In this post, I will show you the steps to create a local admin account using Intune. You can easily create and manage local admin accounts on your Windows devices through Intune admin center. If you need to add an existing Azure AD/Entra ID user account to the local admin group, refer to the guide Add a User to Local admin group using Intune.
- To create a local admin account on macOS via Intune, refer to this guide: Create a Local admin account on macOS using Intune.
- To configure a local admin account on Windows 365, refer to this guide: Elevate User to Local Admin on Windows 365 Cloud PC.
For demonstration purposes, I will create a local administrator account named cloudinfraadmin. However, you can create a local administrator user account using any name you prefer.
If you are using Windows LAPS, you can use the automatic account management policy CSP settings to create and manage the local administrator account. These automatic account management settings are now configured directly from the LAPS configuration UI in Intune. For more details, refer to this post: Setup Windows LAPS with Intune: A Comprehensive Guide.
You can also use OMA-URI settings to configure automatic account management. For more information, refer to Automatic Account Management in Windows LAPS.
Note
Contents
Methods to Create a Local Admin Account using Intune
Below are three different methods to create a local administrator account using Intune on Windows 10 or Windows 11 devices. In the next sections of this post, I will walk through the implementation steps for Method 1. For Methods 2 and 3, use the links to the posts provided below.
- Method 1 (Direct creation): Accounts CSP via OMA-URI creates the local user and optionally adds it to the local Administrators group.
- Method 2: Endpoint security account protection (local user group membership). Refer to the post for detailed steps: Add a User to Local Admin group using Intune.
- Method 3: Proactive Remediation or standalone PowerShell script. Refer to the post for detailed steps Create a Local Admin Using Intune and PowerShell.
If you want to delete a local user account using Intune, refer to the post How to Delete a Local User Account Using Intune.
Create a local admin account using Intune
This is the Method 1, which uses Accounts CSP to create a local user and join it to a local group. The node LocalUserGroup can be set to 2 to add the account to the local Administrators group. An important point to note is that when you deploy this policy from Intune, the Password setting can report as failed even though it has been applied successfully. Let’s go through the steps to create a local admin account via Intune:
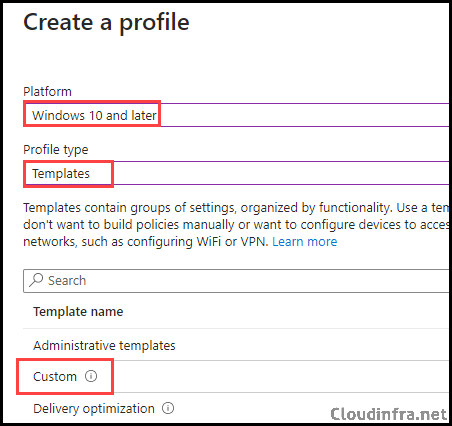
- Sign in to the Intune Admin Center > Devices > Configuration > + Create > New Policy.
- Select Platform type as Windows 10 and later. Select Profile type as Templates.
- Select Template Name as Custom and click on Create.
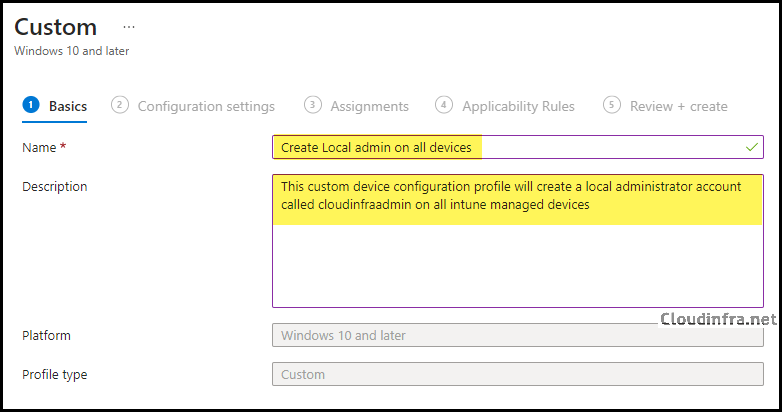
- On the Basics tab, provide a name and description of the policy. Click Next.
