In this blog post, I will show you the steps to block emails based on file attachment extension in Office 365. Let’s check the background of why you may want to block such emails and then we will explore the steps to create rules in exchange online for this.
Background
Recently, it has been discovered that Microsoft OneNote files (.one) are being used to distribute malware via email. The malware in these files includes Redline, Qbot, Shindig, and other types.
Microsoft OneNote is a digital note-taking application that comes bundled with Microsoft 365. When you install Microsoft 365 on your device, OneNote is typically included.
OneNote itself is not a malicious program or application. However, there have been reports of .one file extensions being exploited to distribute malware, potentially leading to data theft from your computer.
Users may receive phishing emails that contain Microsoft OneNote file attachments. When users open such a file, they are given a button that says Double Click to View File.
Certain batch script files are executed in the background when users click this button. According to Rapid 7’s analysis, the malware can steal various data types, including cryptocurrency wallet credentials, Discord data, and web browser data, including cached cookies.
Hence, it is strongly recommended that you implement measures to block emails containing file attachments with the .one extension. This blog post will explore various methods to safeguard your organization against this threat, including blocking emails with potentially harmful file attachments.
If you wish to search for all emails that users have received with file attachments having the .one extension or any other file attachment, you can refer to the blog post titled Audit report of emails with Specific File attachment Extension In Microsoft 365. This post offers detailed, step-by-step instructions on conducting the search and exporting the emails, either in a CSV file or PST format.
Contents
Block emails with .One File attachment extension
We will explore how to block emails with .one file attachments, whether they are sent or received (inbound or outbound). These steps can also be applied to block other types of file attachment extensions.
Option 1 – Create a Rule in Exchange Online
We will create a rule in Exchange Online to prevent emails with .one file attachments from being sent or received. Here are the steps to accomplish this:
- Sign in to the Exchange Admin Center using your Global Administrator or Exchange Administrator role.
- Go to Mail Flow and then Click on Rules.
- Click on +Add a rule > Create a new rule.
- Rule conditions:
- Name: Block Emails with .One File Attachment Extension
- Apply this rule if: Any attachment and File extension include these words.
- Specify words or phrases: one [without the dot]
- Do the following: Block the message and reject the message and include an explanation.
- Specify rejection reason: This email is rejected due to Invalid File Extension Type.
- Click on Next to proceed.
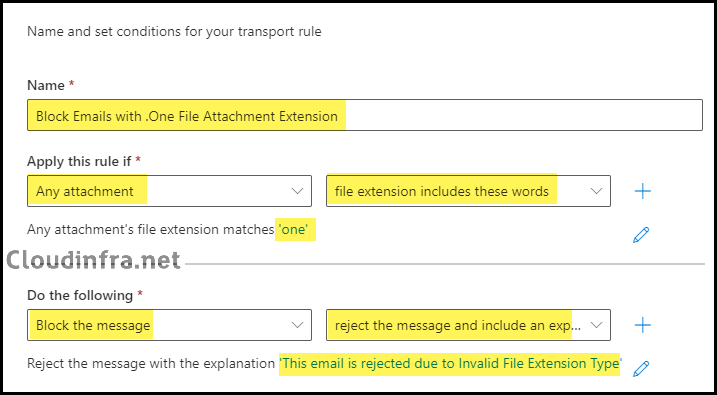
- Rule settings:
- Rule Mode: Enforce
- Keep the rest of the settings to default.
- Click on Next to Proceed.
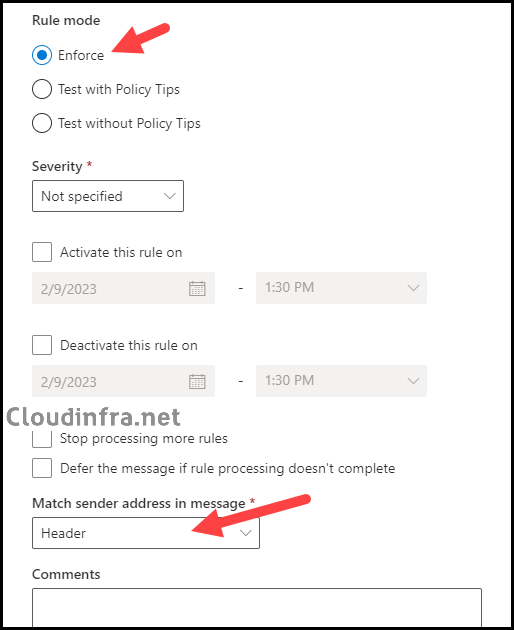
- Review and finish: Review the rule conditions and settings you’ve configured. Once satisfied, click Finish to create this rule. Please be aware that the rule is initially created in a disabled state, so you must enable it after it’s been created.
