In this guide, I will show you how to manage Windows LAPS using PowerShell. Windows Local Administrator Password Solution (Windows LAPS) is a built-in Windows capability that automatically manages and backs up the password of a local administrator account. In enterprise environments, Windows LAPS significantly reduces lateral movement risk by ensuring each device has a unique, regularly rotated local admin password and by centralizing recovery via Microsoft Entra ID, Intune, or Active Directory, depending on your chosen backup target.
This guide focuses on working, supportable PowerShell methods to (1) retrieve Windows LAPS credentials (metadata and passwords) and (2) trigger password rotation, with security and least-privilege recommendations aligned to Microsoft guidance. Use either the delegated sign-in approach or the application permissions approach for an automated workflow. I have demonstrated both these options in this post.
With Intune service release 2507 (July 2025), LAPS for macOS is now available. Setup and configure macOS LAPS via Intune admin center using this step-by-step guide: Setup and Configure LAPS for macOS via Intune.
Contents
Supported scenarios
Before you start, confirm where the password is being backed up, Microsoft Entra ID or on-premises Active Directory, as the commands used to retrieve the password differ based on the backup location.
- Microsoft Entra ID backup: Use Get-LapsAADPassword.
- Windows Server Active Directory backup (domain-joined or hybrid scenarios): Use Get-LapsADPassword (queries AD).
For Password Rotation:
- Rotate password locally: Use Reset-LapsPassword and optionally Invoke-LapsPolicyProcessing.
- Rotate password remotely: Use Intune “Rotate local admin password” permission or Graph rotateLocalAdminPassword.
Prerequisites
You must meet below requirements before proceeding to the steps for managing LAPS with PowerShell.
- Windows LAPS is enabled and configured: If you back up password to Microsoft Entra ID, Windows LAPS must be enabled at the tenant level in Entra device settings, and devices must be configured to back up local admin password to Entra ID.
- Permissions and roles for Entra ID password recovery: To read the password, you will need the microsoft.directory/deviceLocalCredentials/password/read permission. For metadata, you will need microsoft.directory/deviceLocalCredentials/standard/read permission. Read more: #step-to-create-a-custom-entra-id-role.
- PowerShell modules requirements:
Get-LapsAADPasswordis implemented as a wrapper around the Microsoft Graph PowerShell library, which must be installed for the cmdlet to work. Install Graph PowerShell using: Install-Module Microsoft.Graph -Scope CurrentUser.
3 Ways of Retrieving Password of Local Admin Account
There are three ways to retrieve the password of a managed local administrator account. In this post, I will focus on retrieving the password of a managed local administrator account by using PowerShell. For the other methods, refer to Setup Windows LAPS with Intune guide, which explains how to retrieve the password using the Intune admin center (option 1) and Microsoft Entra ID (option 2).
- Using Intune admin center
- Using Entra admin center
- Using PowerShell
Method 1: Retrieve Windows LAPS password from Entra ID
This is the recommended PowerShell approach for Entra-backed Windows LAPS local admin password because Microsoft provides a first-party cmdlet Get-LapsAADPassword that abstracts the underlying Microsoft Graph queries.
Step 1: Connect to Microsoft Graph (delegated sign-in)
For most organizations, the simplest and most supportable approach is delegated sign-in using Graph PowerShell. Before using Connect-MgGraph, install Microsoft Graph PowerShell module on your device.
Install Microsoft Graph PowerShell module
Install-Module Microsoft.Graph -Scope AllUsers -AllowClobber -ForceConnect to Graph with required delegated permission scopes
Connect-MgGraph -Scopes "Device.Read.All","DeviceLocalCredential.Read.All"Use ReadBasic if you only want metadata (no password)
Connect-MgGraph -Scopes "Device.Read.All","DeviceLocalCredential.ReadBasic.All"We are using the Device.Read.All permission; this is because Get-LapsAADPassword -DeviceIds can accept device names, but Graph queries ultimately require device IDs. The cmdlet resolves names to IDs using an additional Graph query, which requires Device.Read.All.
Step 2: Retrieve password metadata only (no password)
After successfully establishing connection with Microsoft Graph PowerShell, run below commands to manage LAPS and retrieve information about the managed local administrator password. Replace the device name with the device you want to query. This mode aligns with the “metadata-only” scenario and requires DeviceLocalCredential.ReadBasic.All. This command will not output managed local administrator password.