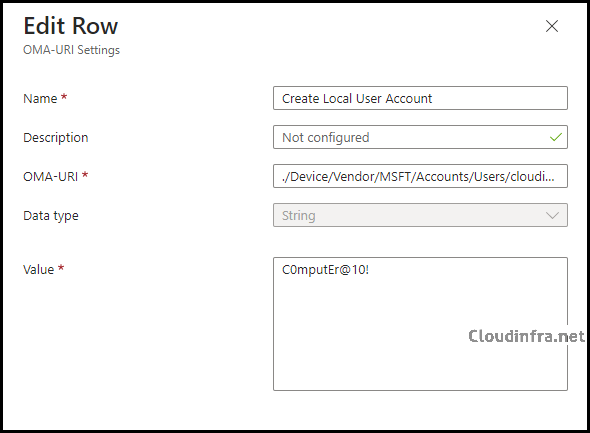
- On the Configuration settings tab, click Add to add the OMA-URI settings, and then configure the following OMA-URI entries. Replace cloudinfraadmin with any other name to create a local user account as per your requirement. For example, if you replace cloudinfraadmin with myadminacc, a local user account named myadminacc will be created.
| Name | OMA-URI | Data type | Value |
|---|---|---|---|
| Create Local User Account | ./Device/Vendor/MSFT/Accounts/Users/cloudinfraadmin/Password | String | C0mputEr@10! |
| Add user to local administrator group | ./Device/Vendor/MSFT/Accounts/Users/cloudinfraadmin/LocalUserGroup | Integer | 2 |
- There is a 20 character limit for usernames.
- Special characters may need escaping in XML-style contexts (
&,<,>).Note
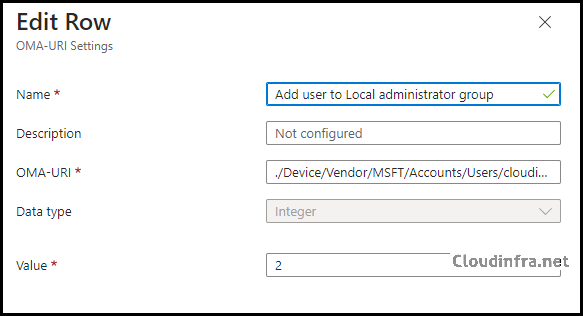
- Scope tags (optional): A scope tag in Intune is an RBAC label that you assign to resources such as policies, apps, and devices to control which administrators can view and manage them. For more information, see How to use scope tags in Intune.
- Assignments: Assign the policy to Microsoft Entra security groups that include the target users or devices. As a best practice, start with a small pilot group, and once validated, expand the assignment more broadly. For guidance on assignment strategy, see Intune assignments: User groups vs. device groups.
- Applicability Rules: You can set up rules on this page to target specific versions or OS editions.
- Review + create: Review the deployment summary and click Create.
Monitor Policy Deployment Progress
- Sign in to the Intune admin center > Devices > Configuration.
- Choose the Device Configuration profile you want to work with, and at the top of the page, you’ll see a quick view of the Success, Failure, Conflict, Not Applicable, and In Progress status.
- Click on View report to access more detailed information.
Sync Intune Policies
The device check-in process might not begin immediately. If you’re testing this policy on a test device, you can manually kickstart the Intune sync from the device itself or remotely through the Intune admin center.
Alternatively, you can use PowerShell to force the Intune sync on Windows devices. Restarting the device is another way to trigger the Intune device check-in process.
End User Experience
After the policy is deployed successfully, check the end user’s device. Confirm if a local user account has been created and added to the local administrator’s group.
- Click on Start and search for Computer Management.
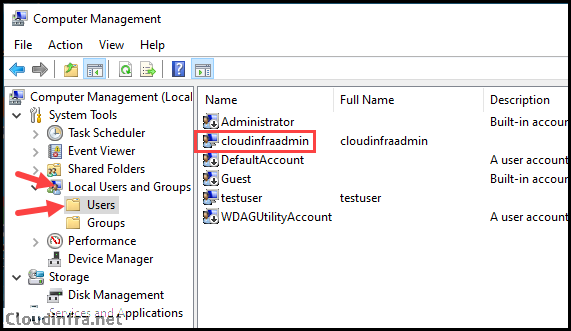
- Click on Local Users and Groups > Users and find the local user account created by Intune policy, which is cloudinfraadmin in our scenario.