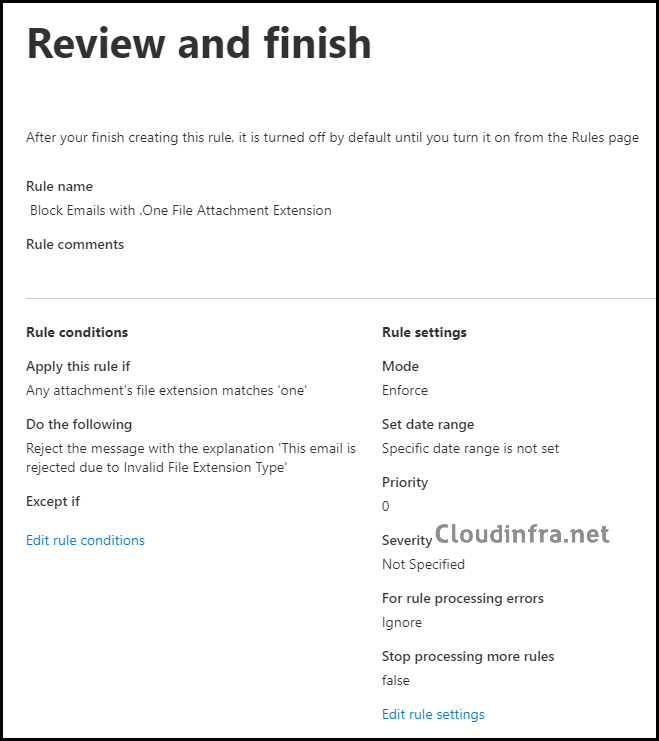
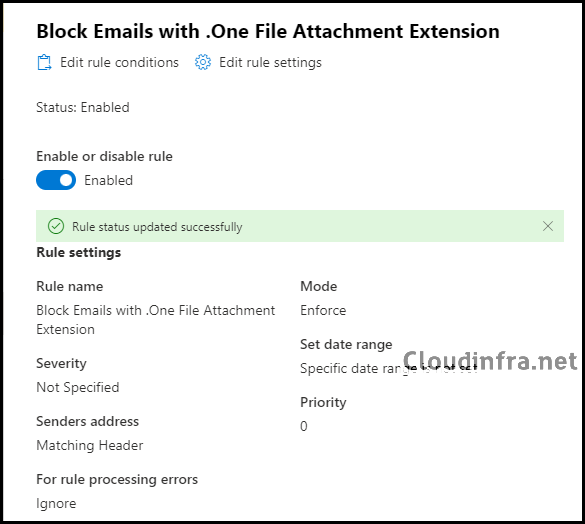
The rule has been created, but as previously mentioned, it is initially disabled. This means it will not be active or impact any users. To make it effective, the rule needs to be enabled.
You can activate the rule by clicking on it and switching the toggle to the “Enable” position.
Option 2 – Block Emails with .One File Attachments using Anti-Malware Policies
In the earlier section, we set up a rule in Exchange Online to block emails containing .one file attachments. Another approach to rejecting such emails is to create an anti-malware policy.
You can create a new anti-malware policy specifically for blocking .one file extensions or modify the existing default anti-malware policy to include this block. Here, we’ll create a new custom anti-malware policy for blocking .one file extensions.
When configuring the anti-malware policy, you have two actions you can choose from for emails with the .one file extension. You can either Reject the message and send a non-delivery receipt (NDR) to the sender or quarantine the message using the attachment filter.
Let’s check the steps:
- Sign in to the Microsoft 365 Defender portal as a Security Administrator or Global Administrator.
- Go to Email and collaboration > Policies & Rules > Threat Policies.
- Under Policies > Find Anti-malware.
- Click on + Create.