PowerShell (Example)
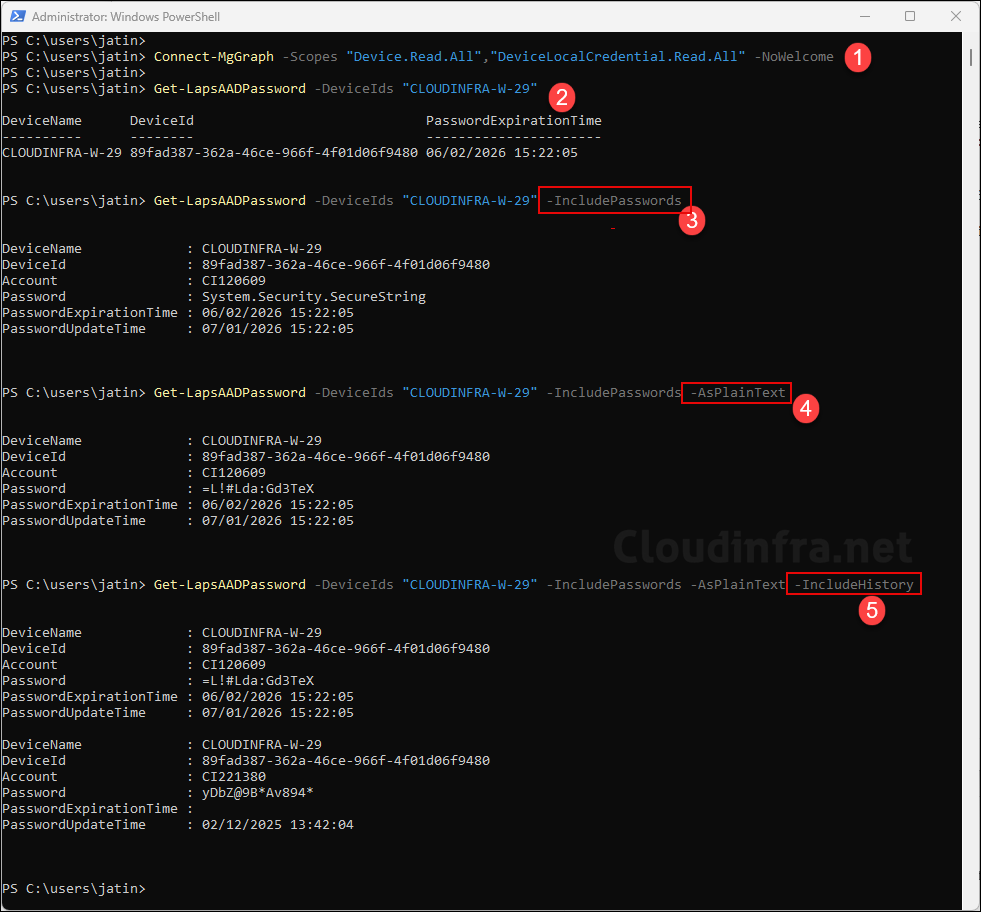
PS C:\users\jatin> Get-LapsAADPassword -DeviceIds "CLOUDINFRA-W-29"
DeviceName DeviceId PasswordExpirationTime
---------- -------- ----------------------
CLOUDINFRA-W-29 89fad387-362a-46ce-966f-4f01d06f9480 06/02/2026 15:22:05Step 3: Retrieve the password (SecureString by default)
PowerShell (Example)
PS C:\users\jatin> Get-LapsAADPassword -DeviceIds "CLOUDINFRA-W-29" -IncludePasswords
DeviceName : CLOUDINFRA-W-29
DeviceId : 89fad387-362a-46ce-966f-4f01d06f9480
Account : CI120609
Password : System.Security.SecureString
PasswordExpirationTime : 06/02/2026 15:22:05
PasswordUpdateTime : 07/01/2026 15:22:05
Step 4: Retrieve the password in clear text
PowerShell (Example)
PS C:\users\jatin> Get-LapsAADPassword -DeviceIds "CLOUDINFRA-W-29" -IncludePasswords -AsPlainText
DeviceName : CLOUDINFRA-W-29
DeviceId : 89fad387-362a-46ce-966f-4f01d06f9480
Account : CI120609
Password : =L!#Lda:Gd3TeX
PasswordExpirationTime : 06/02/2026 15:22:05
PasswordUpdateTime : 07/01/2026 15:22:05
Step 5: Retrieve password history
PowerShell (Example)
PS C:\users\jatin> Get-LapsAADPassword -DeviceIds "CLOUDINFRA-W-29" -IncludePasswords -AsPlainText -IncludeHistory
DeviceName : CLOUDINFRA-W-29
DeviceId : 89fad387-362a-46ce-966f-4f01d06f9480
Account : CI120609
Password : =L!#Lda:Gd3TeX
PasswordExpirationTime : 06/02/2026 15:22:05
PasswordUpdateTime : 07/01/2026 15:22:05
DeviceName : CLOUDINFRA-W-29
DeviceId : 89fad387-362a-46ce-966f-4f01d06f9480
Account : CI221380
Password : yDbZ@9B*Av894*
PasswordExpirationTime :
PasswordUpdateTime : 02/12/2025 13:42:04
Step 6: Bulk query devices and export metadata
Use the script below to query all devices where LAPS is enabled and export password metadata per device, such as password expiration time, along with the device ID. Collect the device names in C:\Temp\laps-devices.txt file and then run the script. The CSV output file will be created at the C:\Temp\laps-metadata.csv location. The CSV file will not contain managed local administrator password information.
Get_LAPS_meta_data.ps1
