In this blog post, I will show you the steps to fix a Win32 app deployment error: Application was not Detected Intune Error 0x87D1041C. This error is generally caused by an Incorrect detection rule specified during the creation of the Win32 application deployment from Intune. As you’re aware, the purpose of the detection rule is to identify the application’s presence. If the detection rule isn’t configured accurately, it may fail to detect the application despite it being installed correctly.
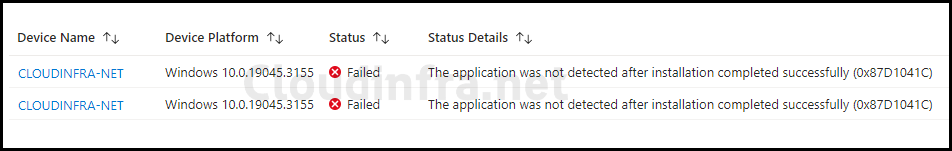
Despite successful deployment via Intune, you may encounter error code 0x87D1041C in the Intune admin center. For example, I deployed an app called Notepad++, which was deployed successfully, but I observed this error when checking its deployment status on Intune.

The screenshot below shows that the Application Status has failed, and Status Details provide further Information about the Error code.
Contents
Fix Intune Error code 0x87D1041C
As we already know, the most common reason for this error is that Intune is not able to detect the application using the configured Detection rule in Win32 App deployment. Therefore, the only way to fix it is to check the Detection rule configured for the App and ensure it’s correct.
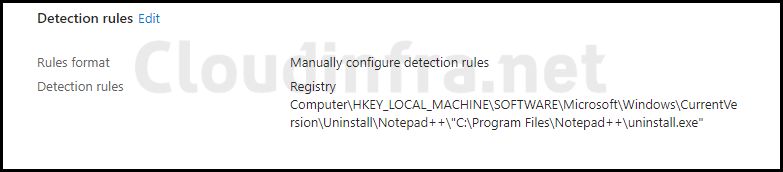
Example of a Misconfigured rule
Below is an example of a misconfigured rule for the application Notepad++. The Detection rule shown in the screenshot below was unable to detect the presence of Notepad++ after deployment. Therefore, even though the app was installed successfully, it was reported as a failure.
Update Detection Rule
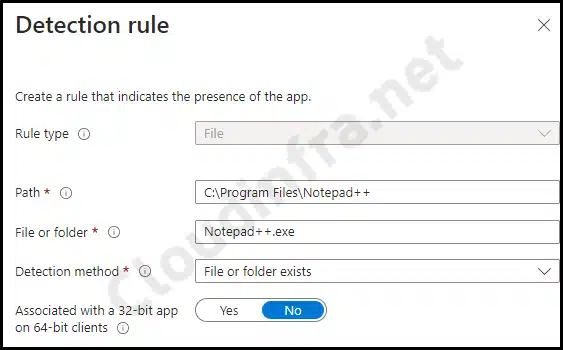
To fix this error, we’ve updated the Win32 App deployment’s detection rule. We are now using file-based detection to verify the existence of Notepad++.exe under C:\Program Files\Notepad++. If the file Notepad++.exe is found, it will confirm the application’s successful installation, preventing unnecessary re-deployment.
It’s important to clarify that we previously used a Registry-based detection logic, and we’ve now moved to a File-based detection logic. This change doesn’t necessarily indicate that file-based detection is superior to registry-based detection; it primarily highlights the issue with the existing detection logic, which failed to identify the application.
Regardless of the Detection Rule type chosen, the key question is, Can it accurately detect the presence of the deployed application?
The screenshot below displays the revised Detection logic for our Notepad++ application.
More Information
If you’d like to investigate this error further, the subsequent sections of this blog post offer further insights.
applicationDetected: False
Although error code 0x87D1041C clearly indicates the issue’s cause, you can gain further insights by examining the IntuneManagementExtension.log file on one of the target devices. There, you may find an applicationDetected: False error.