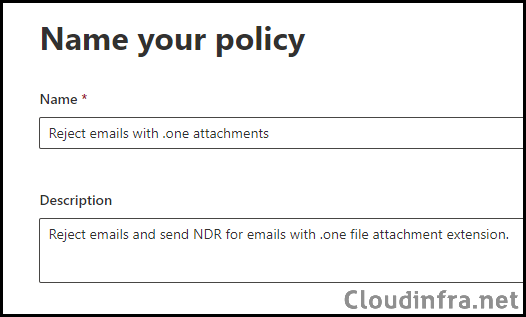
- Name your policy:
- Name: Reject emails with .one attachments
- Description: Reject emails and send NDR for emails with .one file attachment extension.
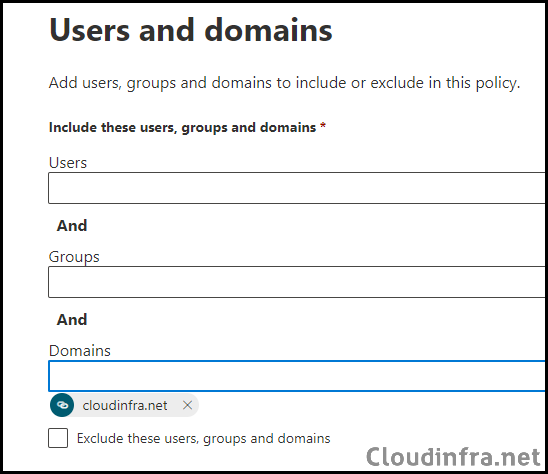
- Users and domains: Add the User, Group, or Domain to which you want to apply this policy. If you add a User, Group, and Domain together, all conditions must match for the rule to take effect.
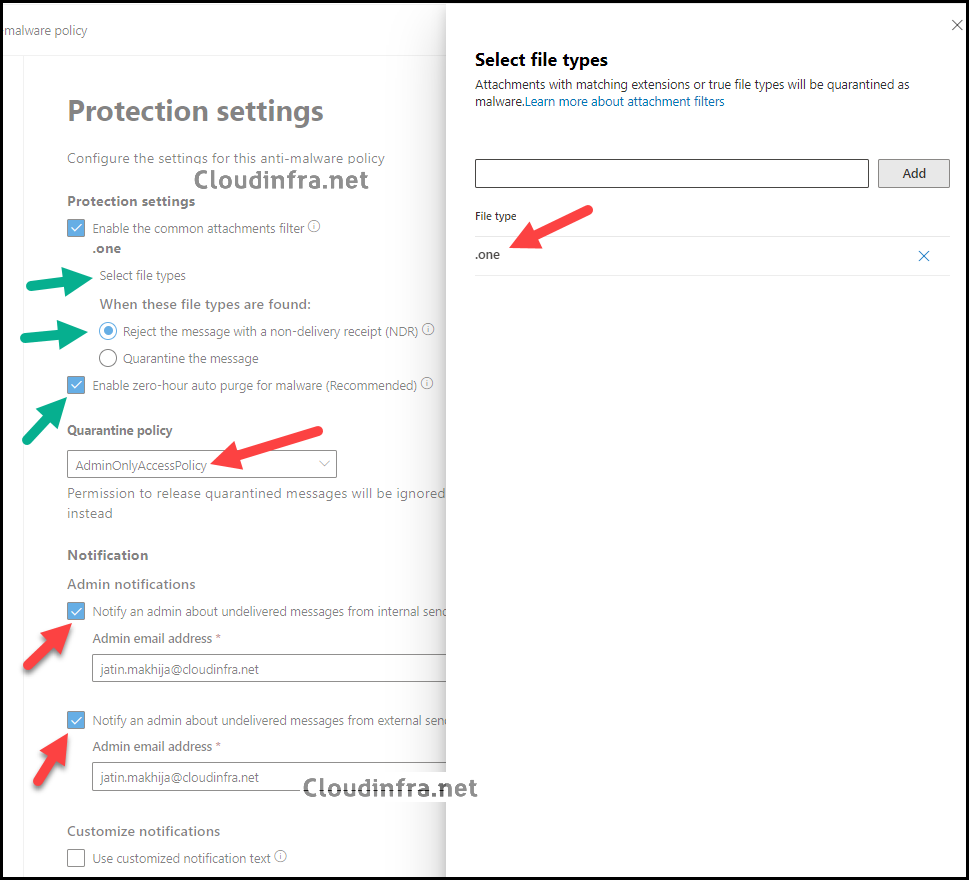
- Protection Settings: Configure Protection settings as per below:
- Click on Select file types and add the .one file type to the list of extensions. Click the X icon next to all other file types to remove them.
