In this post, I will show you the steps to setup Windows LAPS with Intune. Windows Local Administrator Password Solution (Windows LAPS) is a built-in Windows capability that automatically manages the password of a local administrator account and backs it up to either Microsoft Entra ID (cloud) or Windows Server Active Directory (on-prem).
Managing LAPS through Microsoft Intune standardizes password rotation, reduces lateral movement risk, and gives controlled, auditable recovery options for helpdesk and security teams. Intune configures Windows LAPS using the Windows LAPS CSP, which takes precedence over legacy or other policy sources.
A built-in local administrator account exists on every Windows device. Because it holds full administrative privileges and is a well-known, high-value target, you should never keep a shared or rarely changed password. Windows LAPS addresses this risk by ensuring each device uses a unique, regularly rotated local admin password that can be used by authorized admins when needed.
Windows LAPS can manage the built-in Administrator account or a custom local administrator account. Many organizations keep the built-in Administrator account disabled and instead use a dedicated custom admin account for day-to-day operations and break-glass scenarios. With Windows LAPS, you can secure either model by rotating credentials automatically and storing them in a supported directory location.
There is no separate “Windows LAPS license” to purchase. However, you must meet the baseline licensing requirements to deploy and manage the policy with Intune and to use Microsoft Entra as a backup directory. At minimum, Microsoft requires Microsoft Intune Plan 1 and Microsoft Entra ID Free for Windows LAPS with Intune.
If you prefer not to pre-create and maintain a local admin account yourself, Windows LAPS now also supports automatic account management. Starting with Windows 11 24H2, you can enable this mode so Windows LAPS can manage the built-in Administrator account or create and manage a new custom local admin account. On earlier Windows versions, Windows LAPS can only manage accounts that already exist on the device, so account creation must be handled separately.
For macOS, Intune introduced macOS local account configuration with LAPS with Intune service release 2507 (July 2025). This capability is configured within macOS Automated Device Enrollment (ADE) profiles and provisions devices with a local administrator account whose password is stored and rotated by Intune. If you manage Macs, refer to my companion guide, Setup and Configure LAPS for macOS via Intune, for the full step-by-step configuration.
If you plan to use automatic account management, scope that configuration to Windows 11 24H2 (or later) devices only, and use a separate approach to create custom local admin accounts on down-level Windows builds.
Note
Contents
Prerequisites
- Microsoft Intune Plan 1 (or equivalent bundle that includes Intune).
- Microsoft Entra ID Free is sufficient for Windows LAPS features when using Intune
- Microsoft Entra joined or Microsoft Entra hybrid joined devices. Workplace-joined (WPJ / Entra registered) devices are not supported by Intune for LAPS. If your device is only “registered,” you must Entra join or hybrid join it before LAPS via Intune will work.
- If a device is disabled in Microsoft Entra ID, password rotation and backup will not apply.
Starting from April 2023, updates or later, the following operating systems are supported for implementing Windows LAPS. There’s no need for an agent or MSI for LAPS, as it is built into the Windows OS versions listed below with April updates and later.
- Windows 11 22H2 – April 11, 2023 Update
- Windows 11 21H2 – April 11, 2023 Update
- Windows 10 – April 11, 2023 Update
- Windows Server 2022 – April 11, 2023 Update
- Windows Server 2019 – April 11, 2023 Update
Important 2026 note: Windows 10 reached end of support on October 14, 2025. Microsoft allows Windows 10 enrollment in Intune, but LAPS functionality “isn’t guaranteed and can vary” on out-of-support OS versions. If you are standardizing now, prioritize Windows 11.
Design recommendations and best practices
- Manage only one local admin account per device: Windows LAPS can manage only one local admin account per device. If multiple LAPS policies target different accounts, you will create conflicts that must be resolved before the device can be managed.
- Prefer Entra ID backup unless you have a strict requirement for AD backup: If your helpdesk and security operations are cloud-first, Entra backup is usually the best option. Password recovery is available in Entra ID (and shows through Intune for Entra backup scenarios). Entra auditing and access controls are easier to standardize in many tenants. If you must use on-prem AD backup, plan schema updates and OU delegation (covered later).