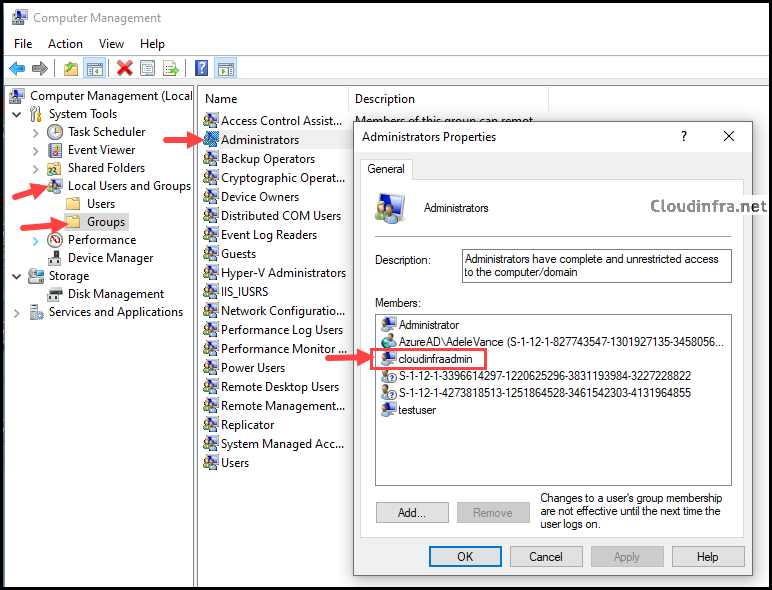
- Next, ensure the account is added to the Administrators group, granting local admin privileges. Go to Computer Management > Local Users and Groups > Groups > Administrators and check if your local user account is listed within the Administrators group.
You can also run the commands below to quickly verify that the configured account has been created and added to the local Administrators group. Open PowerShell as an administrator and execute the commands, replacing the account name in the commands with the one you created.
Get-LocalUser -Name "cloudinfraadmin" net localgroup administrators
Set Local User Account Password to Never Expire Using Intune
To set the local user account’s password expiry to Never on target devices, deploy a PowerShell script with the given command. For step-by-step instructions on deploying PowerShell scripts via Intune, refer to the blog post titled How to Deploy a PowerShell Script Using Intune.
Set-LocalUser -Name "cloudinfraadmin" -PasswordNeverExpires 1
Troubleshooting
- Password OMA-URI shows “Failed” in Intune: This is a known behavior for the Accounts CSP Password node in some deployments from Intune. Validate locally on the device rather than relying only on portal status.
- Local group membership is inconsistent or conflicting: Do not mix older RestrictedGroups policy and LocalUsersAndGroups on the same device. Microsoft explicitly warns this is unsupported and can lead to unpredictable results.
- Entra group does not work when added to Administrators: For Entra groups via LocalUsersAndGroups, you need to use group SID (not the group name).
Conclusion
If you need to create a dedicated local admin account using Intune, Accounts CSP provides a direct OMA-URI method to create the user and add it to the Administrators group. But you should be aware that password deployment can report as failed even when applied. For membership management and ongoing control, Microsoft’s recommended approach in Intune is Endpoint security > Account protection > Local user group membership, which uses Policy CSP: LocalUsersAndGroups and should be your default for managing the Administrators group at scale.

What OMA-URI would we use if we dont want it to have a password associated with it because Windows LAPS will set the random password?
In that case, you can try creating a local user using a Powershell script:
PS C:\> New-LocalUser -Name “localuser01” -Description “Description of this account.” -NoPassword
Using that would they be part of the Administrators group?
Hello dj56, I have created a blog post which shows how you can create a local user account without password using Intune. You will have to use Proactive remediations to create local user account.