- When these file types are found: Select Reject the message with a non-delivery receipt (NDR). (An NDR email will be sent to the sender. The message will not be quarantined, and no recipient or admin notifications will be sent).
- Enable ZAP (Zero-hour auto purge) – Malware ZAP quarantines messages that are found to contain malware after they have been delivered to Exchange Online mailboxes.
- Quarantine Policy – You can select AdminOnlyAccessPolicy to prevent the user from viewing or releasing the messages.
- Notification – Include admin email addresses for Internal and External senders for undelivered emails.
- Click on Submit.
Testing of Exchange Online Rule
We’ve created a rule to block all emails with file attachments having the .one extension. To verify this, follow these testing steps:
- Send a test email with a .one file attachment from an external domain to your organization’s internal domain. [Inbound]
- Send a test email with a .one file attachment from your organization’s internal domain to any external domain. [Outbound]
- Send one test email with .one file attachment from an Internal domain to an Internal domain.
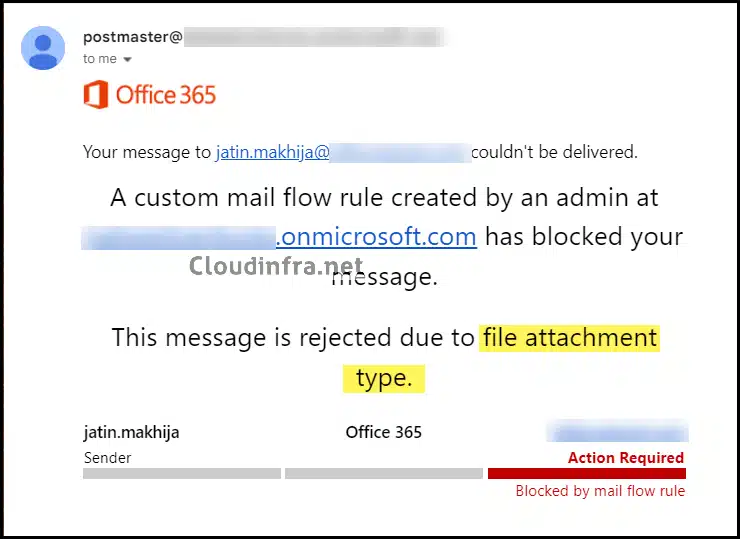
Anyone attempting to send an email with a .one file attachment will receive a bounce-back email with the following message.
“Your message to xxx@cloudinfra.net couldn’t be delivered. A custom mail flow rule created by an admin at xxx.onmicrosoft.com has blocked your message. This message is rejected due to file attachment type.
FAQs
1. How to block other dangerous File Extension types using exchange online
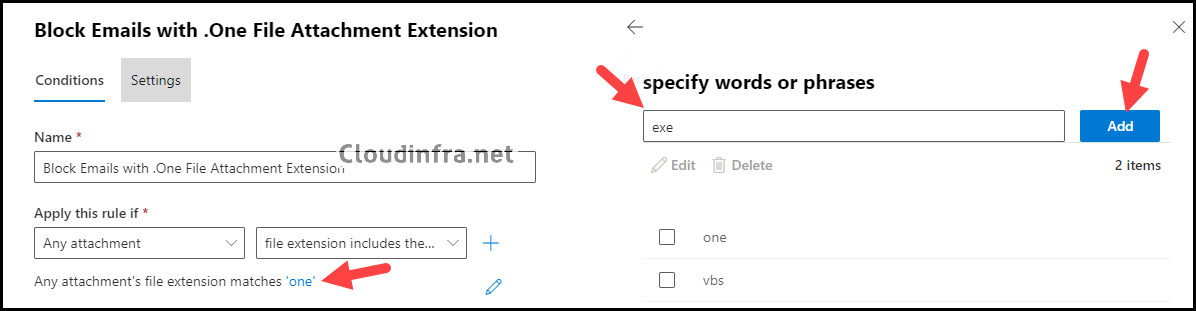
Add extensions to the rule we created to block .one file attachments to enhance your security further.
Go to the Exchange admin center, navigate Mail Flow and Rules, click on the existing rule for .one file attachments, and edit the conditions. Then, under Extensions, add any additional extensions to the list.