# Read device names or device IDs from a text file (one per line)
$devices = Get-Content "C:\Temp\laps-devices.txt"
# Query LAPS metadata for each device
$result = foreach ($d in $devices) {
try {
$r = Get-LapsAADPassword -DeviceIds $d -ErrorAction Stop
[pscustomobject]@{
DeviceInput = $d
DeviceName = $r.DeviceName
DeviceId = $r.DeviceId
PasswordExpirationTime = $r.PasswordExpirationTime
Error = $null
}
}
catch {
[pscustomobject]@{
DeviceInput = $d
DeviceName = $null
DeviceId = $null
PasswordExpirationTime = $null
Error = $_.Exception.Message
}
}
}
# Export results to CSV
$result | Export-Csv "C:\Temp\laps-metadata.csv" -NoTypeInformation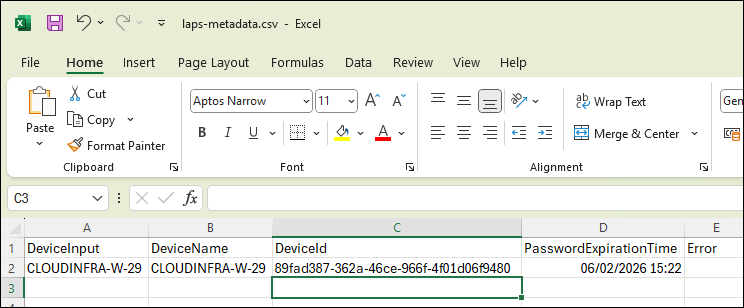
Method 2: Retrieve Windows LAPS password from Active Directory
If your Windows LAPS policy backs up passwords to Windows Server Active Directory, use Get-LapsADPassword. This cmdlet supports clear-text and encrypted storage, and it can automatically decrypt encrypted LAPS passwords when the caller is authorized.
Step 1: Query the current password (SecureString)
Get-LapsADPassword -Identity "CLOUDINFRA-W-29"Step 2: Query the current password in clear text
Get-LapsADPassword -Identity "CLOUDINFRA-W-29" -AsPlainTextStep 3: Include password history (if enabled)
Get-LapsADPassword -Identity "CLOUDINFRA-W-29" -AsPlainText -IncludeHistoryMethod 3: Using Application Permissions
In the first method, we used delegated sign-in permissions to establish a connection with Microsoft Graph PowerShell and retrieve information about the managed local administrator account. In this method, I will show you how to use application permissions to connect to Microsoft Graph, which is required for automated workflows.
I will first create an app registration in Entra ID and assign the required API permissions, and then use the application ID and tenant ID to connect to Microsoft Graph. After creating the application in Entra ID, you must grant the following API permissions so the app can read device information and the managed local administrator password. These are the same permissions we used when connecting to Microsoft Graph PowerShell with the delegated sign-in method.
