In this blog post, we will explore the steps to create a local admin using Intune and PowerShell. It will be completed in two steps. First step will be to create a local user account using a PowerShell script and then we will use an Account protection policy in Intune to add the account to local administrator’s group on Windows 10/11 devices.
When we create a local user account using PowerShell, you have the option to leave the password blank if needed. However, you can provide the password which you want to set for the local user in the script.
We will be using Intune device remediation for this task, which requires a detection script and a remediation script. I have created and tested both the scripts and provided the steps in the following sections of the blog post. Let’s take a look:
Step-by-step guide
| Delete a local user account using Intune |
|---|
| If you’re interested in learning how to delete a local user account using Intune, you can refer to my other blog post: How To Delete A Local User Account Using Intune |
If you are using Windows LAPS, you can use Automatic account management Policy CSP settings to create and manage the local administrator account with Windows LAPS. For detailed information about this, refer to the post: Automatic Account Management in Windows LAPS.
Note
Contents
Step 1: Create a Script Package
To create a script package, follow the below steps:
- Sign in to the Intune admin center > Devices > Scripts and remediations.
- Click on + Create under the Remediations tab.
- Basics: Provide a Name, Description, and Publisher Information. For example:
- Settings: Create a detection script using the PowerShell code below. Save it as DetectLocaluser.ps1.
DetectLocaluser.ps1
$userName = "cloudinfra101"
$Userexist = (Get-LocalUser).Name -Contains $userName
if ($userexist) {
Write-Host "$userName exist"
Exit 0
}
Else {
Write-Host "$userName does not Exists"
Exit 1
}
- Create a remediation script using the PowerShell code below. Save it as RemediateLocalUser.ps1.
RemediateLocalUser.ps1
$userName = "cloudinfra101"
$userexist = (Get-LocalUser).Name -Contains $userName
if($userexist -eq $false) {
try{
New-LocalUser -Name $username -Description "Cloudinfra101 local user account" -NoPassword
Exit 0
}
Catch {
Write-error $_
Exit 1
}
}
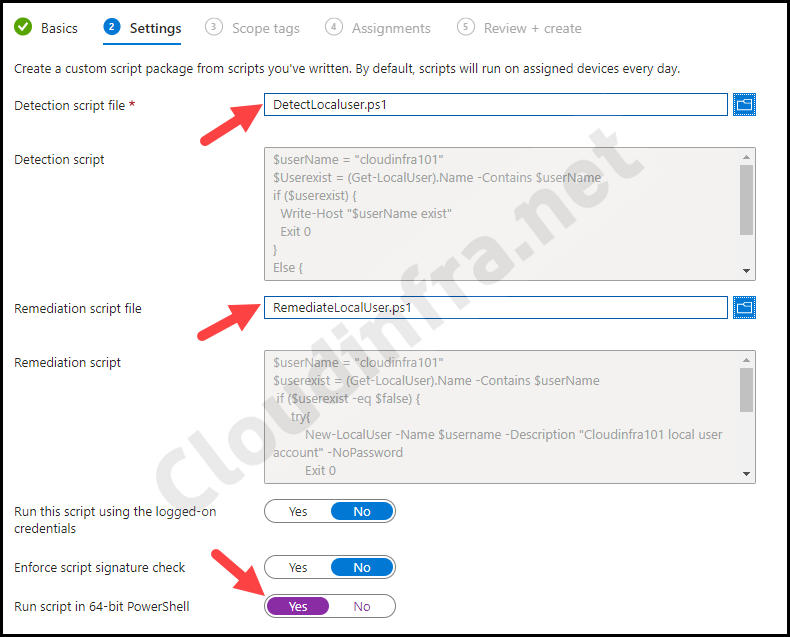
- Detection script file: Browse to the Detection script Detectlocaluser.ps1
- Remediation script file: Browse to Remediation script file RemediateLocalUser.ps1
- Run this script using the logged-on credentials: No
- Enforce script signature check: No
- Run script in 64-bit Powershell: Yes
- Scope tags (optional): A scope tag in Intune is an RBAC label you add to resources (policies, apps, devices) to limit which admins can see and manage them. For more Information, read: How to use Scope tags in Intune.
- Assignments: Assign the policy to Entra security groups that contain the target users or devices. As a best practice, pilot with a small set first; once validated, roll it out more broadly. For guidance on assignment strategy, see Intune assignments: User groups vs. Device groups.
- Review + create: Review the deployment summary and click Create.
Step 2: Add Local User account to the Administrators group
Let’s add the local user account created in the previous step to local administrator group:
- Sign in to the Intune admin center > Endpoint Security > Account Protection.
- Click on + Create Policy.