- Use automatic account management only where it is supported: Automatic account management is supported only on Windows 11 24H2 and later. On earlier versions, specifying an account name that does not exist has no effect and does not generate an error.
Step 1: Enable Windows LAPS in Microsoft Entra ID (tenant-setting)
This step is required for Microsoft Entra joined devices that will back up passwords to Entra ID. (Hybrid join does not require this tenant enablement).
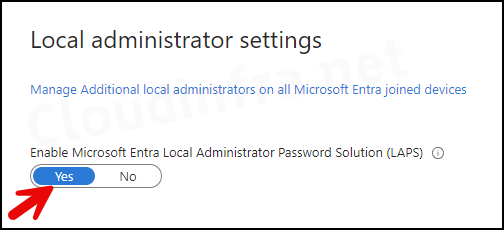
- Sign in to the Entra admin center > Expand Entra ID > Devices > Device Settings.
- Scroll down to find Enable Microsoft Entra Local Administrator Password Solution (LAPS) setting and set it to Yes. Click on Save to save the changes.
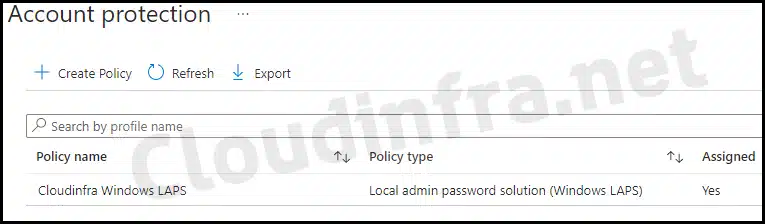
Step 2: Create Windows LAPS policy in Intune
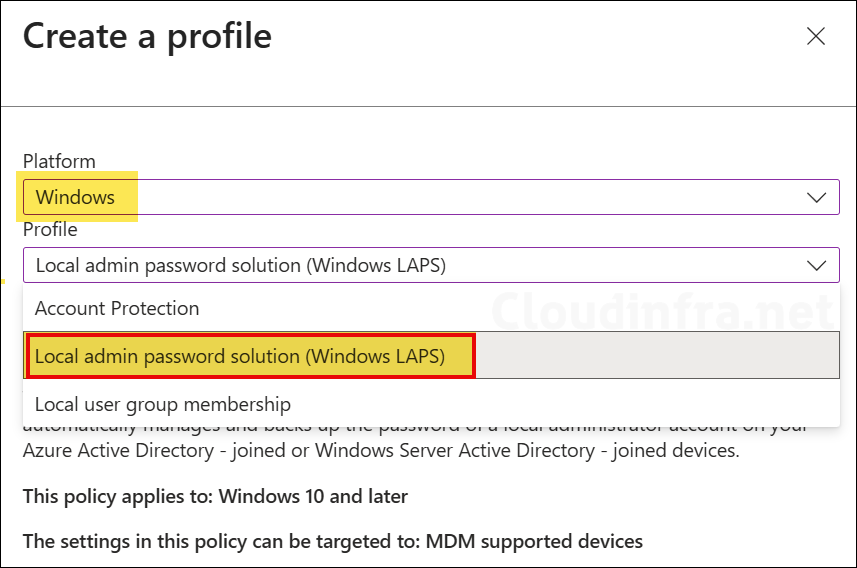
- Sign in to the Intune admin center > Endpoint Security > Account Protection. Click on + Create Policy. Select Platform: Windows. Profile: Local admin password solution (Windows LAPS).
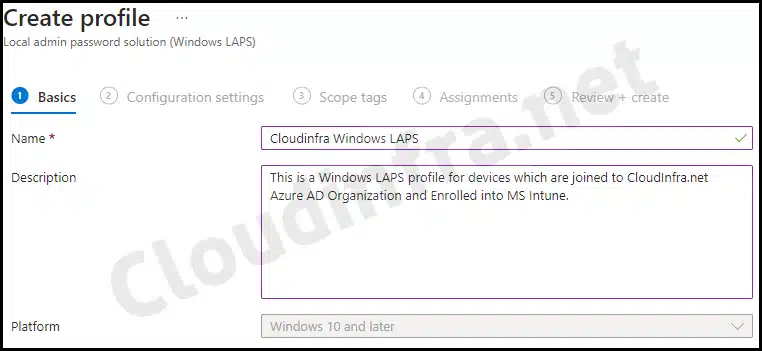
- Basics Tab: Provide a name and description of the policy.
