In this blog post, I will show you the steps to create HKCU registry keys using Intune remediations. Please note that Intune remediations requires Windows 10/11 Enterprise license. For more information, please refer to the prerequisites section.
In my previous blog post, we have learnt the steps to create registry keys and values using Win32 app method and also using Intune remediations method. Both these methods demonstrate creation of registry key and values in HKLM registry node.
If you prefer to use Win32 app method to deploy registry key and values in HKCU node, you can use this link. You will need to export the registry keys and values from HKCU node and while creating deployment, select Install behavior as User to deploy the scripts under user context.
Deployment of reg keys and values using Win32 app method
HKCU is a short form of HKEY_CURRENT_USER. It contains the configuration information for the user currently logged on. The user’s folders, screen colors and Control Panel settings are stored here, and this information is associated with the user’s profile.
About HKCU registry node
If you need to back up and remove a registry key, refer to my other blog post, which offers guidance on addressing the CVE-2022-30190 vulnerability. It also outlines the steps for backing up and deleting a registry key using Intune. It utilizes the PowerShell script deployment method.
Want to backup and delete a registry key?
Contents
Prerequisites
- Device must be Microsoft Entra joined or Entra Hybrid joined.
- Device must be enrolled and managed by Intune.
- Supported Windows operating systems are: Enterprise, Professional, or Education edition of Windows 10 or later.
- Windows 10/11 Enterprise E3 or E5 (included in Microsoft 365 F3, E3, or E5).
- Windows 10/11 Education A3 or A5 (included in Microsoft 365 A3 or A5).
- Windows 10/11 Virtual Desktop Access (VDA) per user.
Create a Remediations Script Package
To create a device remediation script package, we will need a detection and a remediation script. I have provided both the scripts code below. However, you can also download the script files from my GitHub repository: Create HKCU Reg Key and Values using Remediation · GitHub.
- Sign in to the Intune admin center > Devices > Scripts and remediatons.
- Click on + Create under the Remediations tab.
- Basics: Provide a Name, Description, and Publisher Information of the remediation script package.
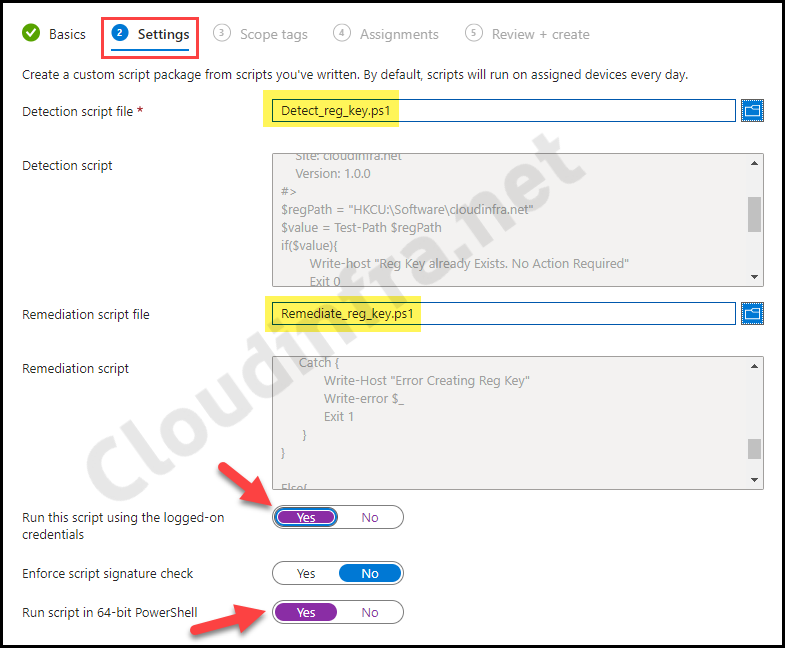
- Settings: Create a detection script using below PowerShell code. Save it as Detect_reg_key.ps1.
You can change the registry path and values in the script according to your requirements. Using this example detection and remediation scripts, I am making sure that cloudinfra.net registry key and entries Location and Status along with the given values and type are always set to values (
$regValues) given in the script.Note
Detect_reg_key.ps1
<#
.DESCRIPTION
Checks the existence of the cloudinfra.net registry key in
HKCU registry node and its values.