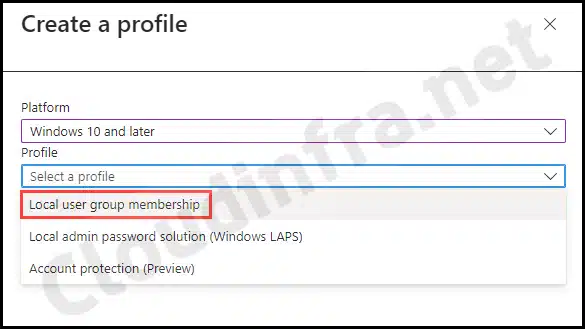
- Select Platform as Windows 10 and Later.
- Select Profile as a Local user group membership.
- Click on Create.
- Basics: Provide a Name and Description of the profile.
- Configuration settings:
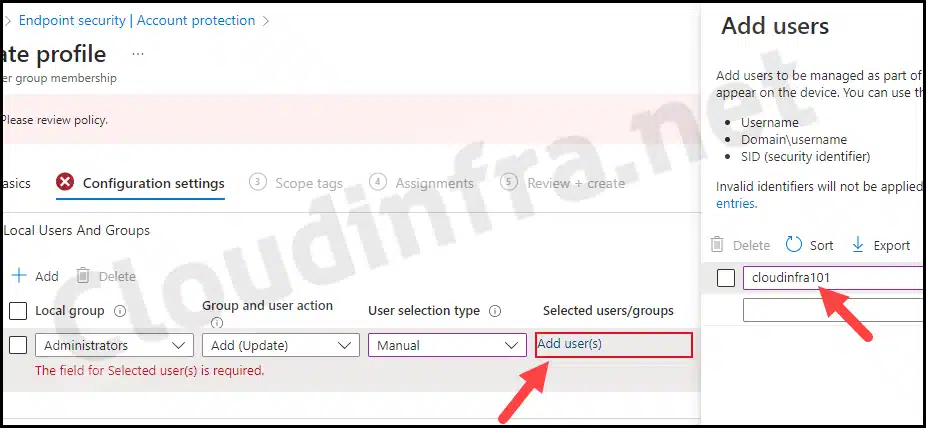
- Local group: Administrators
- Group and user action: Add (Update)
- User selection type: Manual
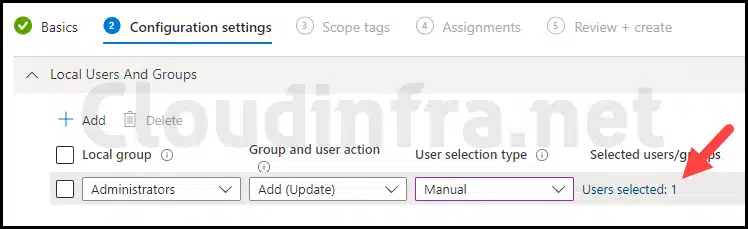
- Selected Users/groups: Click the Add user(s) link and provide the cloudinfra101 local user account name.
We have provided cloudinfra101 to be added to local administrator group. You can add multiple local users into local Administrators group as well. Ensure that the local user account exists on the device and is a valid name. If a local user account name is invalid, it will simply be ignored.
Note
- Assignments: Click Add groups and select the Entra security group containing Windows 10/11 devices.
- Review + Create: Review the policy once and then click on Create.
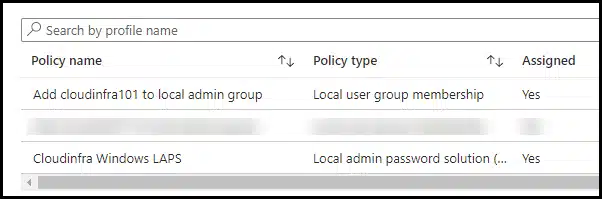
Sync Intune Policies
The device check-in process might not begin immediately. If you’re testing this policy on a test device, you can manually kickstart Intune sync from the device itself or remotely through the Intune admin center.
Alternatively, you can use PowerShell to force the Intune sync on Windows devices. Restarting the device is another way to trigger the Intune device check-in process.
End User Experience
Now, let’s look at the policy’s results after it has been applied successfully.