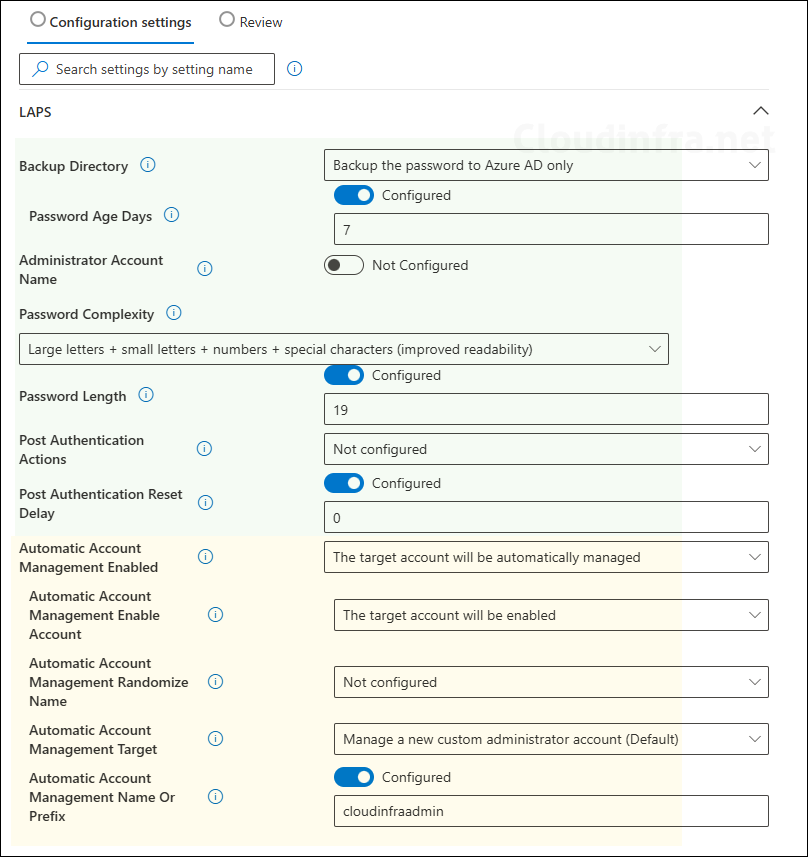
Configuration settings
- Backup Directory: You have four options for this setting. If all devices are Microsoft Entra joined, select Backup the password to Entra ID only. If the devices are Entra hybrid joined, you can choose to store the password in Entra ID or on-premises Active Directory. Select the option that aligns with your environment.
- Disabled (Password will not be backed up) (Default)
- Backup the password to Entra ID only
- Backup the password to the Active Directory only
- Not Configured
- Password Age (Days): This can be set from 1 to 365 days, with a default of 30 days. If you back up the password to Entra ID, the minimum password age is 7 days. For on-premises Active Directory, it can be set as low as 1 day. Choose a balanced value based on how frequently the helpdesk or other teams need access to the passwords, and consult your security team before finalizing this setting. 14 to 30 days is common in enterprise environments.
- Administrator Account Name: This setting specifies which local account LAPS should manage. If you enter a name, LAPS will look for an existing local account with that name and begin rotating its password. If the account does not exist, LAPS will not create it and will fail silently until the account appears.
This setting does not create a local administrator account. If you leave Administrator Account Name set to Not configured, the default built-in Administrator account (identified by RID 500) is used. If you are using Automatic Account Management, keep this setting set to Not configured.
- Password Complexity: The recommended setting is Large letters + small letters + numbers + special characters (improved readability). This option requires Windows 11 24H2 or later.
- Password Length: Password length default is 14, allowed 8 to 64.