- Device.Read.All
- Provide either DeviceLocalCredential.Read.All (to read the password) or DeviceLocalCredential.ReadBasic.All (to read just the metadata like password expiration but not the password).
Step 1: Create an Entra App
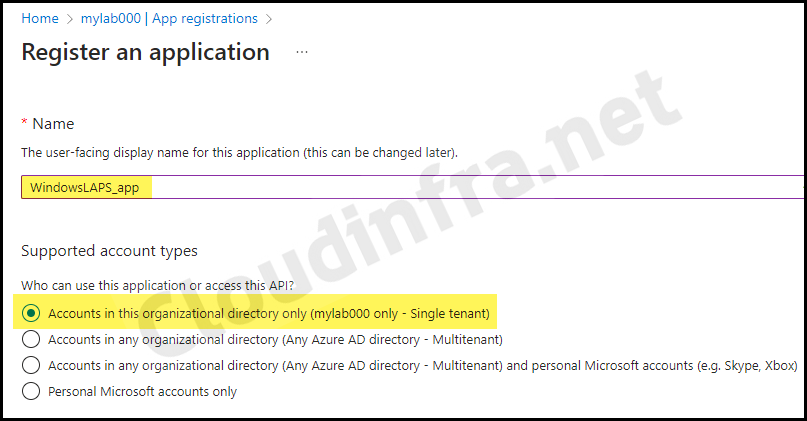
- Sign in to the Entra admin center > Expand Entra ID > App registrations.
- Click + New registration, enter WindowsLAPS_app as the app name (you can use a different name if you prefer), and then click Register.
Step 2: Assign permissions to the Entra App
After registering the app, the next step is to grant the required permissions.
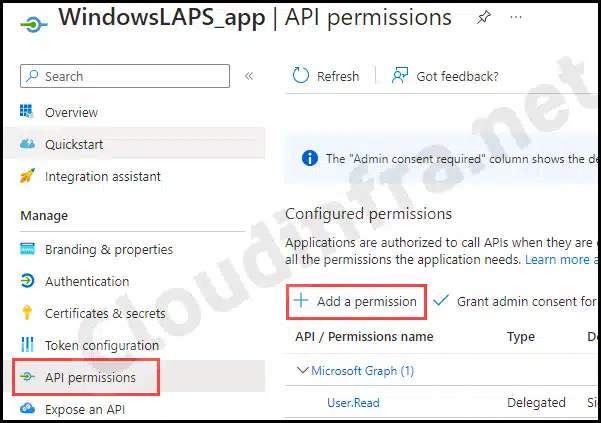