Author: Jatin Makhija
Version: 1.0.0
Copyright: Cloudinfra.net
#>
$regPath = "HKCU:\Software\cloudinfra.net"
$regValues = @{
"Location" = @{ Data = "United Kingdom"; Type = "String" }
"Status" = @{ Data = "1"; Type = "Dword" }
}
$typeMap = @{
"String" = [Microsoft.Win32.RegistryValueKind]::String
"DWord" = [Microsoft.Win32.RegistryValueKind]::DWord
"QWord" = [Microsoft.Win32.RegistryValueKind]::QWord
"Binary" = [Microsoft.Win32.RegistryValueKind]::Binary
"MultiString" = [Microsoft.Win32.RegistryValueKind]::MultiString
"ExpandString" = [Microsoft.Win32.RegistryValueKind]::ExpandString
}
if (Test-Path $regPath) {
Write-Host "Registry key exists. Checking values..."
foreach ($key in $regValues.Keys) {
$expected = $regValues[$key]
$actual = Get-ItemProperty -Path $regPath -Name $key -ErrorAction SilentlyContinue
if ($null -eq $actual) {
Write-Host "Registry value '$key' does not exist!"
Exit 1
}
$actualValue = $actual.$key
$actualType = (Get-Item -Path $regPath).GetValueKind($key)
if ($actualType -ne $typeMap[$expected.Type] -or $actualValue -ne $expected.Data) {
Write-Host "Registry value '$key' is of type $actualType, expected $($expected.Type) or value does not match!"
Exit 1
}
}
Write-Host "All registry values match the expected data. No action required."
Exit 0
} else {
Write-Host "Registry key does not exist."
Exit 1
}
- Create a remediation script using below powershell code. Save it as Remediate_reg_key.ps1.
Remediate_reg_key.ps1
# Open Registry session in current user’s drive
New-PSDrive -Name HKU -PSProvider Registry -Root HKEY_USERS -ErrorAction SilentlyContinue | Out-Null
# Get the current user SID
$user = Get-WmiObject -Class Win32_ComputerSystem | Select-Object -ExpandProperty UserName
if (-not $user) { Write-Error "No interactive user detected."; Exit 1 }
$sid = (New-Object System.Security.Principal.NTAccount($user)).Translate([System.Security.Principal.SecurityIdentifier]).Value
# Set the path to the current user's registry location
$regPath = "HKU:\$sid\Software\cloudinfra.net"
# Define expected values and types
$regValues = @{
"Location" = @{ Data = "United Kingdom"; Type = "String" }
"Status" = @{ Data = "1"; Type = "String" } # String on purpose
}
$typeMap = @{
"String" = [Microsoft.Win32.RegistryValueKind]::String
"DWord" = [Microsoft.Win32.RegistryValueKind]::DWord
"QWord" = [Microsoft.Win32.RegistryValueKind]::QWord
"Binary" = [Microsoft.Win32.RegistryValueKind]::Binary
"MultiString" = [Microsoft.Win32.RegistryValueKind]::MultiString
"ExpandString" = [Microsoft.Win32.RegistryValueKind]::ExpandString
}
# Ensure key and values
if (-not (Test-Path $regPath)) {
try {
Write-Host "Creating Reg Key"
New-Item -Path "HKU:\$sid\Software" -Name "cloudinfra.net" -Force | Out-Null
foreach ($key in $regValues.Keys) {
$value = $regValues[$key]
New-ItemProperty -Path $regPath -Name $key -Value $value.Data -PropertyType $value.Type -Force | Out-Null
}
Exit 0
} catch {
Write-Host "Error Creating Reg Key"
Write-Error $_
Exit 1
}
}
else {
Write-Host "Reg Key already exists. Checking values..."
foreach ($key in $regValues.Keys) {
$value = $regValues[$key]
$actual = Get-ItemProperty -Path $regPath -Name $key -ErrorAction SilentlyContinue
if ($null -eq $actual) {
Write-Host "Registry value '$key' does not exist! Creating it..."
New-ItemProperty -Path $regPath -Name $key -Value $value.Data -PropertyType $value.Type -Force | Out-Null
continue
}
$actualValue = $actual.$key
$actualType = (Get-Item -Path $regPath).GetValueKind($key)
if ($actualType -ne $typeMap[$value.Type] -or $actualValue -ne $value.Data) {
Write-Host "Incorrect '$key' value or type. Correcting it..."
Remove-ItemProperty -Path $regPath -Name $key -ErrorAction SilentlyContinue
New-ItemProperty -Path $regPath -Name $key -Value $value.Data -PropertyType $value.Type -Force | Out-Null
}
}
Write-Host "All values are correct or have been remediated. No further action required."
Exit 0
}
- Detection script file – Browse to the Detection script Detect_reg_key.ps1
- Remediation script file – Browse to Remediation script file Remediate_reg_key.ps1
- Run this script using the logged-on credentials – Yes
- Enforce script signature check – No
- Run script in 64-bit Powershell – Yes
- Scope tags (optional): A scope tag in Intune is an RBAC label you add to resources (policies, apps, devices) to limit which admins can see and manage them. For more Information, read: How to use Scope tags in Intune.