2. I am getting below Error message when creating Exchange rule
Failed to create the new transport rule
Error:
Error executing cmdlet: |Microsoft.Exchange.Data.DataValidationException|Name: The property “Name” with value ” Block Emails with .One File Attachment Extension” is invalid. The value can’t contain leading or trailing whitespace. Exception of type ‘Microsoft.Exchange.Management.PSDirectInvoke.DirectInvokeCmdletExecutionException’ was thrown.
Solution:
- Ensure the rule’s name does not contain spaces before or after it. You can go back and update the name to remove the extra spaces.
- Make sure the Extension specified does not have dot (.) in the name – If you include a dot (.) when adding an extension name, such as .one, you might encounter an error that advises you to exclude the dot from the extension name. To create a rule successfully, use words or extensions without a dot.
3. What’s the default anti-malware policy in Microsoft 365? Can it be deleted?
The built-in anti-malware policy in Microsoft 365 is called Default. It holds the lowest priority and is automatically applied to all recipients within your organization. The priority of the default policy remains fixed, and administrators can view, edit, and configure it to align with their organizational requirements. However, it cannot be deleted.
4. How do you manage anti-malware policies using Powershell?
To manage anti-malware policies using PowerShell, follow these steps:
- Install Exchange Online Powershell module using Install-module ExchangeOnlineManagement command.
- Connect to Exchange Online using
Connect-ExchangeOnline. - Use
Get-MalwareFilterPolicyorGet-MalwarefilterRuleto fetch the existing policy settings.
Creating anti-malware policies using PowerShell is a two-step process. First, you need to create a Malware filter policy. Then, you create a Malware filter rule that specifies which Malware filter policy is applied to the rule.
New-MalwareFilterPolicy– Use this cmdlet to create a malware filter policy.New-MalwareFilterRule– Use this cmdlet to create a malware filter rule.
Modify existing Malware filter Policy
Set-MalwareFilterPolicy– Use this cmdlet to modify malware filter policies.Set-MalwareFilterRule– Use this cmdlet to modify malware filter rules.
Conclusion
In this blog post, we’ve learned how to block emails with file attachments using the .one extension. You can also add extensions to the block list to prevent other dangerous extension types .exe or .vbs. You can find the list of dangerous extensions in the Default anti-malware policy on the Microsoft Defender portal.
There is a default anti-malware policy that quarantines any message with the below dangerous extensions:
ace, apk, app, appx, ani, arj, bat, cab, cmd,com, deb, dex, dll, docm, elf, exe, hta, img, iso, jar, jnlp, kext, lha, lib, library, lnk, lzh, macho, msc, msi, msix, msp, mst, pif, ppa, ppam, reg, rev, scf, scr, sct, sys, uif, vb, vbe, vbs, vxd, wsc, wsf, wsh, xll, xz, zOther pre-defined file types can be added to the anti-malware policy:
7z, 7zip, a, accdb, accde, action, ade, adp, appxbundle, asf, asp, aspx, avi, bin, bundle, bz, bz2, bzip2, cab, caction, cer, chm, command, cpl, crt, csh, css, der, dgz, dmg, doc, docx, dot, dotm, dtox, dylib, font, gz, gzip, hlp, htm, html, imp, inf, ins, ipa, isp, its, jnlp, js, jse, ksh, lqy, mad, maf, mag, mam, maq, mar, mas, mat, mav, maw, mda, mdb, mde, mdt, mdw, mdz, mht, mhtml, mscompress, msh, msh1, msh1xml, msh2, msh2xml, mshxml, msixbundle, o, obj, odp, ods, odt, one, onenote, ops, package, pages, pbix, pdb, pdf, php, pkg, plugin, pps, ppsm, ppsx, ppt, pptm, pptx, prf, prg, ps1, ps1xml, ps2, ps2xml, psc1, psc2, pst, pub, py, rar, rpm, rtf, scpt, service, sh, shb, shtm, shx, so, tar, tarz, terminal, tgz, tool, url, vhd, vsd, vsdm, vsdx, vsmacros, vss, vssx, vst, vstm, vstx, vsw, workflow, ws, xhtml, xla, xlam, xls, xlsb, xlsm, xlsx, xlt, xltm, xltx, zi, zip, zipx.
The mail flow rules doesn’t seem to work. Had an email with a .htm attachment come through?
Make sure you do not have a dot in the name while creating a rule. Any attachment file Extension matches “htm”