- Open the Entra ID app WindowsLAPS_app.
- Go to API Permissions under Manage.
- Then click on + Add a permission.
- Under Microsoft APIs > Click on Microsoft Graph.
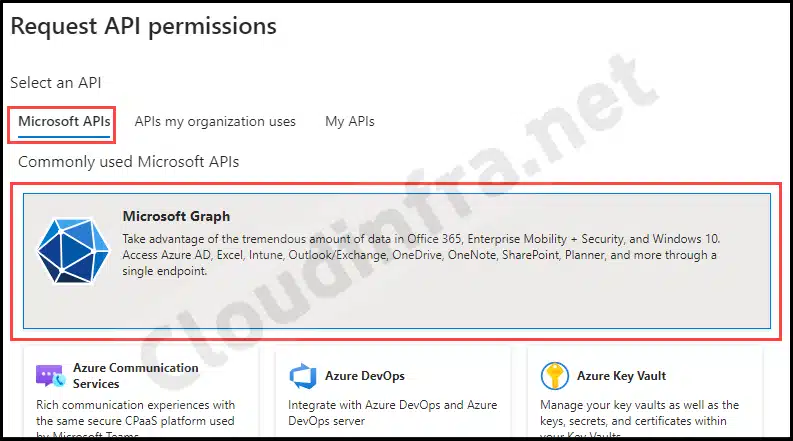
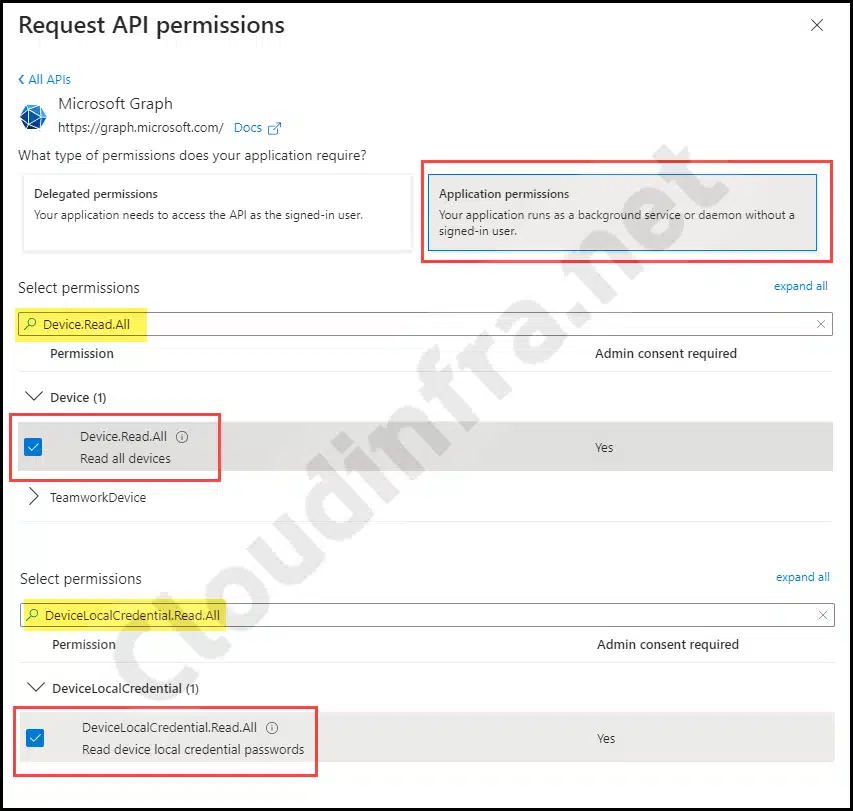
- Under Application permissions. Search for Device.Read.All and select this permission.
- Next, search for either DeviceLocalCredential.Read.All, and select this permission.
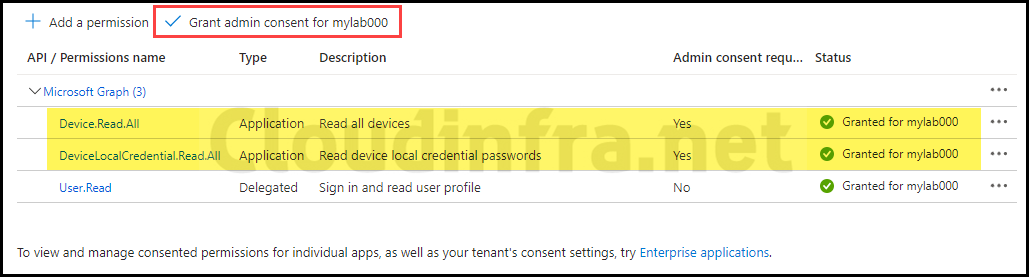
- Make sure to grant admin consent for the assigned API permissions. The status should be displayed as green with a check once admin consent has been granted.