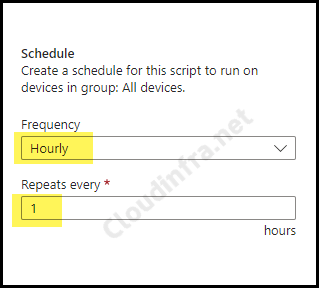
- Assignments: Click on Add group to add an Entra security group containing users or devices. You can also select the Schedule to run this script package. You have three options: Once, hourly, or Daily. For further guidance on assignment strategy, see Intune assignments: User groups vs. Device groups.
- Review + create: Review the deployment and click on Create.
Sync Intune Policies
The device check-in process might not begin immediately. If you’re testing this policy on a test device, you can manually kickstart Intune sync from the device itself or remotely through the Intune admin center.
Alternatively, you can use PowerShell to force the Intune sync on Windows devices. Restarting the device is another way to trigger the Intune device check-in process.
End User Experience
After the script package is deployed on the target device. You can open the registry editor on the device to check and confirm if the registry keys and values are created as per the script.
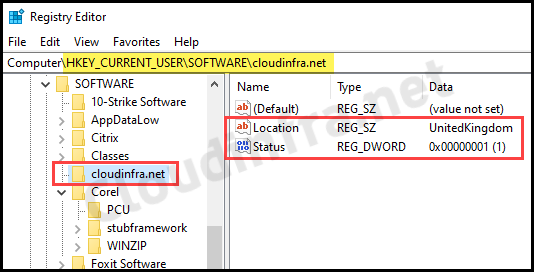
Monitor Intune Device Remediations
- Sign in to the Intune admin center > Devices > Scripts and remediations.
- Click on the Remediation script package you want to monitor: for example, Create Reg Keys in HKCU.
Conclusion
This blog post explored the steps to create registry keys in the HKCU (HKEY_CURRENT_USER) hive using Intune remediations. Intune offers various methods for deploying registry keys and entries. Another approach involves creating and deploying a PowerShell script through the Devices > Scripts and remediations > Platform scripts method.

Good morning!
i copied this to test – word for word and set it as a PS1 file – it came back as “failed”
there is unfortunately no information in there of course. But i ran both sucessfully on my machine, but going into intune did not work
Good morning! I tested the script to ensure it was functioning correctly. I’ll review it again and provide an update.
Hi there, i had repliued but looks like it didn’t go through – it works, but it was due to it being coded as UTF-8 BOF and not just straight UTF-8 (as per their docs)
after i changed it within notepad ++ it worked flawlessly
All fixed – UTC-8 encoding needed – was set to UTC-8 BOF
Awesome! I’m happy to hear that it’s working for you.
Excellent guide, but would the users not need to be local admin on the device to add the key to HKCU?
Good question! 🙂 If I recall correctly, I did not grant admin rights to the user. However, the logic suggests that the user should have edit rights for the registry since the script is running under the logged-on user. I will test it again and confirm this.
@Rikki – This post has been updated to ensure that scripts also work in User context and update the registry keys even if the user does not have administrative rights.
Firstly, thanks for this guide, it’s great and I used it to pushout a couple of fixies.
However, sadly it didn’t when I tried to add new keys under HYCU\SOFTWARE\Policies\ When I check the permissions the users only have read access to the key.
I’ve tried a few work around but so far none have worked yet, if you’ve any thoughts it would be appreciated.
Thank you for the feedback. Someone provided a fix for your issue in the comment section of this blog post: https://cloudinfra.net/how-to-deploy-a-powershell-script-using-intune/#comments. Please check to see if that resolves your issue.
Trying to use this method to set the default font for Outlook. The path is HKCU:\Software\Microsoft\Office\16.0\Common\MailSettings but there are six values to change that are all BINARY.
ComposeFontComplex
ComposeFontSimple
ReplyFontComplex
ReplyFontSimple
TextFontComplex
TextFontSimple
I have them set in my PC I just need to somehow export them in a readable form to put in the script to set them. Any ideas?
I have used the Export method in this blog post. Please refer to it for more Information: https://cloudinfra.net/how-to-create-registry-keys-using-intune-win32-app/.
Alternatively, you can create registry keys and values directly as well via Powershell: https://cloudinfra.net/how-to-create-a-registry-key-and-values-using-powershell/
$value.Data isn’t set anywhere line 37 needs to be inserted with:
$value = $regValues[$key]
@Brian Johnson – Thank you, The issue is rectified in the updated script.