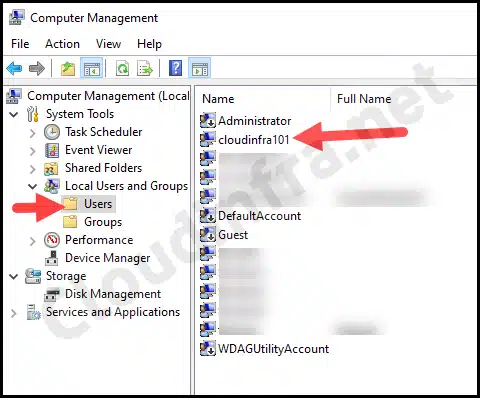
- Click on Start > search for Computer Management
- Then go to Local Users and Groups > Users
- Check if the cloudinfra101 local user account has been created
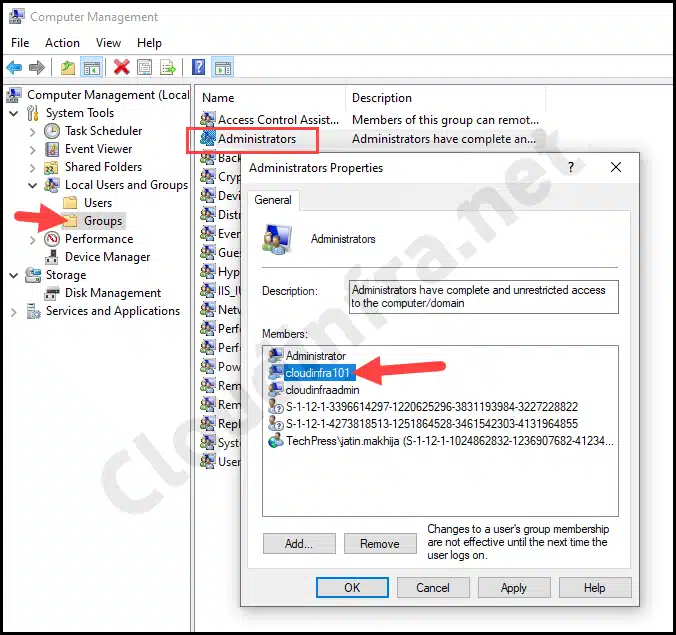
- Go to the Groups folder and double-click on the Administrators group to check if the cloudinfra101 local user account has been added.
Conclusion
We have created a local user account using Intune device remediation and added it to the local Administrators group using an Account protection policy. This approach is different from using OMA-URI approach we followed in the previous blog post: Create local admin using OMA-URI method.

What is the syntax for modifying this to add the password?
I have not defined any password for the local user also as I have used -Nopassword parameter with New-LocalUser cmdlet. You can modify the script to add password for the local user account if you want.
Hi RW, To add the password. You can use below code:
$Password = provide password here
$params = @{
Name = ‘User03’
Password = $Password
FullName = ‘Third User’
Description = ‘Description of this account.’
}
New-LocalUser @params
You can use this blog post as well if you want to create a local user account with password using intune: https://cloudinfra.net/how-to-create-a-local-admin-account-using-intune/
For more info, please refer to: https://learn.microsoft.com/en-us/powershell/module/microsoft.powershell.localaccounts/new-localuser?view=powershell-5.1
I have tried to use this script for an Intune LAPS rollout, the account is created and Inune’s LAPS provides the password however on logon the profile failed on creation with the following event, “User profile cannot be loaded with Event ID 1509”.
Manually creating an account allowing LAPs to replace the password works fine,
Any Ideas?
We’ve noticed that the local user account will not be added to a computer unless there is nobody is logged in. Is this normal behavior? Is there a workaround for it?
Hello Jatin,
I’ve noticed on several devices that the add user remediation doesn’t appear to work when any user is logged in at the time the script is executed. Is that normal behavior? If not, is there a workaround for it?
Thank you for this great article, it has been of great help to me. A question:
To this type of users, created locally with Intune,
Is it possible to block the user from changing their password?
Thanks in advance.
Hey Jesus, Thank you for the feedback. You can use the “User cannot change password” flag for your requirements. I don’t have a script ready for this, but there is a similar script that modifies the “User must Change password at next logon” flag.
You could use that script and modify it to target the “User cannot change password” flag. Here’s the link: https://cloudinfra.net/enable-disable-user-must-change-password-at-next-logon-using-intune/
This script is not safe enough in corporate environment if you are using this for creation of local admin accounts before the LAPS kicks in – empty password is the risk. If there is a problem with the LAPS process that should kick in later, you will have an organization of people walking around the world with empty admin passwords.
For this occasion i suggest you use:
function Get-RandomPassword {
param (
[Parameter(Mandatory)]
[int] $length,
[int] $amountOfNonAlphanumeric = 1
)
Add-Type -AssemblyName ‘System.Web’
return [System.Web.Security.Membership]::GeneratePassword($length, $amountOfNonAlphanumeric)
}
$userName = “lapsadmin”
$userexist = (Get-LocalUser).Name -Contains $userName
$password = Get-RandomPassword -Length 30
if($userexist -eq $false) {
try{
New-LocalUser -Name $username -Description “LAPS backup admin account” -Password $password
Exit 0
}
Catch {
Write-error $_
Exit 1
}
}
Hi Marek, I’m trying to baked this with autopilot and deploying LAPS at pre provisioning phase, do you think it will work with that script? your script will create an account called lapsadmin with the random password and then enabled that account so LAPS can change and manage the password correct?
Use the script above but with :
$password = Get-RandomPassword -Length 30 | ConvertTo-SecureString -AsPlainText -Force