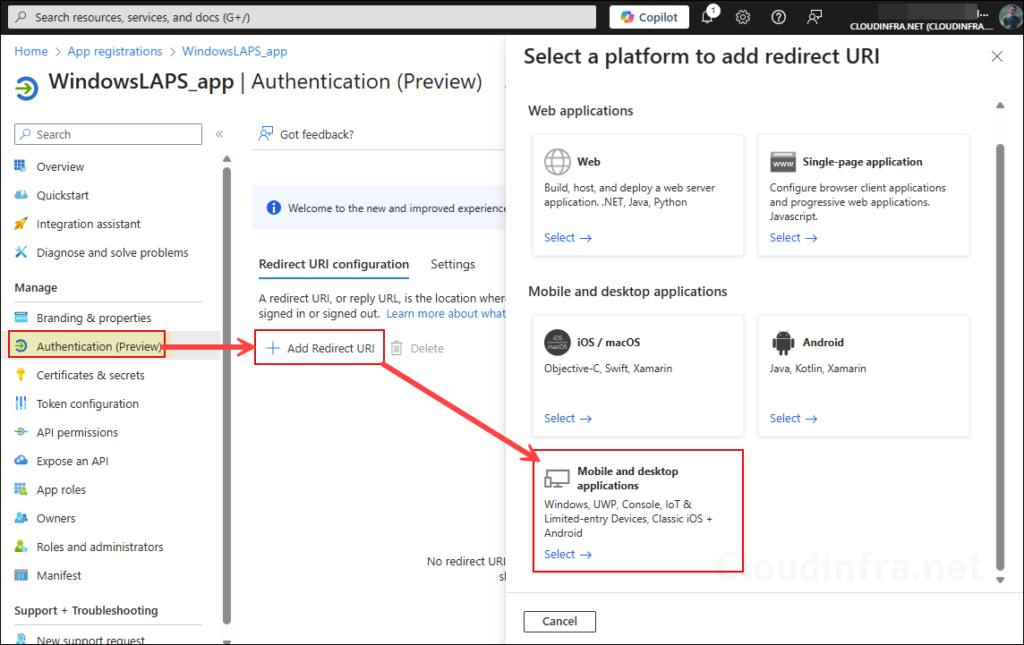
- Open the app WindowsLAPS_app and then click on Authentication under Manage. Click on + Add Redirect URI and then click on Mobile and Desktop applications.
- Add Custom Redirect URIs as http://localhost. Select the checkbox for https://login.microsoftonline.com/common/oauth2/nativeclient, and click Configure.
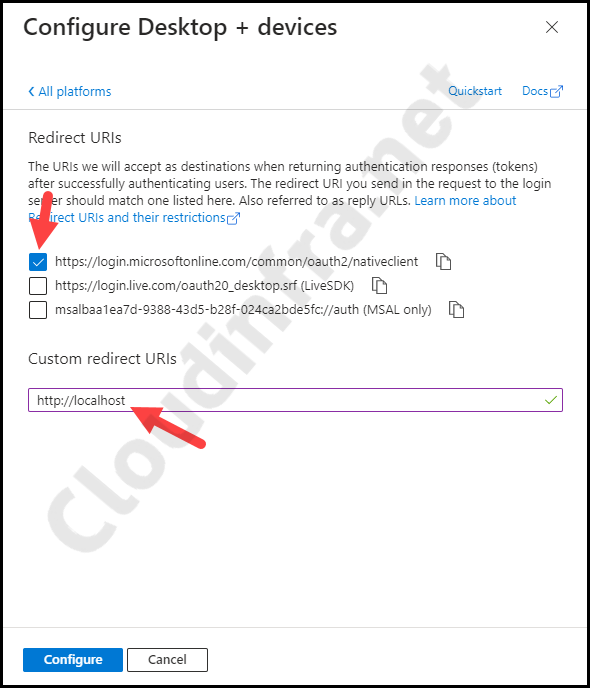
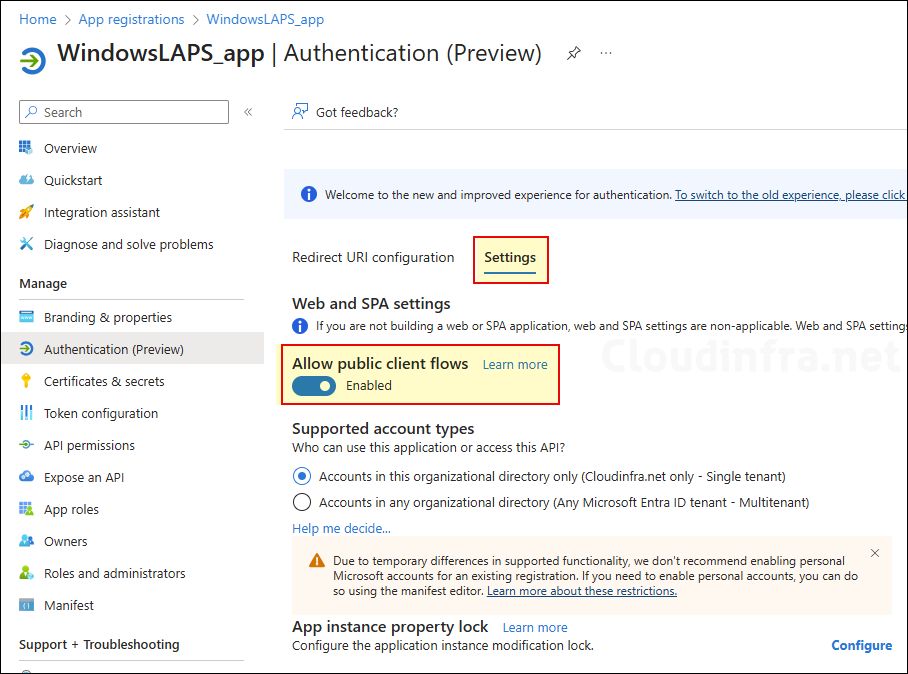
- Under the Settings tab, enable Allow Public client flows toggle switch and click Save.