- Post Authentication Actions: If you want to automatically rotate the local administrator password after every use, select one of the available options. When enabling this feature, ensure it is used together with Post Authentication Reset Delay to allow sufficient time for helpdesk staff to complete troubleshooting before any post-authentication action is triggered. If this setting is not configured, the default option, Reset password and log off, is applied.
- Reset password: Every time someone authenticates using the local administrator account, the password is reset, and a new password is backed up to Entra ID.
- Reset password and log off: Every time someone authenticates using the local administrator account, the password is reset, a new password is backed up to Entra ID, and the user is logged off to prevent further misuse.
- Reset password and reboot: Every time someone authenticates using the local administrator account, the password is reset, a new password is backed up to Entra ID, and the device is rebooted to prevent further misuse.
- Reset the password, log off the managed account, and terminate any remaining processes.
| Post Authentication Actions |
|---|
| Not Configured |
| Reset password: upon expiry of the grace period, the managed account password will be reset. |
| Reset the password and logoff the managed account: upon expiry of the grace period, the managed account password will be reset and any interactive logon sessions using the managed account will terminated. (Default) |
| Reset the password and reboot: upon expiry of the grace period, the managed account password will be reset and the managed device will be immediately rebooted. |
| Reset the password, logoff the managed account, and terminate any remaining processes: upon expiration of the grace period, the managed account password is reset, any interactive logon sessions using the managed account are logged off, and any remaining processes are terminated. |
- Post Authentication Delay: Use this setting to specify the amount of time, in hours, to wait after an authentication before executing the configured post-authentication actions. If this setting is not specified, it defaults to 24 hours. The minimum allowed value is 0 hours, which disables all post-authentication actions, and the maximum allowed value is 24 hours.
Below are the new settings recently added to the LAPS configuration settings page. Previously, these were configured using OMA-URI. These options allow you to create and manage a local administrator account directly within the LAPS policy, eliminating the need to create the account separately. You simply provide the account name, and LAPS will create and manage it for you (supported on Windows 11 24H2 or later).
I have written a detailed guide on automatic account management using OMA-URI. I recommend configuring Automatic Account Management directly in the LAPS policy UI, although OMA-URI remains a valid option. These settings are self-explanatory, and I will not explain each one here, as they are already covered in my Automatic Account Management with LAPS post. If you get stuck, refer to that guide for a detailed explanation of the settings below.
- Automatic Account Management Enabled
- Automatic Account Management Enable Account
- Automatic Account Management Randomize Name
- Automatic Account Management Target
- Automatic Account Management Name or Prefix
- Scope tags (optional): A scope tag in Intune is an RBAC label that you assign to resources such as policies, apps, and devices to control which administrators can view and manage them. For more information, see How to use scope tags in Intune.
- Assignments: Assign the policy to Microsoft Entra security groups that include the target Windows devices. As a best practice, start with a small pilot group, and once validated, expand the assignment more broadly. For guidance on assignment strategy, see Intune assignments: User groups vs. Device groups.
- Review + create: Review the deployment summary and click Create.
Sync Intune Policies
The device check-in process might not begin immediately. If you’re testing this policy on a test device, you can manually kickstart Intune sync from the device itself or remotely through the Intune admin center.
Alternatively, you can use PowerShell to force the Intune sync on Windows devices. Restarting the device is another way to trigger the Intune device check-in process.
Step 3: Validate LAPS Deployment on a Device
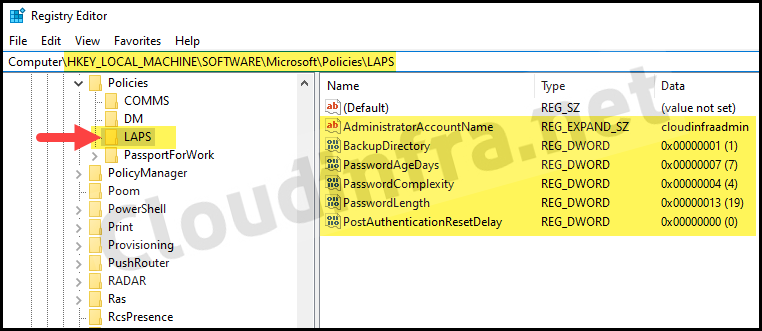
After Windows LAPS policy is successfully deployed to the target devices, it creates the LAPS registry keys under HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Policies\LAPS location, and the registry entries align with the policy settings configured in Intune.