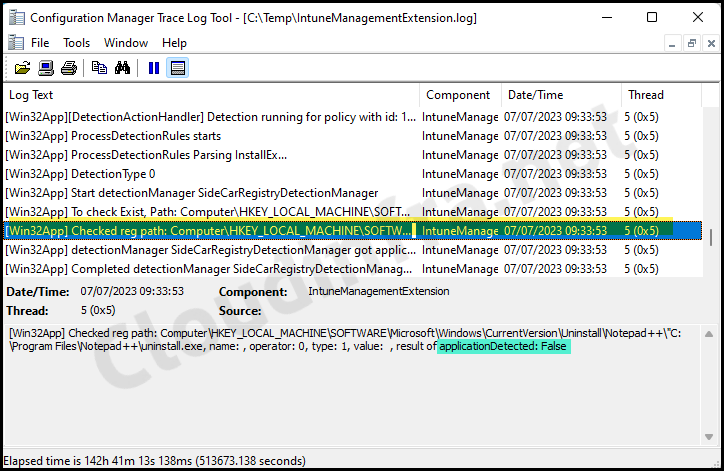
Here’s an excerpt related to this app deployment from the Intune Management Extension log file. The log file reveals that the Detection logic is unable to identify the application, leading to the application deployment status reporting failure.
[Win32App][DetectionActionHandler] Handler invoked for 1 app detections. IntuneManagementExtension 07/07/2023 09:33:53 5 (0x0005) [Win32App][DetectionActionHandler] Detection running for policy with id: 19de19a9-71a2-462a-942f-86aaec859ea1. IntuneManagementExtension 07/07/2023 09:33:53 5 (0x0005) [Win32App] ProcessDetectionRules starts IntuneManagementExtension 07/07/2023 09:33:53 5 (0x0005) [Win32App] ProcessDetectionRules Parsing InstallEx… IntuneManagementExtension 07/07/2023 09:33:53 5 (0x0005) [Win32App] DetectionType 0 IntuneManagementExtension 07/07/2023 09:33:53 5 (0x0005) [Win32App] Start detectionManager SideCarRegistryDetectionManager IntuneManagementExtension 07/07/2023 09:33:53 5 (0x0005) [Win32App] To check Exist, Path: Computer\HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Uninstall\Notepad++\”C:\Program Files\Notepad++\uninstall.exe, valueName: applicationDetected: False IntuneManagementExtension 07/07/2023 09:33:53 5 (0x0005) [Win32App] Checked reg path: Computer\HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Uninstall\Notepad++\”C:\Program Files\Notepad++\uninstall.exe, name: , operator: 0, type: 1, value: , result of applicationDetected: False IntuneManagementExtension 07/07/2023 09:33:53 5 (0x0005) [Win32App] detectionManager SideCarRegistryDetectionManager got applicationDetectedByCurrentRule: False as system IntuneManagementExtension 07/07/2023 09:33:53 5 (0x0005) [Win32App] Completed detectionManager SideCarRegistryDetectionManager, applicationDetectedByCurrentRule: False IntuneManagementExtension 07/07/2023 09:33:53 5 (0x0005) [Win32App][DetectionActionHandler] Detection for policy with id: 19de19a9-71a2-462a-942f-86aaec859ea1 resulted in action status: Success and detection state: NotDetected. IntuneManagementExtension 07/07/2023 09:33:53 5 (0x0005).
Excerpt from IntuneManagementExtension.log
To access the Intune Management Extension log file, follow these steps:
- Navigate to C:\ProgramData\Microsoft\IntuneManagementExtension\Logs your computer.
- Look for the most recent version of the IntuneManagementExtension.log file.
- The recommended tool for viewing this log file is CMTrace.
Conclusion
As demonstrated in this blog post, resolving error code 0x87D1041C, which stems from misconfigured detection logic in Win32 app deployments, can be straightforward. Several types of detection logic are available, including MSI, File, and Registry. Regardless of the chosen detection logic type, the critical factor is its ability to detect the application accurately. Properly configured detection logic is key to a successful deployment.

Couldn’t detect app because it was manually updated after installation or uninstalled by the user.while deployin mozilla firefox 50.1.0 rxe
Thank you for this detailed post! I was troubleshooting the Intune error 0x87D1041C for days, and your insights about checking the application assignments really helped narrow down the issue. Keep up the great work!