Step 3: Install and Connect with Microsoft Graph PowerShell
Now that the Entra app has been created and configured, we will use it to establish a connection with Microsoft Graph PowerShell. First, install the Microsoft Graph PowerShell module if it is not already installed, and then connect to Microsoft Graph by using Connect-MgGraph.
Install Microsoft Graph PowerShell Module
Install-Module Microsoft.Graph -Scope AllUsers -AllowClobber -Force
Now, use the Connect-MgGraph PowerShell cmdlet to establish the connection. For this, you will require the client ID of the application and tenant ID values.
- Client ID: Click on the app, go to the Overview tab, and copy the Application (client) ID.
- Tenant ID: Sign in to the Entra admin center > Expand Entra ID > Overview. Copy the tenant ID value.
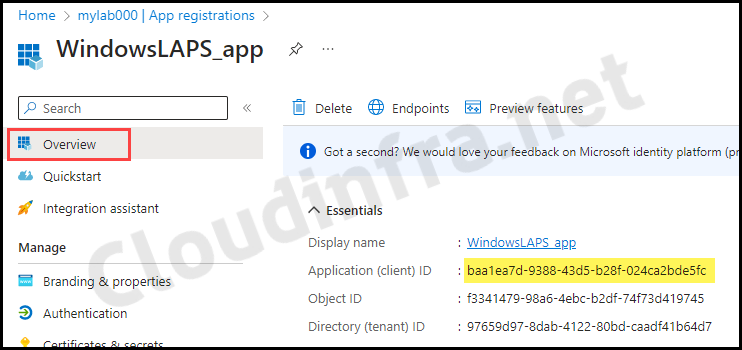
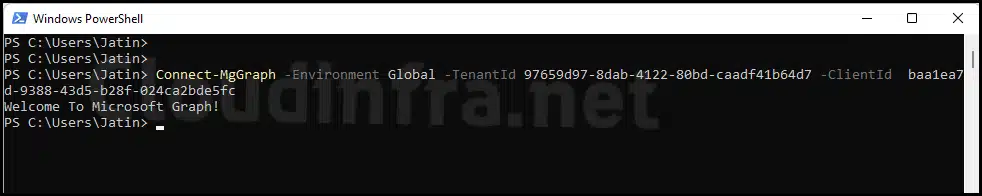
Connect-MgGraph
Connect-MgGraph -Environment Global -TenantId 97659d97-8dab-4122-80bd-caadf41b64d7 -ClientId baa1ea7d-9388-43d5-b28f-024ca2bde5fc
If you get a pop-up similar to below, select Consent on behalf of your organization, then click Accept button to proceed.
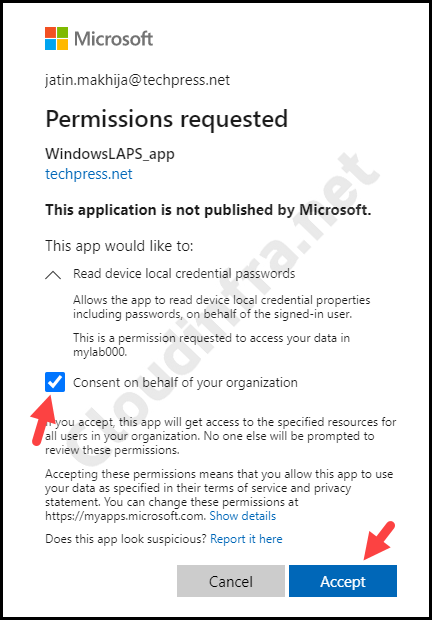
Once you are connected successfully, you will see a message: Welcome to Microsoft Graph! on the PowerShell console.