Windows LAPS uses a background task that runs every hour to check whether the password has expired. If the password is expired, LAPS resets it and backs up the new password to Entra ID or to the configured backup location, based on the Backup Directory setting.
Note
You’ll find that Intune has created the following registry entries as per our LAPS policy.
- AdministratorAccountName: cloudinfraadmin
- BackupDirectory: 1
- PasswordAgeDays: 7
- PasswordComplexity: 4
- PasswordLength: 19
- PostAuthenticationResetDelay: 0
Retrieve Windows LAPS Managed Local Admin Password
Password retrieval differs depending on where you back up the password. If you have backed up the password in Entra ID, you can retrieve it either from Intune admin center, Entra admin center, or by using PowerShell. To read the password, you will need the microsoft.directory/deviceLocalCredentials/password/read permission. For metadata, you will need microsoft.directory/deviceLocalCredentials/standard/read permission (explained later). If BackupDirectory is on-premises Active Directory, Intune cannot show the password in the admin center when the password is backed up to on-prem AD. You must retrieve it via AD tools/workflows.
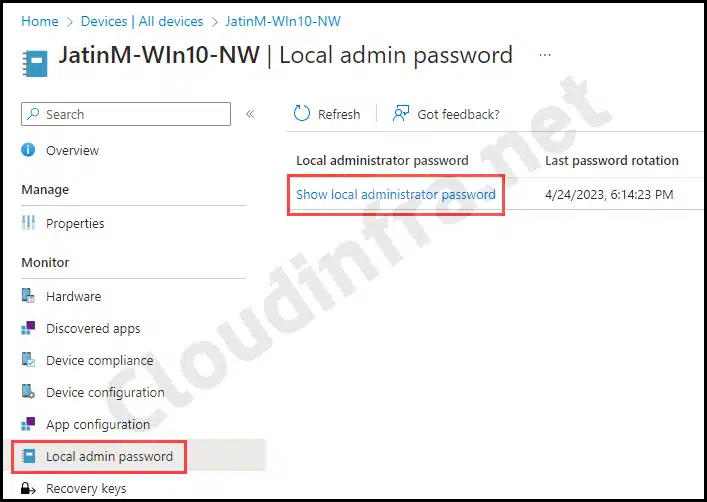
1. Retrieve Local admin password from Intune admin center
To retrieve the password from Intune admin center, follow below steps:
- Sign in to the Intune admin center > Devices > All devices.
- Click on the device that is targeted by the Windows LAPS policy.
- On the left-hand side, under Monitor, find the Local admin password option.
- Then click on Show local administrator password.
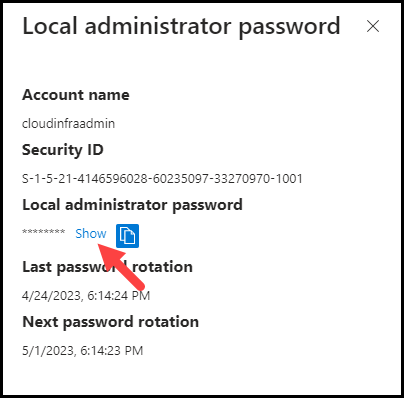
- You can click on Show to check the password in plain text.
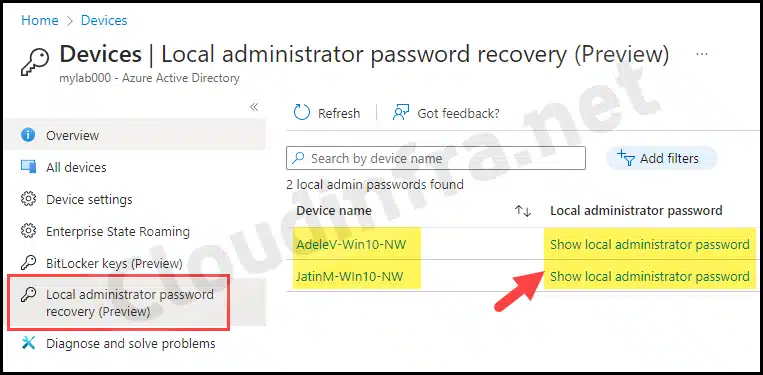
2. Retrieve Local admin password from Entra admin center
You can also retrieve the managed local admin password from Entra admin center. Follow below steps:
- Sign in to the Entra admin center > Expand Entra ID > Devices > All devices.