Then add that account to local administrators group using Local user group membership option.
https://cloudinfra.net/create-a-local-admin-using-intune-and-powershell/
Isn’t using OMA-URI settings for creating or managing accounts the OLD method? Why can’t Intune admins use the Endpoint Security -> Account Protection -> Local user group membership templates instead?
Yes, you can use that as well. Please create the local user account first before updating Administrator group.
Cool stuff.
Tried this and it worked a treat
This CSP always works but shows error 0x87d1fde8. Any ideas?
Hi Jeff,
Same issue for me as well. The config applies but I experience the same error for both settings.
I have been doing additional digging. Here’s some information that may help.
Blog: https://call4cloud.nl/2021/12/i-kill-remediation-errors/
MS: https://learn.microsoft.com/en-us/windows/client-management/mdm/accounts-csp
“Supported operation is Add and the GET operation is not supported. When you have configured this setting from the Endpoint Manager it will report as failed when deployed.”
Any ideas as to why the profile shows errors on config profile?
Setting Name Setting Status Errorcode
Create LAdmin [./Device/Vendor/MSFT/Accounts/Users/hmadmin/Password] Error -2016281112
AddLAGroup ./Device/Vendor/MSFT/Accounts/Users/cloudinfraadmin/LocalUserGroup Error -2016281112
The account is created successfully and added to the local admin group.
Thank you,
Yes, even though it error’s out, the account is still created and added to local admin group. This could be due to the password which Intune is probably not able to verify and confirm if the profile deployment is successful.
If you want to use another way to deploy local user account and add it to local admin, you can also use Intune Proactive remediations and Local user group membership option. I have written a blog post on this to provide the scripts and step by step guide: https://cloudinfra.net/create-a-local-admin-using-intune-and-powershell/
A recent change in Intune requires E3 or better licensing to use Proactive Remediations. It is no longer available to those with M365 Business Premium, which unfortunately cuts off many non-profits and SMBs.
Hi, what if you want to delete a local user? The MS documentation teaches you how to remove it from specific groups but not remove it from the Users part of Local Users and Groups.
You can delete a local user account using Intune Proactive remediations. Here’s is a blog post which provides step by step guide along with powershell scripts to delete a local user account using Intune.
https://cloudinfra.net/how-to-delete-a-local-user-account-using-intune/
Am I correct in assuming that the password created in this process is a ‘one and done’ deployment in that it creates the account, sets the password and then leaves it? There wouldn’t be any issues with having another policy, lets say Windows LAPS since someone else mentioned it, changing the password?
Also for the password, Are we able to use the serial number in the password by using “%SERIAL%” or {{serialnumber}} as used with Account SCP or in certain areas of Intune?
I am also looking for an answer on Windows LAPS and would this be affected by the CSP policy?
Hi Jatin,
Thanks for the article.
Just wondering how do we create the local account without forcing it to change password at first logon? Because the creation of the local account and adding it to admin groups works well, it’s just that when we use it for the first time for anything that requires elevation, it says the account needs to change password first.
Hello Shawn, You can follow below article which provides the steps to disable “User must Change password at next logon” flag using intune https://cloudinfra.net/enable-disable-user-must-change-password-at-next-logon-using-intune/
Question: Why does this show errors, but create the account.
My best guess is that Intune could not verify the local user account password. I am not 100% sure on this yet. You can Ignore the error, or else use Intune remediations or Powershell script to create a Local admin user. I may reach out to Microsoft to get some answers.
I know this is a relatively older post but I’ve run it and while the account get’s created in Administrator’s group, it’s also created in the Users group. Any idea why that would happen?
Hi Jamie, As it creates a local user and adds it to the local administrator group, you will find it showing under the Local Users and Groups > Users folder and then gets added to the Groups > Administrators group.
Hi Jatin, so the account is being added to both the Groups > Administrators group and the Groups > Users group (the one noting that members can’t make changes), that then won’t allow the account’s admin function to work regardless of the membership in the Admins group, but I can’t figure out why it added it to both.
This worked perfectly for what I needed!! Thank you so much!