Step 4: Retrieve local admin password using Get-LapsAADPassword
After you have successfully established the connection using Microsoft Graph PowerShell, the remaining commands for managing LAPS passwords are the same as those used with delegated sign-in permissions. The only difference is that, in this case, application permissions are used instead of delegated sign-in permissions.
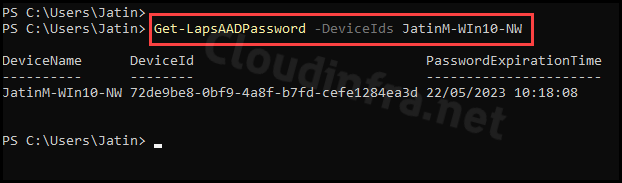
Get-LapsAADPassword
Get-LapsAADPassword -DeviceIds JatinM-WIn10-NW
Retrieve managed local admin password
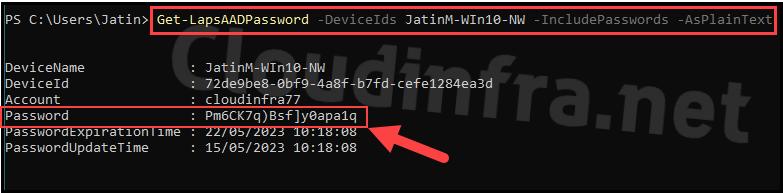
Get-LapsAADPassword -DeviceIds JatinM-WIn10-NW -IncludePasswords -AsPlainText
Reset Managed Local Administrator password
Use Reset-LapsPassword cmdlet to reset the password of a managed local administrator password.
Rotate local admin password using Windows LAPS
Since the local admin user account has full control over your device, its password must be strong and regularly rotated or changed. This practice adds an extra layer of security, making it more challenging for unauthorized users to access the device. To learn about different methods to rotate the local admin user account password, refer to the post: 4 Ways to Rotate Local Admin Password Using Intune.
Troubleshooting
You may encounter issues when managing LAPS using PowerShell. Below are some common errors you might see and how to resolve them.
Issue 1: Access denied or insufficient privileges Get-LapsAADPassword
This is almost always a permissions issue:
- For reading the metadata: ensure DeviceLocalCredential.ReadBasic.All.
- For retrieving the password: ensure DeviceLocalCredential.Read.All.
- If using device names, ensure Device.Read.All for name-to-ID resolution.
Issue 2: Cmdlet fails when using device name
If duplicate device names exist in the tenant, Get-LapsAADPassword cmdlet may fail. Use the device ID instead.
Issue 3: You cannot see the LAPS password in Intune or Entra portals
- Enable Windows LAPS in Entra device settings.
- Confirm your LAPS policy backs up to Entra ID.
- Confirm your role assignment includes the below permissions. Refer to this link for more information: #2-create-a-custom-entra-id-role.
- microsoft.directory/deviceLocalCredentials/password/read
- microsoft.directory/deviceLocalCredentials/standard/read
Issue 4: Can we recover a password for a device deleted from Entra ID?
No. Microsoft explicitly confirms that when a device is deleted in Entra ID, the LAPS credential tied to that device is lost, and there is no built-in recovery method. If you have operational needs that require historical recovery, the correct approach is prevention: avoid deleting devices until you have validated you do not need their recovery artifacts (for example, BitLocker keys, and in this case, LAPS passwords).
Issue 5: Need diagnostics for device-side LAPS behavior
Use Get-LapsDiagnostics and enable verbose logging where supported to gather device-side diagnostic data for investigation.
Conclusion
PowerShell is a first-class way to operate Windows LAPS at scale. Use Get-LapsAADPassword for Entra-backed credentials (with Graph permissions), Get-LapsADPassword for AD-backed credentials, and rotate passwords either locally with Reset-LapsPassword or remotely via Intune and Microsoft Graph where operationally required.

Is there a way by which we can retrieve LAPS password for device which is deleted from Entra?