- On the left-hand side, under Manage, click Local administrator password recovery, and then select Show local administrator password for the device. Alternatively, you can open the specific device object under the All devices blade and select Local administrator password to view the password.
3. Retrieve Managed Local admin password using Powershell
Another method to retrieve the password of a local admin account is by using PowerShell. You can utilize the Get-LapsAADPassword PowerShell cmdlet by first connecting to Graph. This method requires an entra app registration and permission to retrieve passwords. Refer to this link: Manage Windows LAPS Using PowerShell for a step-by-step guide on managing Windows LAPS using PowerShell and retrieving local admin passwords for any device.
Windows LAPS Events in the Event Viewer
All Windows LAPS operations are monitored, and events are stored in the Windows Event Log. You can find these events in the dedicated LAPS folder. Open the Event viewer > Applications and Services Logs > Microsoft > Windows > LAPS > Operational. Processing starts at 10003 and ends at 10004. Failures log 10005. For more information, refer to the link: Windows LAPS troubleshooting guidance – Windows Server | Microsoft Learn.
- Event ID 10003: Background policy processing start log (Log: LAPS policy processing is now starting.)
- Event ID 10004: LAPS policy processing success. (Log: LAPS policy processing succeeded.)
- Event ID 10005: Laps policy processing failed. Error code 80070032.
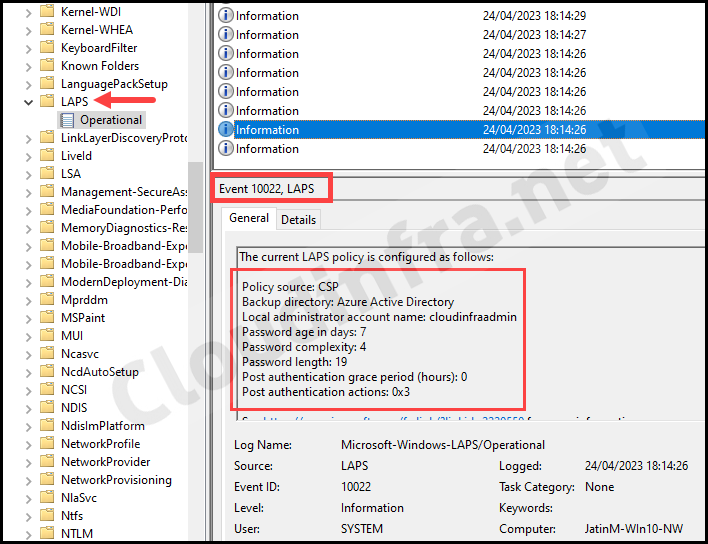
- Event ID 10022: Information about current LAPS policy.
Manage Windows LAPS using Powershell
You can also manage Windows LAPS using PowerShell. This allows you to check device information, view password expiry dates, and retrieve the password of the managed local administrator account in plain text. For more information, refer to this step-by-step guide: Manage Windows LAPS Using PowerShell.
Rotate Local admin password using Windows LAPS
Since the local admin user account has full control over your device, its password must be strong and regularly rotated or changed. This practice adds an extra layer of security, making it more challenging for unauthorized users to access the device. To learn about different methods to rotate the local admin user account password, refer to the post: 4 Ways to Rotate Local Admin Password Using Intune.
Permissions Required to Access Local Admin Password
If you’re unable to access the Local Admin Password option for a device on the Intune admin center because it’s greyed out, you have two options:
- Grant Rotate Local Admin Password permission to the user from the Intune admin center.
- Create a custom Entra ID role that allows you to view and retrieve local admin passwords for devices.
