefix of the randomly created account. As an example, I have provided the prefix as CI.
Let’s see what happens when this updated LAPS policy is applied on the target devices. If we recall, we have not randomized the local admin account name earlier and created admin-cloudinfra local admin account. After this updated policy is applied on the devices, it will delete admin-cloudinfra local admin account and create a new local admin account with the prefix specified in the policy appended with random numerix numbers.
Below is a screenshot of the same device where admin-cloudinfra local admin account was created by automatic account management LAPS policies. Now we don’t see that account in the list as it has been removed when we updated the policies. You will also find that the account name has been created with prefix CI<random numeric numbers>, e.g., CI343793 and its also added to Administrators group.