1. Rotate local admin password permission on Intune
To assign the Rotate local Admin password permission to any user, follow the below steps:
- Sign in to the Intune admin center > Tenant Administration > Roles
- Click on + Create to create a new custom Intune role.
- Provide a name and description of the custom role. For example:
- Name: Rotate local administrator password.
- Description: This role will enable the rotation of the local admin password.
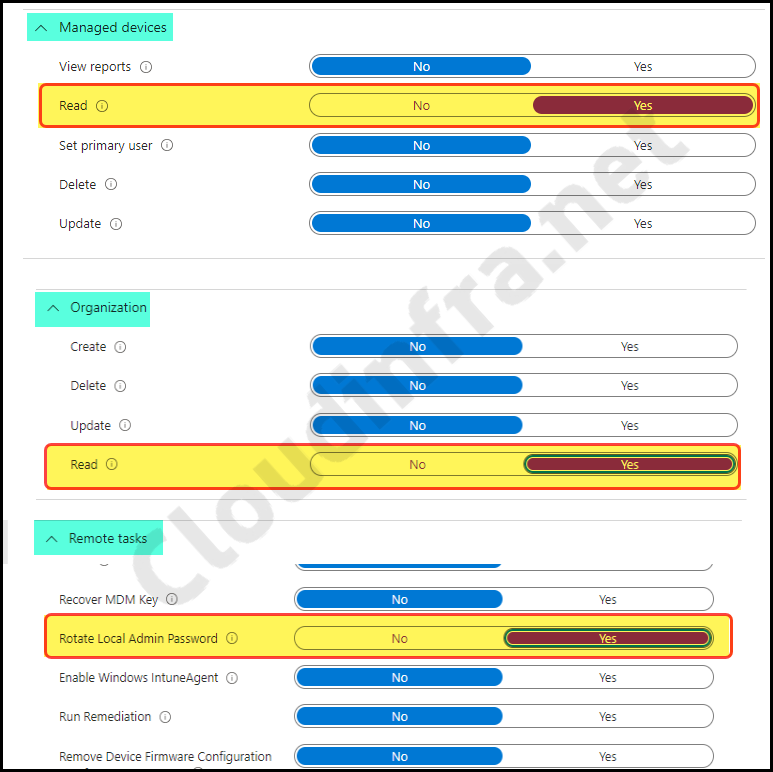
- In the Permissions tab, set up the following permissions:
- Managed Devices: Read
- Organization: Read
- Rotate Local admin password: Yes
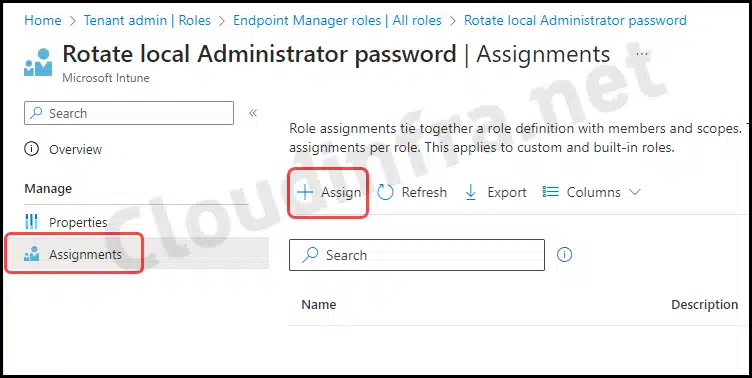
- After creating this role, find it under All roles. Click on it to open, and then select Assignments under Manage. Click on + Assign to assign this role to your helpdesk team and other admins.
2. Create a Custom Entra ID role
The built-in Entra ID roles, including Cloud Device Administrator, Intune Administrator, and Global Administrator, automatically grant the device.LocalCredentials.Read.All permission. If a user is a member of these built-in roles, they can manage the local administrator password for any device. If a user isn’t a member of any of these built-in roles but still needs to view the local admin password of devices, you must create a custom Entra ID role and assign the following permissions to this role.
- microsoft.directory/deviceLocalCredentials/password/read
- microsoft.directory/deviceLocalCredentials/standard/read
Step to Create a Custom Entra ID role
- Sign in to the Entra admin center > Expand Entra ID > Roles & admins > All roles.
- Click on + New custom role.
- Provide a name and description and keep baseline permissions as Start from scratch.
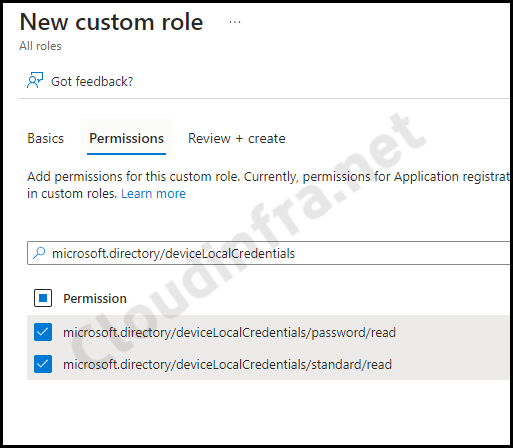
- Under the Permissions tab, select two permissions below:
- microsoft.directory/deviceLocalCredentials/password/read
- microsoft.directory/deviceLocalCredentials/standard/read
Next, create a custom Entra role. Click on the custom role, and then add either eligible assignments or active assignments to grant users access to retrieve the local admin password of Intune-managed devices.
On-prem Active Directory backup (Optional)
Use this only when you require on-prem AD as the password escrow location.
AD prerequisites
- AD schema includes Windows LAPS attributes (use
Update-LapsADSchema). - Computers have permission to write their own LAPS attributes (delegate with Set-LapsADComputerSelfPermission)
- Your password readers group has permission to read the password attribute (delegate with Set-LapsADReadPasswordPermission).
Steps:
- Extend schema (one time per forest).
- Delegate write permissions to the OU containing managed devices.
- Delegate read permissions to a dedicated AD group for password recovery.
- In Intune LAPS policy, set BackupDirectory to Active Directory.
Conclusion
Windows LAPS with Intune is a clean, Microsoft-supported approach to securing local administrator access by enforcing strong credential policies, backing up secrets to the correct directory (Entra ID or on-prem AD), and rotating passwords automatically and on demand.
For a smooth rollout, start the deployment on a pilot device group, use Microsoft-documented RBAC (custom Intune role for rotation and Entra permissions for password recovery), and validate behavior using the LAPS Operational event log and the CSP registry location. With these controls in place, you get both a stronger endpoint security posture and a practical, auditable helpdesk recovery workflow.

To have a custom local admin account, you point to using OMA-URI in another post.
Wouldn’t the OMA-URI override the password set by LAPS?
Or am I missing something?
@Dave – It may override the password set in OMA-URI. I have not tested that scenario. But if you want to create a local user account without defining any password then you could use Powershell scripts to create a local user account and add it to Administrators group. I have written another blog post on this which shows how to create a local user account without setting any password. Her’s the blog post link:
https://cloudinfra.net/create-a-local-admin-using-intune-and-powershell/
Hi,
What happens in the background when you ‘Enable Azure AD Local Administrator Password Solution’ under device settings? I would like to test this for a group before turning it on globally – im going to use intune to push policy for it. I suspect that enabling this under device settings just turns on the feature in Azure, but if you don’t have any policies in intune, nothing happens with the end users. is it true?
Thanks.
Hi Erik, I don’t think anything actually happens on the target device until you create LAPS policy and target to the devices. This is just to enable the feature on the tenant level so that you can create the policy in Intune.
Hello! After setting up Windows LAPS in Intune for AADJ devices and creating an accompanying policy to enable the built-in Administrator account, I’m now getting an error where the UAC prompt says “the user’s password must be changed before logging on the first time.” The event log shows no errors and the following is the policy shown in Event 10022, LAPS:
Password age in days: 7
Password complexity: 4
Password length: 14
Post authentication grace period (hours): 24
Post authentication actions: 0x3
Do you have a solution for an Azure AD registered device to modify the password of a local admin account created via an OMA-URI?
Good afternoon, thanks for sharing this guide. It works very well. However, despite the fact that the new local account gets created using Custom OMA-URI settings, the report returns only errors. Does the same happens to you? Many thanks
Yes, That’s a known issue.